Worm:W32/Ippedo
Summary
The detection Worm:W32/Ippedo identifies the malicious shortcut (.LNK) files used by the Ippedo worm to lure users into unwittingly launching its malicious code. Once active on a machine, the worm can be directed by a remote attacker to perform various malicious actions, including performing ad-clicking, downloading additional files onto the machine, stealing information from it, restarting or shutting down the system and so on.
Removal
Based on the settings of your F-Secure security product, it will either move the file to the quarantine where it cannot spread or cause harm, or remove it.
If the LNK files are still present after automatic removal, we recommend performing a manual scan on any attached removable drives, and then a full system scan on the affected desktop machine.
-
In the F-Secure security product, go to the
Settings menu.
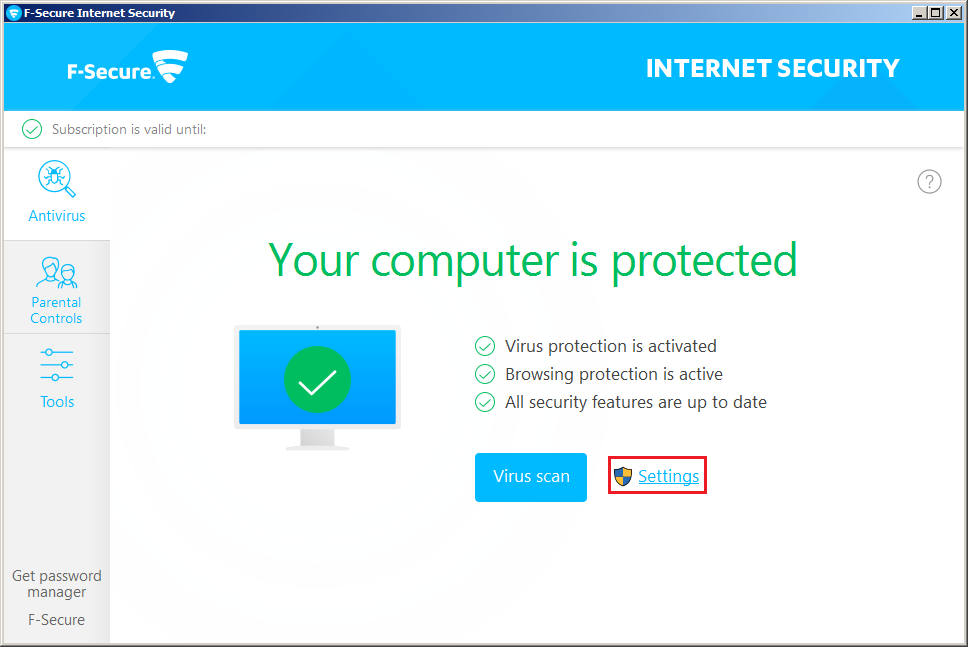
-
Under Manual scanning, untick the option
Scan only known file types (faster) and
then click OK.
