On the front page of the site a hidden
IFrame has indeed been inserted and it loads a URL from another website.
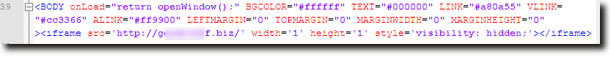
This file in turn uses three IFrames to load three other URLs.

Two of the URLs are now down but the third contains an obfuscated JavaScript that uses exploits to download and run a file called
loader.exe. This file is a small downloader which downloads additional files that are different password stealing trojans, additional downloaders, et cetera. We detect all of the malicious files with our latest database update.
Update: The malicious IFrame has been removed from the front page and it's now safe to visit the site again.
|
Wednesday, August 29, 2007
|
|

It is our belief that the MicroVault software hides this folder to somehow protect the fingerprint authentication from tampering and bypass. It is obvious that user fingerprints cannot be in a world writable file on the disk when we are talking about secure authentication. However, we feel that rootkit-like cloaking techniques are not the right way to go here. As with the Sony BMG case we, of course, contacted Sony before we decided to go public with the case. However, this time we received no reply from them.

It should be noted that MicroVaults with fingerprint authentication appear to be an older product and may no longer be manufactured. At least we had some trouble finding a reader of this type in Helsinki. Nevertheless, we did manage to find them on sale.
Note that over the weekend there was news about a
suspected rootkit in the PC version of the game Bioshock. This news proved not to be true, but since BioShock apparently uses copyright protection software made by Sony there was lots of initial commotion.


Subjects we've seen used in the e-mail messages so far are:
Cat Lovers
Dated Confirmation
Internal Support
Internal Verification
Login Info
Login Information
Login Verification
Member Confirm
Member Details
Member Registration
Membership Details
Membership Support
New Member Confirmation
New User Confirmation
New User Details
New User Letter
New User Support
Poker World
Registration Confirmation
Registration Details
Secure Registration
Tech Department
Thank You For Joining
User Info
User Verification
Your Member Info
Welcome New Member
Tech Support
Internet Tech SupportAnd the senders have been:
Bartenders guide
Bartenders Guide
Coolpics
Dog lovers
Entertaining pics
Entertaining pros
Fun World
Free ringtones
Free web tools
Game Connect
Internet Dating
Job search pros
Joke-a-day
Mobile Fun
MP3 world
Net gambler
Net-jokes
Online hook-up
Poker world
Resume Hunters
Ringtone heaven
Web
Web cooking
Web connects
Webtunes
Wine LoversOnce someone visits the website the text has changed a bit. Now it talks about that you need a Secure Login Applet to be able to use the service and the link points to
applet.exe which is of course the infected file.

Similar to previous attacks it also uses exploits in an attempt to automatically infect the user when you view the page –
so don't do it.
UPDATE: The spam runs of these e-mail messages continues and we've updated the list of subjects and senders used. Feel free to mail us if you've seen any others that we don't have on the list. Use the e-mail address listed at the
top of the page.
Thanks to everyone who has sent us updates on the subjects and senders used.
|
Saturday, August 18, 2007
|
|
|
Thursday, August 16, 2007
|
|
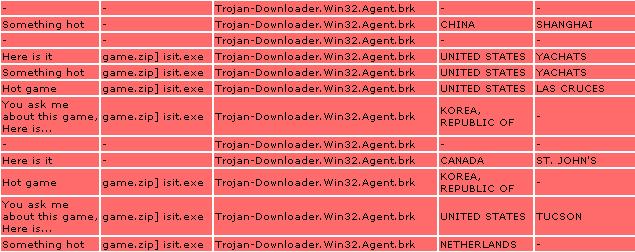
This time the e-mail attachment is
game.zip.
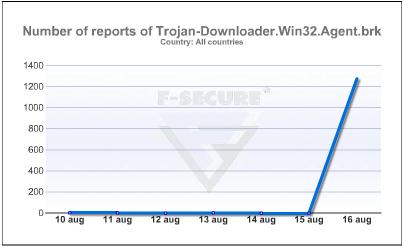
E-mail subjects are now related to games like the following:
Hot pictures
Hot game
Here is it
You ask me about this game, Here is it
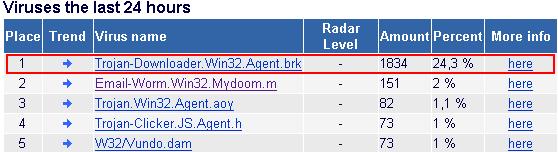
Something hotThe file was already detected by us before the spamming run started to increase in number.
Previous posts related to this can be seen
here and
here.
|
Wednesday, August 15, 2007
|
|

The updates resolve vulnerabilities found on several applications including Office Excel, Internet Explorer, and GDI. Most of these vulnerabilities allow remote code execution and one allows an elevation of privileges.
For more information as well as links for the actual patches, see
August's bulletin.
As always, it's good to perform a system update ASAP.
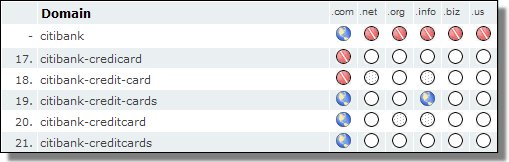
| Keyword | Number of Domains |
| citibank* | 497 |
| bankofamerica* | 407 |
| lloyds* | 994 |
| bnpparibas* | 41 |
| egold* | 691 |
| hsbc* | 1258 |
| chase* | 6470 |
| paypal* | 1634 |
| ebay* | 8057 |
And today?
August 2007| Keyword | Number of Domains
|
| citibank* | 810 |
| bankofamerica* | 656 |
| lloyds* | 1421 |
| bnpparibas* | 62 |
| egold* | 1304 |
| hsbc* | 1574 |
| chase* | 10153 |
| paypal* | 1653 |
| ebay* | 9120 |
Not all of these sites are bad, but there are definitely some needles in those haystacks.