|
Friday, November 30, 2007
|
|
|
Tuesday, November 27, 2007
|
|

The team over at US-CERT has posted some
workarounds such as disabling the QuickTime ActiveX Controls, blocking RTSP. If you do the registry changes, make sure you revert them once you have installed the coming patch or else you won't be able to view any streaming QuickTime media.
Additional Notes: Symantec has some excellent analysis located
here. They found that this exploit crashes the ActiveX Control in IE. Firefox on the other hand may pass off the QuickTime request directly to QuickTime player depending on configuration. So Firefox users may therefore be more vulnerable, not because of the browser itself, but because Firefox will deliver the exploit directly to its most optimal platform.
Also, while this exploit allows remote code execution and is potentially quite severe, it's not yet being implemented in the wild. There is however a very good chance of that changing as QuickTime is one of a growing number of popular third-party applications targeted by the bad guys.
|
Monday, November 26, 2007
|
|
|
Wednesday, November 21, 2007
|
|
|
Tuesday, November 20, 2007
|
|
|
Friday, November 16, 2007
|
|
|
Thursday, November 15, 2007
|
|
|
Wednesday, November 14, 2007
|
|
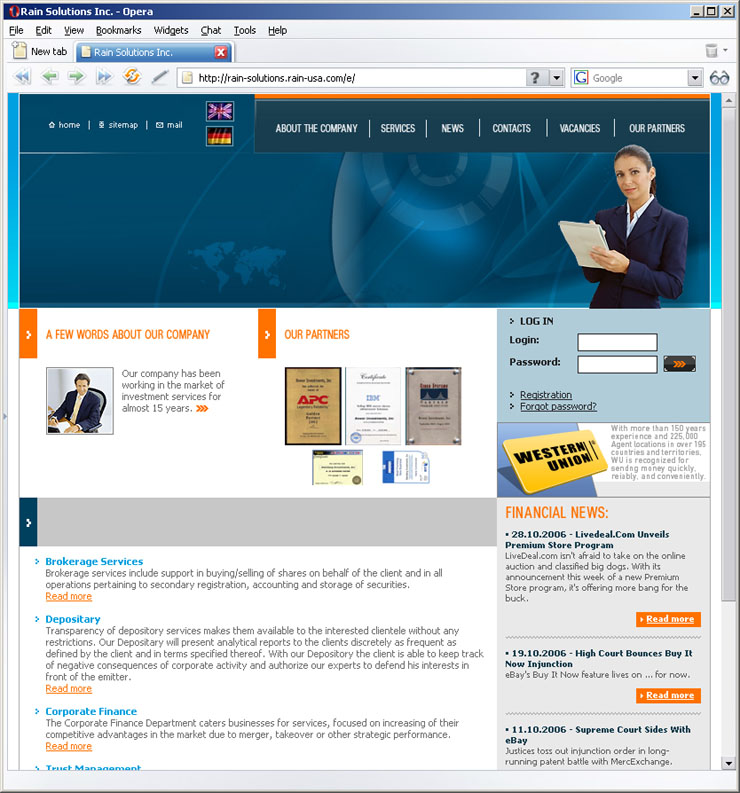
Click image for animation.
Money mules are very often unsuspecting people getting tricked into helping out in money laundry schemes. They receive stolen money into their accounts, withdraw it in cash, and then transfer it to the bad guys by using some more anonymous service, such as Western Union. When authorities look into these cases the trail will always lead to the money mule, not the people behind the crime. We see these cases pretty frequently but it's not that often that a site gets hacked and used to host the mule site.
The same site design is also available on:
http://www.calisto-trading.org
http://www.simple-investments.org
An excellent catch by Bob over at
Bobbear.co.uk.
Rain is quite popular in Asia and has even been spoofed by Steven Colbert in the USA:
http://en.wikipedia.org/wiki/Rain_(singer)While we're on the topic, if you haven't seen it yet, check out the Weblog's challenge post:
https://www.f-secure.com/weblog/archives/00001314.htmlUpdated to Add: Rain Solutions is still online. That's the difficult nature of these fraud sties.
Here's how the front page of the legitimate site appears:

|
Tuesday, November 13, 2007
|
|

However, don't let your guard down as the vulnerabilities can enable remote code execution and DNS spoofing. Affected applications are IE7 for MS07-061 and all Windows servers for MS07-062.
Complete info and patch download links available from
Microsoft's Web site.
Keep your systems updated, using updates from the original site.
|
Monday, November 12, 2007
|
|
The page, located on a .cn server, prompts for the installation of Adobe's Flash Player. If you download the file, it's named
install_flash_player.exe. Just as the real Flash Player download would be…
Firefox browser is already warning about the fraudulent nature of this site, and we have detection with our 2007-11-12_04 database, so we don't expect a very big catch for this particular rock phishing site.
|
Sunday, November 11, 2007
|
|
|
Thursday, November 8, 2007
|
|
|
Wednesday, November 7, 2007
|
|
|
Tuesday, November 6, 2007
|
|
| Android |
Posted by Mikko @ 12:21 GMT |
|

The interview, in English, is available from BNR's site:
BNR NieuwsradioDirect link:
MP3Topics discussed in the radio interview include the security of Windows Vista, "BundesTrojan", and if the Microsoft Update system is hackable or not.
|
Thursday, November 1, 2007
|
|
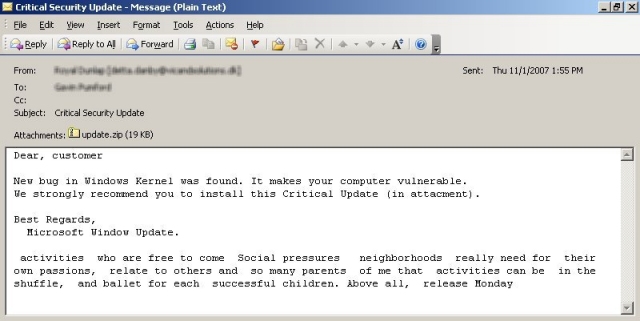
A short description of the trojan and a screenshot of the spammed message can be found
here.