Trojan.GenericKD.3016333
Summary
Trojan.GenericKD.3016333 is ransomware that encrypts files stored on the affected device and demands payment of a ransom.
Removal
Based on the settings of your F-Secure security product, it will either move the file to the quarantine where it cannot spread or cause harm, or remove it.
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
This malware is distributed via a spam email message that pretends to be a notification from either the POSTNORD or AUPOST postal services (POSTNORD caters to Denmark and Sweden, while AUPOST deals with delivery in Australia). The text content of the message is typically about lost or undelivered packages and the email includes a contain ZIP file attachment that is the actual ransomware file. Malicious links in the email text content reportedly could also lead the user into downloading the ransomware file.
The ZIP file attachment most commonly uses the filenames "postnord_info_59278.exe", "bolletta_36135.exe", and "AUPOST_info_23884.exe". The attachment contains an executable program that uses a PDF file icon; this is a common technique used by malware authors to trick users into thinking that the file is a document rather than an executable program.
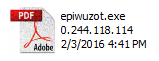
Ransomware executable file disguised as a PDF document
If the camouflaged executable file is run, it injects inject malicious code into the "explorer.exe" processes. It moves the ransomware file to %WINDOWS% and renames it as <8_random_alphanumeric_characters>.exe.
It then removes other copies in %LOCAL_APPDATA%\temp\ and encrypts the user's files. It also drops a text file containing the following ransom demand, as well as instructions for payment:
=============================================================================== !!! Vi har krypterat dina filer med Crypt0L0cker virus !!! =============================================================================== Dina viktiga filer (inklusive de på nätverksdiskar, USB, etc): bilder, videor, var dokument krypteras med vår Crypt0L0cker virus. Det enda sättet att få dina filer tillbaka är att betala oss. Annars kommer dina filer att gå förlorade.Klicka här för att betala för filer återvinning:------------------------------------------------------------------------------- ------------------------------------------------------------------------------- [=] Vad har hänt med mina filer?Dina viktiga filer: bilder, video, var dokument krypteras med vår Crypt0L0cker virus. Detta virus använder mycket stark krypteringsalgoritm - RSA-2048. Brytning av RSA-2048 krypteringsalgoritm är omöjlig utan särskild krypteringsnyckel. [=] Hur kan jag få mina filer tillbaka?Dina filer är nu oanvändbara och oläslig, du kan verifiera det genom att försöka öppna dem. Det enda sättet att återställa dem till ett normalt tillstånd är att använda vår speciella dekryptering programvara. Du kan köpa denna dekryptering programvara på vår hemsida [malware_site]. [=] Vad ska jag göra härnäst?Du bör besöka vår hemsida [malware_site] och köpa dekryptering för din dator. [=] Jag kan inte komma till din webbp
The malware also uses a domain generation algorithm that based on its network activity; the generated domains are used by the malware to determine the location of its command and control (C&C) server, which it will later try to contact. Generated domains are:
- nwowapi.ksmvryodp.com
- akimhsewf.ksmvryodp.com
- hkyjymubudy.ksmvryodp.com
- wsyhew.ksmvryodp.com
- ipokikgzadg.ksmvryodp.com
- izvli.ksmvryodp.com
- acujyz.ksmvryodp.com
- erojibpfi.rygzatyee.com
- aqyn.rygzatyee.com
- ahuby.rygzatyee.com
- orid.rygzatyee.com
- eqova.rygzatyee.com
- eqilufyk.rygzatyee.com
- afazoriju.rygzatyee.com
The presence of the malware's randomly named file in the %WINDOWS% folder is an indicator of infection; another such indicator is the existence of the ransom note and instructions for payment. The malware also creates the following autorun keys, mutexes and component files, which are also indicators of infection:
-
Autorun keys:
- HKLM\Software\Microsoft\Windows\CurrentVersion\Run
-
Mutexes:
- \BaseNamedObjects\<31_randoms_letters>
- \BaseNamedObjects\ihejicyrywonulatupaxafubevuzezu
- \BaseNamedObjects\imefanafytotehadujulifygicumovo
-
Component files:
- %programdata%\<16_random_letters>\02000000
- %programdata%\<16_random_letters>\01000000
- %appdata%\<16_random_letters>\01000000
- %appdata%\<16_random_letters>\01000000