UrlSpoof.E
Summary
On January 24th and 25th, 2004, a number of emails with a fake virus warning from Microsoft were spammed. When users view the email it attempts to download and execute a variant of VBS/Inor trojan dropper from a web site. The real address has been spoofed using a security vulnerability in Internet Explorer.
Removal
Based on the settings of your F-Secure security product, it will either move the file to the quarantine where it cannot spread or cause harm, or remove it.
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
When an user opens the spammed email, an attept to download and execute a VBS/Inor dropper is made. If the dropper is able to execute, then a variant of W32/Dumaru worm is installed into system. Inor drops the worm to "C:\2.exe".
We have received reports that different variants of W32/Dumaru have been dropped from the web site. Further information about W32/Dumaru is available within the following descriptions:
At the time of writing this description, the trojan downloader is removed from the web site.
Below is a screenshot of the message:
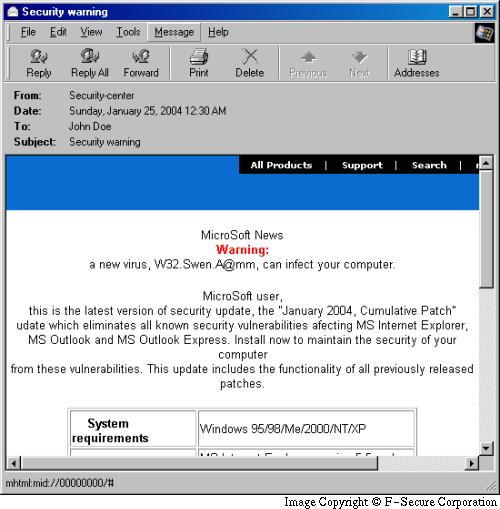
)
Protect your devices from malware with F‑Secure Total
Protecting your devices from malicious software is essential for maintaining online security. F‑Secure Total makes this easy, helping you to secure your devices in a brilliantly simple way.
- Award-winning antivirus and malware protection
- Online browsing, banking, and shopping protection
- 24/7 online identity and data breach monitoring
- Unlimited VPN service to safeguard your privacy
- Password manager with private data protection
More Support
Community
Ask questions in our Community .
User Guides
Check the user guide for instructions.
Submit a Sample
Submit a file or URL for analysis.