|
Wednesday, October 31, 2007
|
|
|
Tuesday, October 30, 2007
|
|

With an unpatched system, visiting the site will trigger an exploit to automatically download and execute a malicious file. The new filename is
halloween.exe. We already detect this as
Email-Worm.Win32.Zhelatin.LJThis may be a
Trick, and a bad
Threat from the Storm gang, so be sure to keep your databases updated.
|
Thursday, October 25, 2007
|
|

And it attempts to connect to www.kalonzomusyokaforpresident.com.

The website is the official presidential campaign page of Kenyan politician Stephen
Kalonzo Musyoka. He launched his presidential campaign on October 14, 2007. Kenyan elections will be held in December. Note that the malware quotes
Francis rather than Stephen.
Agent.DPL hacks the registry so that the user is unable to locate key Windows functions. This image shows the missing Control Panel icon as well as a few other things.

If any Control Panel apps are launched from another location, they'll be shut down by the malware.
Our guess is that by making the computer next to useless, Musyoka's detractors hope to shift the blame to him. But then again we don't know that much about the political situation in Kenya…
Our description —
Trojan:W32/Agent.DPL — provides additional details, including an unusually easy way to disable it.
|
Wednesday, October 24, 2007
|
|
|
Wednesday, October 17, 2007
|
|
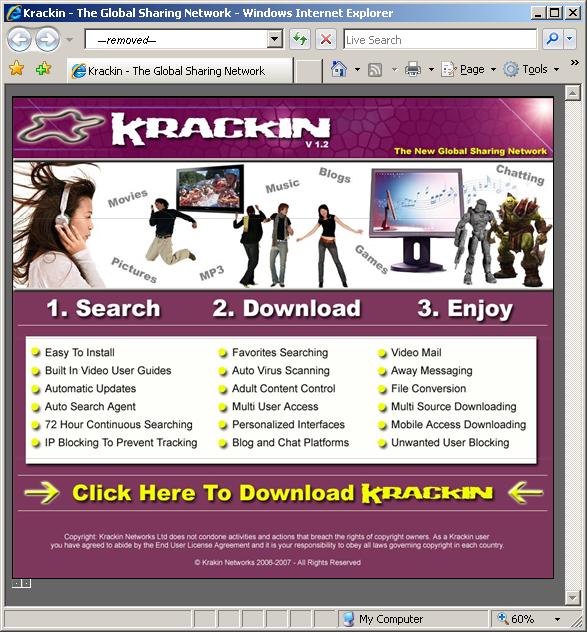
However, a mere visit to the site using an unpatched system will trigger an exploit to automatically download and execute a malicious file. Patched systems are protected but only if the users do not choose to download the file (with filename
krackin.exe) and execute it themselves.
The webpage is detected as
Trojan-Downloader.JS.Agent.KD while the file is detected as
Email-Worm.Win32.Zhelatin.KE.
This is one network you wouldn't want to join, so make sure to keep your databases updated.
|
Tuesday, October 16, 2007
|
|
|
Saturday, October 13, 2007
|
|
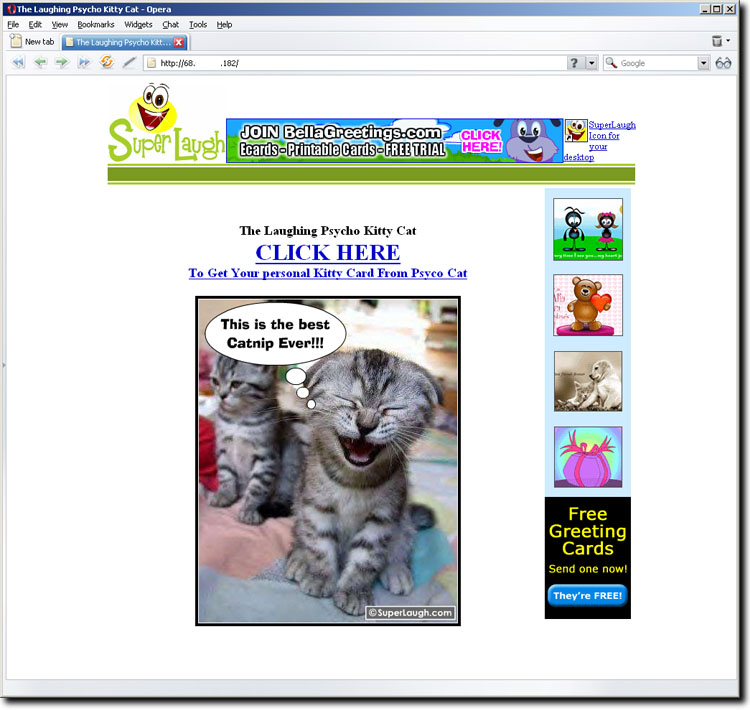
All the links points to
SuperLaugh.exe which we detect as
Email-Worm.Win32.Zhelatin.KI
|
Wednesday, October 10, 2007
|
|

These updates involve applications including Kodak Image Viewer, Outlook Express and Windows Mail, Internet Explorer, and a vulnerability in Microsoft Word. All of these could allow remote code execution and elevation of privileges. For more details on these updates, here's the link to
Microsoft's Security Bulletin.
BE SURE to update always!
|
Thursday, October 4, 2007
|
|