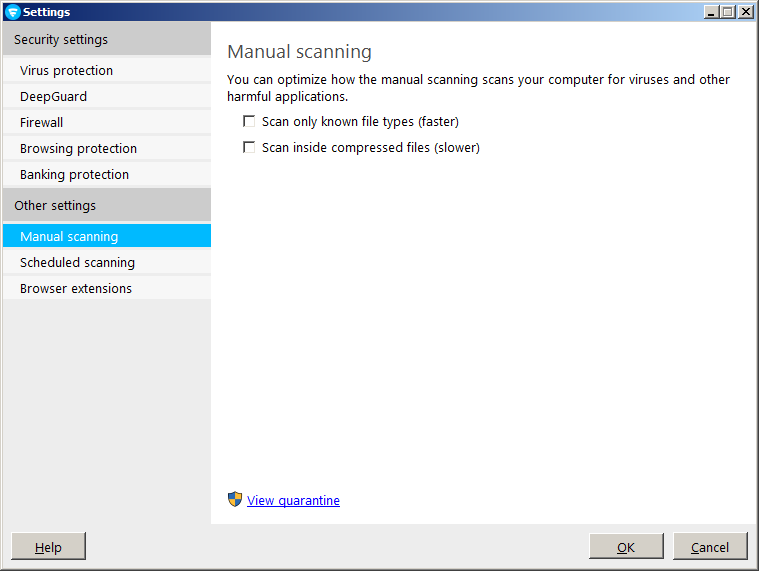
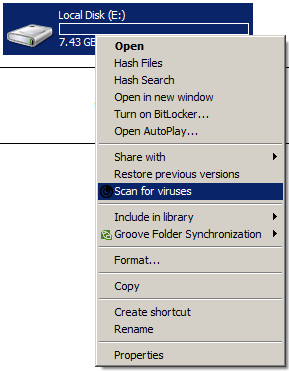
- Run a manual scan on the removable drive.
-
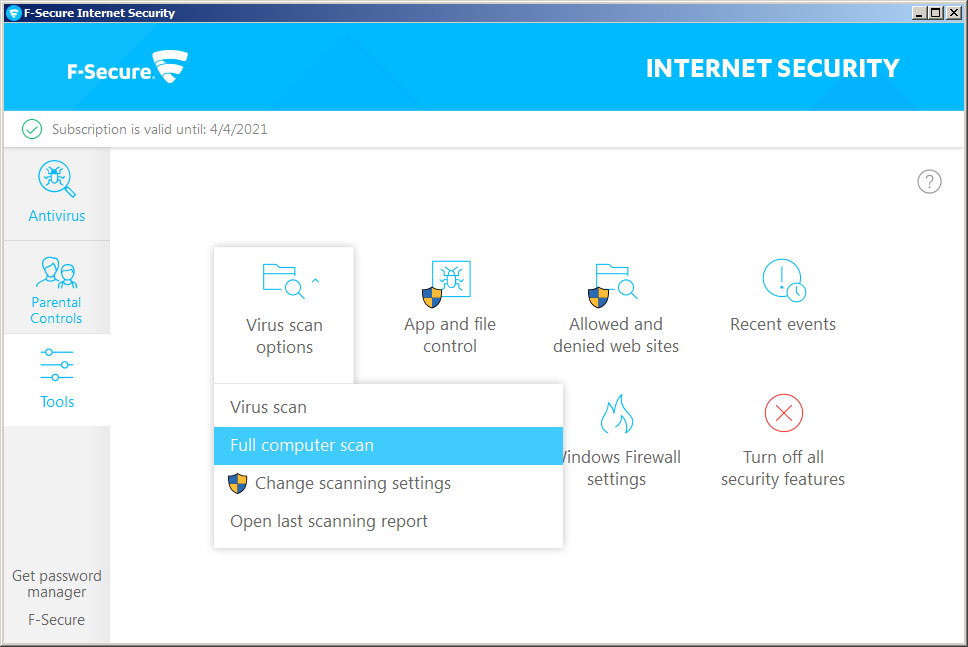
After the scan is complete, select
Handle all.
Once the harmful items are cleaned, you should see a scanning report.
