Zafi.F
Summary
A new variant of Zafi worm - Zafi.F is spreading. While the original Zafi.A uses only Hungarian, the Zafi.F spreads in email in English, Italian, Spanish, Russian, Swedish and several other languages. The worm sends itself in infected messages attached as .pif, .cmd, .bat, .com or .zip file. This variant of Zafi also spreads in P2P networks. It can display a decoy message in message box saying "Image format error!"
Removal
Based on the settings of your F-Secure security product, it will either move the file to the quarantine where it cannot spread or cause harm, or remove it.
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
Zafi.F spreads in FSG! packed form which is 16770 bytes in size. The body unpacks to around 30 KiB of hand-written assembly code.
System Infection
When Zafi.F is started it copies itself to the Windows System Directory with a name "AntiVirus Update.exe". This file is added to the following registry key:
[HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] "Zi5" = "%System%\AntiVirus Update.exe"
Zafi.F creates a mutex named "Zi5" for making sure that only one copy of the worm is run at the same time.
Zafi.F enumerates all the directories in the system and copies itself as either 'Adobe Acrobat 8.0 Pro.exe' or 'Windows Update Crack.exe' to the ones that contain 'shar', 'uploa' or 'musi' in their name.
Email Propagation
Zafi.F looks into the Windows Address Book and different files and tries to gather email addresses. Files with the following extensions are checked:
- dbx
- asp
- txt
- htm
- mbx
- wab
- php
- sht
- adb
- tbb
- inb
- pmr
- fpt
- eml
Using its own SMTP engine the worm sends messages with infected attachments in many different languages. It can use different SMTP relays for sending its messages depending on the language.
For email addresses in the following domains the worms sends messages in the respective languages:
.hu .sp .se .de .at .ch .nl .fr .it .es .mx .ru
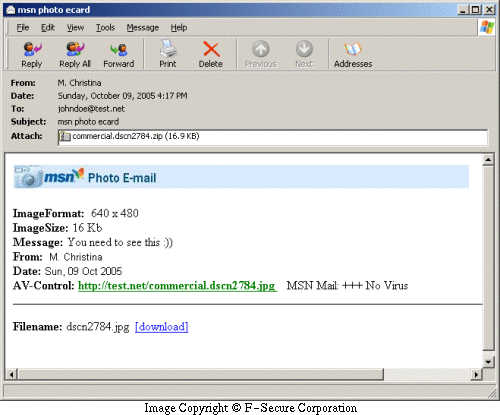
Following text is an example of english message:
From: M. Christina Subject: msn photo ecard commercial ecard :))
Sender name is used as a fallback if the email address doesn't have it.
Other language versions are as follows:
From: Szalai Bernadett Subject: legszexibb megasztar foto! szavazz ra te is! From: N. Fernandez Subject: broma :)) humor :)) From: H. Andersson Subject: rolig reklam :)) haha - rolig :)) From: H. Maria Subject: witzig reklame :)) witzig bild :D From: R. Cornel Subject: grappig beeld :)) een grappig reclame :DFrom: B. Martin Subject: blague :)) humour - reclame :)) From: R. Antonio Subject: scherzo :)) comico quadro :)) From: N. Fernandez Subject: broma :)) humor :)) From: D. Alexej Subject: humor.ru :D The body message is ImageFormat: 640x480 ImageSize: 16Kb Message: you need to see this :)) From: Date: AV-Control: MSN Mail: +++ No Virus
The actual attachment is a ZIP file with name composed of the following words:
- reklam
- megasztar
- humor
- reklame
- reclame
- funny
- commercial
Inside the ZIP file, there is a copy of the worm using one of the following file extensions:
- .bat
- .cmd
- .com
- .pif
Here's a screenshot of English message:
The worm does not send emails to addresses that contain any of these strings:
- admi
- bitde
- contact@
- eset
- -faq
- help
- hotmai
- info
- linux
- kasper
- mcafe
- micro
- msn
- nod3
- panda
- sales
- secur
- service
- soft
- sopho
- subsc
- suppor
- support
- symant
- test
- trend
- use
- webm
- win
- www
Payload
Zafi.F terminates any application that has the words 'firewall' or 'virus' in it. These files are overwritten with a copy of the worm.
Several Windows tools, like Task Manager, Registry Editor are disabled when the worm is active. Zafi.F opens these files with exclusive locking to prevent anything else from opening them.
Zafi.F has a backdoor that listens on port 2121. The worm can upload and execute file using the backdoor.
)
Protect your devices from malware with F‑Secure Total
Protecting your devices from malicious software is essential for maintaining online security. F‑Secure Total makes this easy, helping you to secure your devices in a brilliantly simple way.
- Award-winning antivirus and malware protection
- Online browsing, banking, and shopping protection
- 24/7 online identity and data breach monitoring
- Unlimited VPN service to safeguard your privacy
- Password manager with private data protection
More Support
Community
Ask questions in our Community .
User Guides
Check the user guide for instructions.
Submit a Sample
Submit a file or URL for analysis.