|
Wednesday, April 29, 2009
|
|
| Estonia |
Posted by Mikko @ 19:51 GMT |
|
|
Wednesday, April 22, 2009
|
|
| Time | | IP |
| 11:00:17 | | 118.232.218.209 |
| 11:00:22 | | 211.105.220.204 |
| 11:00:28 | | 121.179.73.185 |
| 11:00:33 | | 124.8.89.29 |
| 11:00:38 | | 69.55.30.158 |
| 11:00:44 | | 116.127.184.49 |
| 11:00:49 | | 201.42.136.214 |
| 11:00:54 | | 89.35.18.27 |
| 11:01:00 | | 24.77.250.131 |
| 11:01:05 | | 118.130.83.202 |
| 11:01:11 | | 77.78.150.199 |
| 11:01:16 | | 211.180.118.70 |
| 11:01:21 | | 189.111.197.36 |
| 11:01:27 | | 121.183.32.80 |
| 11:01:32 | | 211.218.197.220 |
| 11:01:38 | | 121.183.32.80 |
| 11:01:43 | | 125.129.151.33 |
| 11:01:48 | | 151.60.88.70 |
| 11:01:54 | | 121.179.73.186 |
| 11:01:59 | | 210.207.217.154 |
And all those IP addresses are infected home computers, where the owner of the computer has no idea he's actually running a webserver — which is serving viruses.
This botnet is not just used to host the malware: the malware itself uses it when calling home. When Waledac is executed, it does dozens of HTTP posts to IP addresses belonging to this botnet.
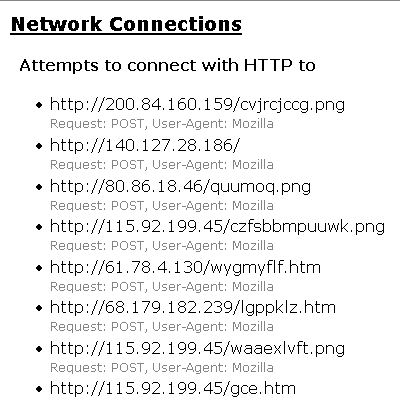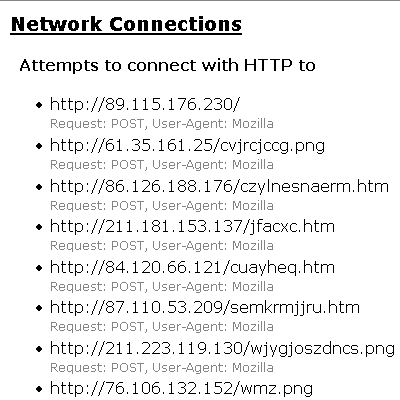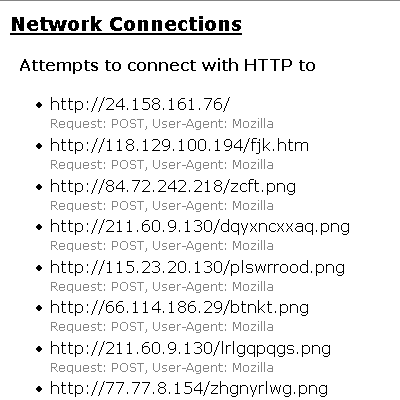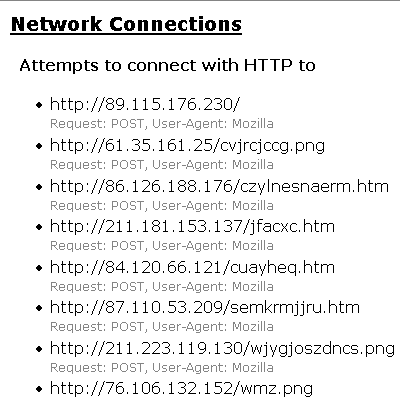
Waledac gang has registered over 100
.com domains for their purposes. You can actually tell a bit about their operations if you arrange their domains into groups. Practically all the domains they own are registered to these email addresses:
hanlin_425@126.com, lijian@qq.com and
wusong_ccc@126.com.