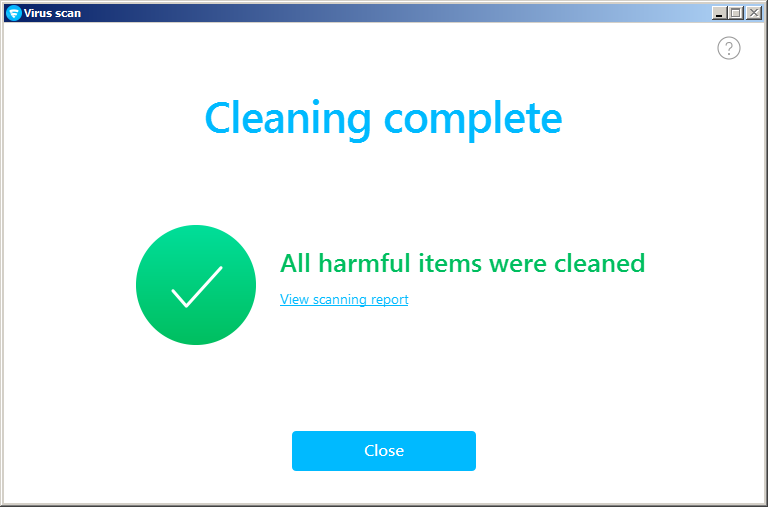

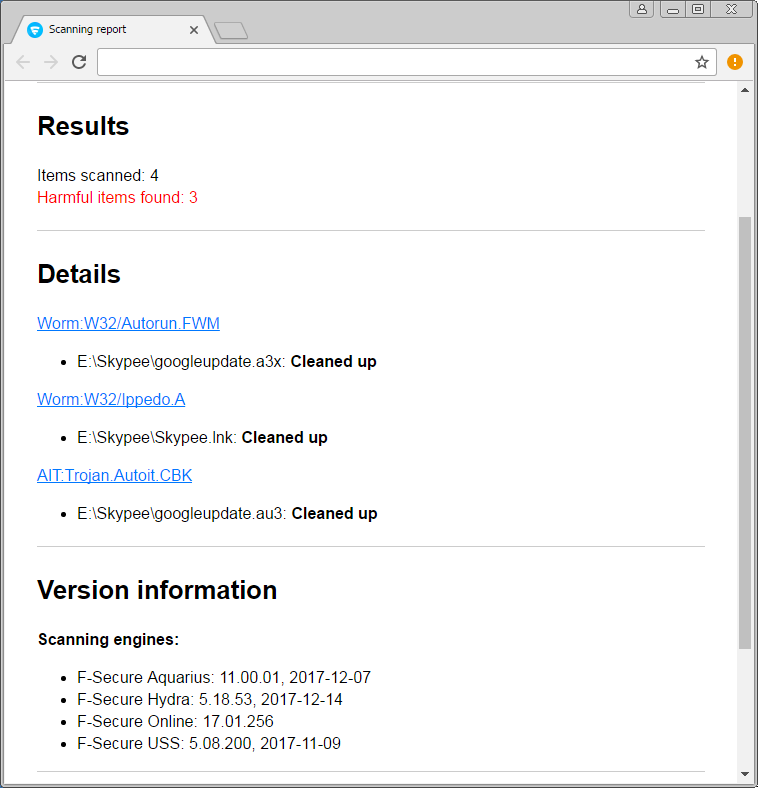
-
After cleaning the removable drive, perform a full
system scan on the affected desktop.
-
Again, after the scan is complete, select
Handle all.
Once the harmful items are cleaned, you should see a scanning report.
