Worm:SymbOS/Mabir.A
Summary
Worm:SymbOS/Mabir.A is a worm that infects devices running the Symbian Series 60 operating system. Mabir.A is capable of spreading in an infected symbian Installation (SIS) file over both Bluetooth and MMS.
Removal
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
The SIS file that Mabir.A sends use the file name "caribe.sis". Please note that though Mabir.A uses the same SIS file name as Cabir worms, it is actually different worm.
Infection
On receiving the transmitted SIS file, it is automatically installed.
During installation, the installer will copy the worm executables into following locations:
- \system\apps\Caribe\Caribe.app
- \system\apps\Caribe\Caribe.rsc
- \system\apps\Caribe\flo.mdl
When the Mabir.exe is executed it copies the following files:
- \system\symbiansecuredata\caribesecuritymanager\Caribe.app
- \system\symbiansecuredata\caribesecuritymanager\Caribe.rsc
And rebuilds its SIS file to:
- \system\symbiansecuredata\caribesecuritymanager\Info.sis
Replication (Bluetooth)
When Mabir worm is activated on an infected device, it uses the native Bluetooth functionality to start looking for other discoverable Bluetooth-enabled devices. If found, it transmits an infected SIS file to the targetted device. If the target goes out of range or rejects file transfer, Mabir will continue trying to communicate with the same device.
The infected SIS file is always named caribe.sis. To be infected, a user must selected 'Yes' when prompted to do so.
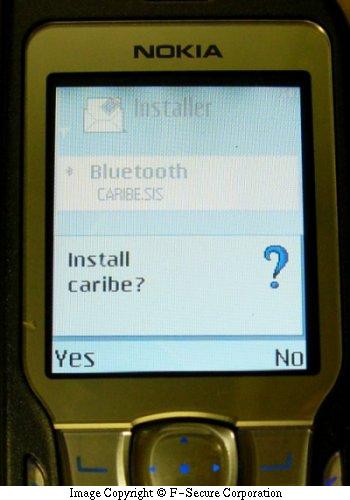
The file contains the worm component files caribe.app, caribe.rsc and flo.mdl. It also contains autostart settings that will automatically execute caribe.app after the SIS file is being installed, thus starting the worm.
Replication (MMS)
MMS messages are multimedia messages that are intended to contain only media content, such as pictures, audio or video, but can also be used to transmit infected Symbian installation files.
The MMS sending is triggered by MMS or SMS message that arrives to the phone, causing Mabir to send itself as MMS message to the number from which the message arrived from. Thus the Mabir tries to fool the receiver that it has been sent as reply to the message that user sent to the infected phone.
The Mabir worm does not use any texts in the MMS messages it sends.
When the recipient opens the MMS message containing the infected SIS file, the action automatically executes the file and causes it to install.
)
Protect your devices from malware with F‑Secure Total
Protecting your devices from malicious software is essential for maintaining online security. F‑Secure Total makes this easy, helping you to secure your devices in a brilliantly simple way.
- Award-winning antivirus and malware protection
- Online browsing, banking, and shopping protection
- 24/7 online identity and data breach monitoring
- Unlimited VPN service to safeguard your privacy
- Password manager with private data protection
More Support
Community
Ask questions in our Community .
User Guides
Check the user guide for instructions.
Submit a Sample
Submit a file or URL for analysis.