Worm:W32/Agent.IPZ
Summary
A standalone malicious program which uses computer or network resources to make complete copies of itself.
Removal
Based on the settings of your F-Secure security product, it will either move the file to the quarantine where it cannot spread or cause harm, or remove it.
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
There are two ways that this worm may arrive on a user's system: it may be delivered directly to the user in an infected email attachment, or the user may unknowingly download it from an infected website host.In the first method, the emails are sent out from other, infected machines. The worm's code is stored in a ZIP file attachment to the email. Each email will use one of these two sets of characteristics:
- Subject: "IKEA's New Planning Software" Attachment: Ikea.zip
- Subject: "You've received a Hallmark e-card!" Attachment: Postcard.zip
The worm may also be downloaded from an infected website host. If an infected machine is an IIS web server, the worm replaces the default index page at C:\Inetpub\wwwroot\index.htm with a page containing:
- "Security warning"
- A link, misleadingly named "MS09-067.exe", which downloads a copy of the malware from the Web server onto the system.
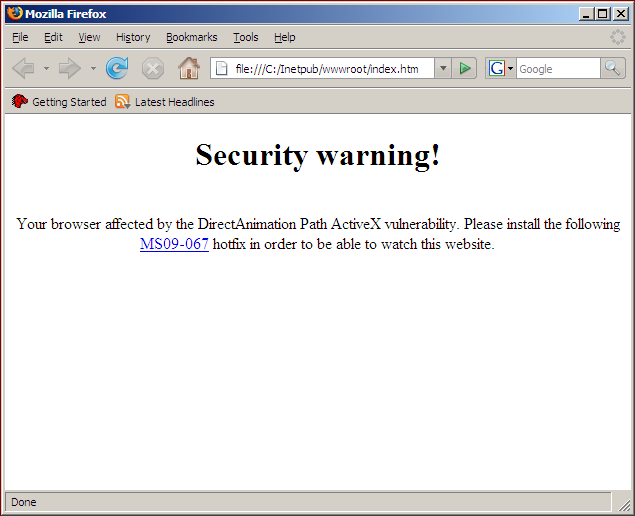
In both cases, running the extracted attachment or downloaded copy will launch the malware.
Execution
On execution, the worm will create a copy of itself.
- %windir%\system32\jushed.exe
It will also drop another malware file, detected as Trojan.Win32.Pakes.mmp.
- %windir%\system32\jqs.exe
It will then create registry entries so that the copy of the worm will run on system startup, as well as disabling the Windows Firewall.Next, the worm contacts this site to determine the infected system's IP address.
- http://whatismyip.com/
Propagation
To propagate itself via infected emails, the worm harvests all email addresses stored on the infected system and sends out messages to all the harvested addresses. Each email contains the worm's code in an attachment, and the email itself will use one of the same two sets characteristics (subject line, attachment name, etc) as the email the worm arrived in.For the worm to propagate via downloads from a Web server, the infected system must first have Microsoft IIS installed. If so, the worm will create a copy of itself in the following location:
- C:\Inetpub\wwwroot\MS-09-067.exe
It will also create or replace the following file:
- C:\Inetpub\wwwroot\index.htm
This new index page relies on social engineering to persuade visitors to download the malware.
Registry Modifications
Sets these values:
- HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer sun = 01
- HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer java = 03
- HKLM\SYSTEM\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile\AuthorizedApplications\List C:\WINDOWS\system32\jushed.exe = C:\WINDOWS\system32\jushed.exe:*:Enabled:Explorer [Windows Firewall Disabled]
- HKLM\Software\Microsoft\Windows\CurrentVersion\Run SunJavaUpdater = C:\WINDOWS\system32\jushed.exe [Launchpoint: Run]
- HKU\S-1-5-21-299502267-823518204-839522115-1003\Software\Microsoft\windows\CurrentVersion\Internet Settings MigrateProxy = 6619252
- HKU\S-1-5-21-299502267-823518204-839522115-1003\Software\Microsoft\windows\CurrentVersion\Internet Settings ProxyEnable = 4522105
- HKLM\SYSTEM\CURRENTCONTROLSET\HARDWARE PROFILES\CURRENT\Software\Microsoft\windows\CurrentVersion\Internet Settings ProxyEnable = 4522105
- HKU\S-1-5-21-299502267-823518204-839522115-1003 SavedLegacySettings =
- HKCU\Software\Microsoft\Windows NT\CurrentVersion øøø[...]=16253176
- HKCU\Software\Microsoft\Windows NT\CurrentVersion (default) = H1UYEEMA[QRspr{gm8;Rfzz iqn
- HKLM\Software\Microsoft\Windows NT\CurrentVersion\SystemRestore DisableSR = 6357107 [System Restore Disabled]
- HKCU\Software\Microsoft\Windows\CurrentVersion\Run QnX = C:\WINDOWS\system32\jqs.exe [Launchpoint: Run]
- HKLM\SOFTWARE\Microsoft\Active Setup\Installed Components\{77520Q86-864L-N81R-0R2W-7U2G0P22436U} StubPath = "C:\WINDOWS\system32\jqs.exe" [Launchpoint: Active Setup]
- HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run QnX = C:\WINDOWS\system32\jqs.exe [Launchpoint: Explorer]