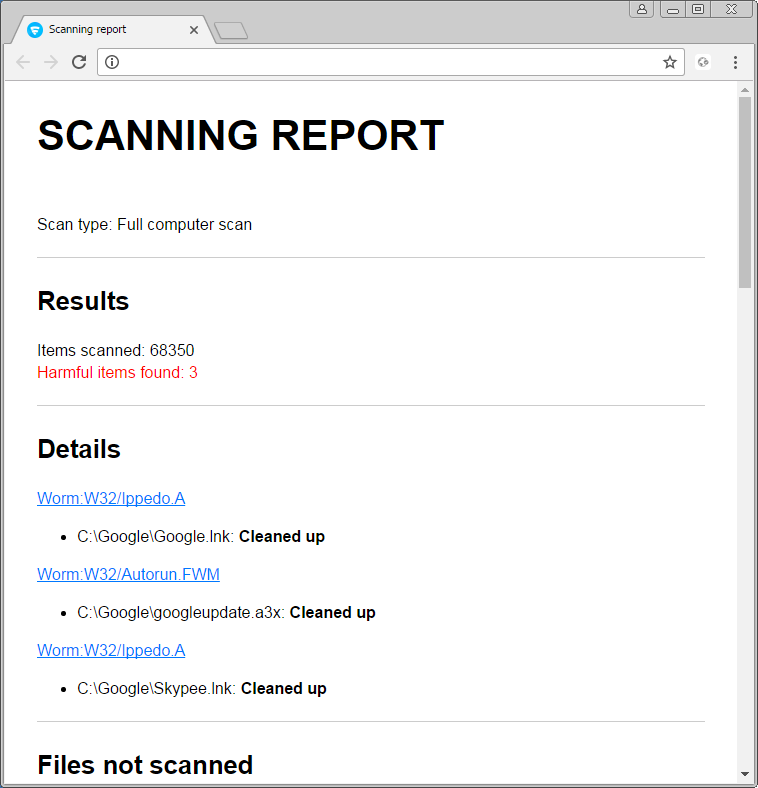
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
Worm:W32/Ippedo spreads through infected removable drives. When a removable drive is inserted into a machine and the worm's malicious file is launched, it installs multiple files to the C:\Google and C:\Skypee folders. The added files include a copy of the worm's main executable file. Ippedo also deletes the legitimate googleupdate.vbs file.
Malicious LNK files
The shortcut (.LNK) files installed by the worm are linked to a executable program, an executable Autoit script launcher and an Autoit script which deploys a backdoor on the affected machine. Click on any of the disguised LNK files launches the associated malicious program, launcher or script, which can perform a number of malicious actions, including:
- Contacting a remote server
-
Looking for and sending the following system to a remote
location:
- Operating system version
- Installed antivirus program
- Computer and user names
- Geographical location
-
Executing commands from a remote attacker, including:
- Downloading and executing additional malicious files
- Performing ad-clicking
- Restarting and shutting down the computer
- Updating the worm
And so on.
When it is launched, Ippedo's malicious executables first check to see if it is running in a virtual environment or if the machine includes files or processes that indicate it is used for malware analysis; if so, it will terminate itself.
Adds files
The worm adds .LNK shortcut files (the component identified by the Worm:W32/Ippedo detection) to the Startup folder and any connected removable drives, so that the worm copy is automatically executed each time the system starts or a user unsuspectingly clicks the shortcut. The links are deceptively named to appear legitimate, but all point to the worm's main file.
-
In C:\Google\Skypee:
- Autoit.exe
- Googleupdate.a3x
-
Skypee.lnk or Google.lnk
Target path: C:\Windows\system32\cmd.exe /c start ..\Skypee\AutoIt3.exe /AutoIt3ExecuteScript ..\Skypee\googleupdate.a3x explorer "%CD%" & exit
-
In the Startup menu
- C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup\AntiUsbWormUpdate.lnk
- C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup\AntiWormUpdate.lnk
Registry modification
It also modifies the registry so that its copy is run each time Windows is started, and adds the following registry keys:
-
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run]
"AntiWormUpdate"="C:\\Google\\AutoIt3.exe /AutoIt3ExecuteScript C:\\Google\\googleupdate.a3x"
"AntiUsbWorm"="C:\\Windows\\system32\\cmd.exe /c start C:\\Google\\AutoIt3.exe /AutoIt3ExecuteScript C:\\Google\\googleupdate.a3x & exit" -
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run]
"AntiWormUpdate"="C:\\Google\\AutoIt3.exe /AutoIt3ExecuteScript C:\\Google\\googleupdate.a3x"
"AntiUsbWorm"="C:\\Windows\\system32\\cmd.exe /c start C:\\Google\\AutoIt3.exe /AutoIt3ExecuteScript C:\\Google\\googleupdate.a3x & exit"c