|
Thursday, January 30, 2014
|
|
And on Friday, the 30th of January, 2004: the universe's first antivirus blog was born!
Then Sunday…
Continuing to this very day!
Thank you, loyal readers.
To quote Mikko: "I've never had an uninteresting day at work." And the mission of this blog? To share some of the fun.
Code Warriors:

Lab coats:

Alexey, Jusu, Jarno, and Jarkko:

Helsinki + Kuala Lumpur:

Ero in action:

Mika the virenjager:
Antti's phish story:
 Bagles
Bagles:

Testing laptop locks:

Most people don't even know what a rootkit is…

Happy Anniversary, News from the Lab!
—————
P.S. More than 2,600 entires are available in our
monthly archives.
|
Tuesday, January 28, 2014
|
|
|
Wednesday, January 22, 2014
|
|
|
Tuesday, January 21, 2014
|
|
|
Wednesday, January 15, 2014
|
|
|
Tuesday, January 14, 2014
|
|
|
Thursday, January 9, 2014
|
|


The attachments usually have the following filenames.

The binary attachment is a threat that is often referred to as Fareit. Fareit is known to steal information such as credentials and account information from installed FTP clients and cryptocurrency wallets, and stored passwords in browsers.
For the two samples coming from these spam, we've seen them connecting to these to send information:
� networksecurityx.hopto.org
� 188.167.38.131
� 94.136.131.2
� 66.241.103.146
� 37.9.50.200
In addition to stealing data, these samples download other malware including Zeus P2P from:
� ip-97-
*.net/zA6.exe
� 119
*4/fF3krry.exe
� rot
*.com/124Tzh.exe
� ww
*ng.net/bpuMp.exe
� dev
*.com/1mHifVu.exe
� surfa
*.com/DJm.exe
� kl
*.com/Q4EzT.exe
Other malware seen installed in the system was Cryptolocker.
Apparently, spam overdose results in malware overdose.
Samples are detected as Trojan.Pws.Tepfer and Trojan.GenericKD variants.
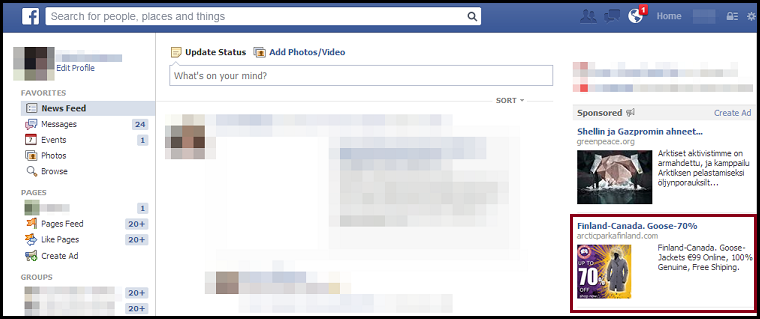
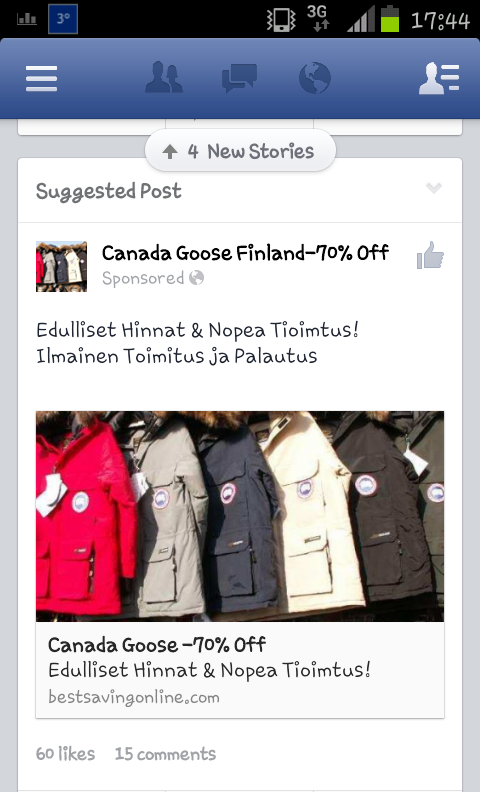
Upon clicking the ads, one ends up in a normal-looking shopping site. Complete with all the online shopping bells and whistles.
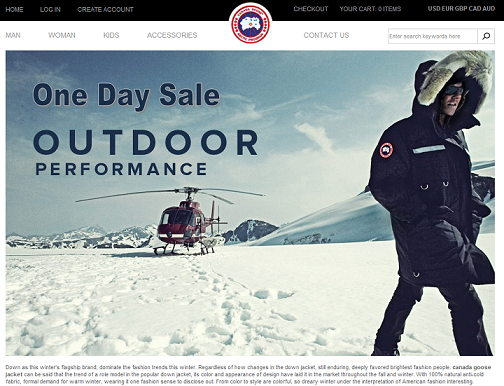
The ads have some mixed comments, from people saying that this is too good to be true, to those who almost bought them.
Now why do we think this site smells foul?
- Website has only 1 year validity
- Registrant is not local to the country/continent it's selling to (currently registered in China)
- Website is selling goods at 50-70% discount (Have you ever seen Canada Goose at these prices?)
- Website has no encryption when user is filling in personal information
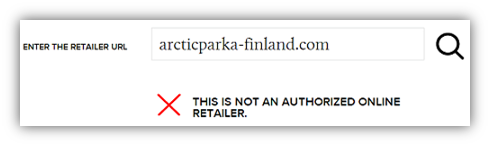
- The store/site is not an official Canada Goose retailer according to Canada Goose's
online retailer search tool:
Oakley was also victimized by this scamming method last year and they took strong measures by seizing sites down and giving visitors some information on it:

Kudos to Oakley for being so vigilant against this!
Although these reputable brands are taking strong measures to take down these fake sites, it's possible that a potential buyer may stumble unto them before the actual brand owners do. As such, we can't emphasize it strongly enough, please be extra careful when shopping online. Scam sites are sprouting everywhere and are selling anything that anyone can possibly want. If this is the first time you have heard of the website, you are unsure of its reputation, and the offers are very tempting, it would be best not to shop there. There is no certainty that you will get the right product, or even anything at all in return.
F-Secure Users with their browsing protection enabled are protected from these suspect sites.
—————
Post by — Karmina and Christine