Here they are:
Newsbestgoodnews.com
bestbreakingfree.com
breakinggoodnews.com
breakingnewsltd.com
breakingkingnews.com
breakingnewsfm.com
easyworldnews.com
goodnewsreview.com
goodnewsdigital.com
reportradio.com
linkworldnews.com
tntbreakingnews.com
usabreakingnews.com
wapcitynews.com
worldtracknews.com
worldnewseye.com
worldnewsdot.com
worldtracknews.com
spacemynews.com
yourbreakingnew.com
Blogsbestusablog.com
bestjournalguide.com
bestlifeblog.com
bestblogdirect.com
boarddiary.com
blogsitedirect.com
blogginhell.com
farboards.com
mobilephotoblog.com
photoblogsite.com
Fear & Terroragainstfear.com
antiterroris.com
antiterroralliance.com
antiterrornetwork.com
fearalert.com
globalantiterror.com
terroralertstatus.com
terrorfear.com
terrorismfree.com
urbanfear.com
Coupons & Salesbestcouponfree.com
codecouponsite.com
gonesite.com
greatcouponclub.com
greatsalesgroup.com
greatsalestax.com
smartsalesgroup.com
thecoupondiscount.com
yourcountycoupon.com
Love & Sexadorelyric.com
adorepoem.com
adoresong.com
adoresongs.com
bestadore.com
bestlovehelp.com
bestlovelong.com
bluevalentineonline.com
chatloveonline.com
cherishletter.com
cherishpoems.com
extendedman.com
funloveonline.com
funnyvalentinessite.com
greatsvalentine.com
orldlovelife.com
greatvalentinepoems.com
lovecentralonline.com
lovelifeportal.com
romanticsloving.com
thevalentinelovers.com
whocherish.com
wirelessvalentineday.com
worldlovelife.com
worshiplove.com
youradore.com
yourgreatlove.com
yourlength.com
yourvalentineday.com
yourvalentinepoems.com
yourvalnetinepoems.com
And here are the latest additions:
SMS Spyingchinamobilesms.com
downloadfreesms.com
freecolorsms.com
freeservesms.com
miosmsclub.com
smsclubnet.com
smspianeta.com
virtualesms.com
This leaves us with a handful of domains we can't categorize to any of the above groups. They are:
batchoose.com
bayhousehotel.com
coralarm.com
longballonline.com
moneymedal.com
quickjust.com
soundroyal.com
yourbarrier.com
yourlol.com
yourwent.com
Maybe these domains could give us a hint on their next move?
Does anybody have any ideas? If so, leave us a
comment.
- On April 8th a new update was made available to Conficker.C infected machines via the P2P network
- The new file, which we call Conficker.E, was executed and co-existed alongside the old infection.
- It re-introduces spreading via the MS08-067 vulnerability. Spreading functionality was removed in Conficker.C and the gang behind this maybe realized they made a mistake and added it again.
- The new variant does not have the domain generation algorithm like the previous variants have
- There's a possible connection to Waledac, a spambot. Some Conficker.C infected computers connected to a well known Waledac domain and downloaded Waledac from there.
- There's also a connection to rogue anti-virus products as we've seen it end up on Conficker.C infected machines. The rogue product was SpywareProtect2009.
- Conficker.E deletes itself if the date is May 3, 2009 or later. It does not delete Conficker.C though so that will remain on an infected computer.
Sound complicated and strange? It is and unfortunately nothing is easy when it comes to Conficker so we'll continue to update this post as we find out more about its behavior. We detect the new Conficker.E since yesterday and all the related files it downloads.
- feng.pc-officer.com
- ihe1979.3322.org
Right now, host ihe1979.3322.org does not resolve at all, and feng.pc-officer.com resolves to a placeholder IP (which is 63.64.63.64). The attackers can temporarily make the hostname resolve to the real IP address and then turn it back, to hide their tracks.
The domain name
pc-officer.com is a weird one. It has been registered already in 2006, and it has been used in targeted attacks before.
See this ISC blog entry from
September 2007. Here the attack was done via a DOC files, instead of XLS. And the reporting server was
ding.pc-officer.com, not
feng.pc-officer.com.
If you haven't read about
Ghostnet yet, now would be a good time.
PS. We don't know what area is shown in the map image. If you do, please
leave a Comment.
Updated to add, Wednesday the 7th of April: We kept monitoring the host
feng.pc-officer.com. As expected, it became alive for a short period yesterday.
Here's what our logs look like:
Tue 7 Apr 2009 16:13:21
63.64.63.64 Tue 7 Apr 2009 16:14:17
63.64.63.64 Tue 7 Apr 2009 16:15:13
63.64.63.64 Tue 7 Apr 2009 16:16:09
216.255.196.154 Tue 7 Apr 2009 16:17:04
216.255.196.154 Tue 7 Apr 2009 16:18:00
216.255.196.154 Tue 7 Apr 2009 17:40:33
216.255.196.154 Tue 7 Apr 2009 17:41:29
216.255.196.154 Tue 7 Apr 2009 17:42:25
216.255.196.154 Tue 7 Apr 2009 17:43:21
63.64.63.64 Tue 7 Apr 2009 17:44:17
63.64.63.64 Tue 7 Apr 2009 17:45:13
63.64.63.64IP 63.64.63.64 is just a placeholder; 216.255.196.154 is the real control server. They only bring it online sporadically, trying to avoid detection.
The IP is located in Spokane, USA:
% whois 216.255.196.154
OrgName: One Eighty Networks
OrgID: OEN-1
Address: 118 N Stevens
City: Spokane
StateProv: WA
PostalCode: 99201
Country: US
Updated to add, Thursday the 9th of April: It changed again. Host
feng.pc-officer.com is now pointing to
211.234.122.84.
This IP is located in Seoul. South Korea:
% whois 211.234.122.84
[ IPv4�ּ� ��� ��� ���� ]
���������ȣ : ORG137200
����� : (��)����������
�ּ� : ������ ������
���ּ� : 261-1
������ȣ : 135-010