|
Thursday, October 30, 2008
|
|

The ZIP file typically contains a file that looks like a document (.DOC) but it is really an EXE, there's just a lot of whitespaces between .DOC and .EXE.

Some of these ZIP files are protected by a password which makes it more likely to be allowed through an e-mail server. The password is always in the e-mail message so that the recipient can easily see it.
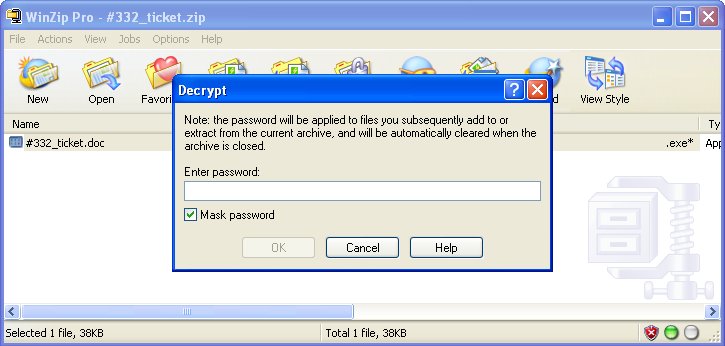
Using e-mail attachments has made a come back in popularity amongst malware writers during the last few months. We detect this latest batch as variants of the
Worm:W32/Autorun family.
|
Wednesday, October 29, 2008
|
|

The reason for the out-of-band patch is that there is already a trojan actively using the vulnerability to infect computers, which we detect as
Trojan-Spy:W32/Gimmiv.A. This trojan steals confidential information from the infected computer and sends it back to the attacker.
The situation is not as dire as in earlier years, as Windows XP SP2 and newer have a firewall in place by default. If you have file or printer sharing enabled however, your computer could be affected.
We recommend that everyone apply the
update as soon as possible.
|
Wednesday, October 22, 2008
|
|
|
Wednesday, October 15, 2008
|
|
|
Tuesday, October 14, 2008
|
|
|
Wednesday, October 8, 2008
|
|
- Mebroot is the most advanced and stealthiest malware seen so far
- It operates at the lowest level of the Windows operating system
- Mebroot writes its startup code to the first physical sector on the hard drive
- When an infected machine is started, Mebroot loads first and survives through the Windows boot
- Mebroot hides all changes made to the infected system
- It heavily uses undocumented features of Windows
- It creates a complex network communication system, involving pseudo random domain names
- Large parts of the code is highly obfuscated
- Mebroot uses a very complex installation mechanism, trying to bypass security products and to make automatic analysis harder
- All botnet communication is encrypted with advanced encryption mechanism
- The malware has apparently gone through extensive quality assurance. It never seems to crash the systems it infects, even though it runs at the kernel level
- The Mebroot gang has so far registered around 1000 com/net/biz domain names for their communication needs
- The botnet backdoor functionality is very powerful, even allowing the upload and execution of arbitrary kernel-mode modules
- As a payload, Mebroot attacks over 100 European online banks, trying to steal money as users do their online banking on infected machines
The authors of Mebroot remain unknown at this time. However, it's obvious they are well organized and well funded.
To download the slide set prepared by Kimmo and Elia, click on the image below.
Signing off,
MikkoP.S. This would seem like a great opportunity to plug another conference:
T2 will be held in Helsinki later this month and Kimmo will be talking there as well, on the
Evolution of Kernel-Mode Malware. The agenda as a whole looks very good,
take a look.
|
Wednesday, October 1, 2008
|
|