Trojan:Android/GinMaster.A
Summary
Trojan:Android/GinMaster.A steals confidential information from the device and sends it to a remote website.
Removal
Once the scan is complete, the F-Secure security product will ask if you want to uninstall the file, move it to the quarantine or keep it installed on your device.
Monitoring-Tool:Android/GinMaster.A can be uninstalled by following the steps below:
- Go to Settings
- Go to Applications
- Go to Manage Applications
- Select the application
- Press "Clear data"
- Press "Uninstall"
- Select "OK" when asked for confirmation and wait
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
Trojan:Android/GinMaster.A is a trojanized application which was first seen in the Android Market for (mainland) China by researchers from North Carolina State University. The exploit source code has been publicly available since April 2011.
It is the first malicious software to utilize a rooting exploit that targets Android 2.3.3 (Gingerbread) devices to escalate privileges on the system. Based on the author's own description of the exploit and examination of its binary, it may also work on Android 2.2 (Froyo) and 3.0 (Honeycomb) devices.
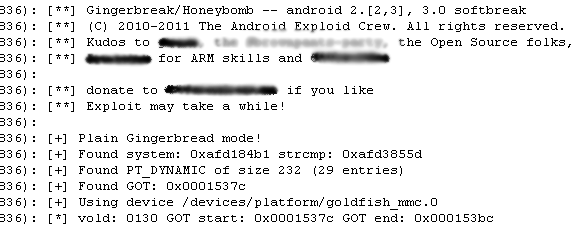
Trojan:Android/GinMaster.A's own description.
However, in the particular sample analyzed, the trojan will only run the exploit if the device version is not greater than 2.3.3 (up to Gingerbread version only).
Trojan:Android/GinMaster.A's use of the exploit may allow it to install additional applications to the device without the user's consent.
Installation
The malicious application asks for the following permissions during installation:
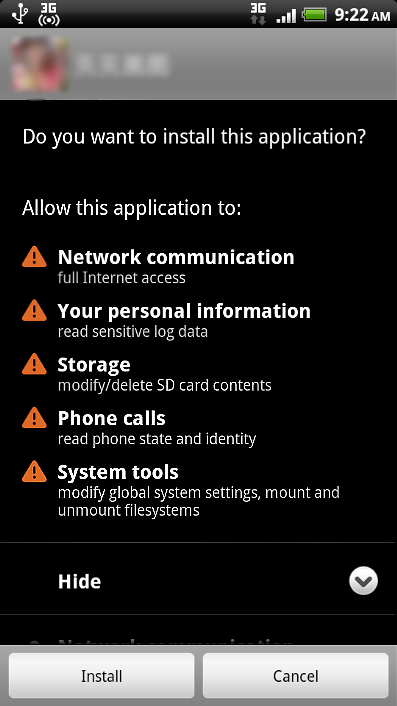
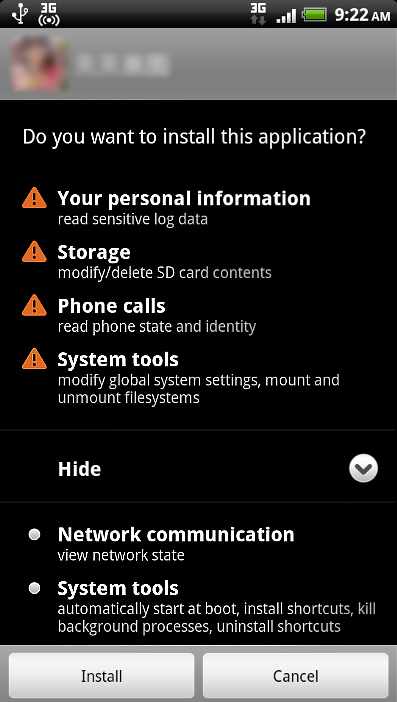
Permissions requested by Trojan:Android/GinMaster.A
If the user agrees with the permission requests and proceeds with installation, the application will start up a malicious service in the background. The malicious service is designed in such a way that as long as the main process is running, it will not be terminated by the operating system in the event of a device memory resources shortage.
This is how it looks like on the device in the list of running services.
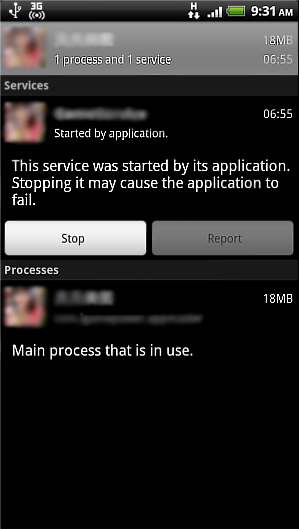
Trojan:Android/GinMaster.A starts a service in the background.
Activity
The malicious service (in effect, the trojan's payload) is triggered when one of the following conditions is met:
- When the trojanized application is running
- When the device finishes a boot
- When a new package is installed on the device.
- When a new package is removed from the device.
All these malicious activities occur invisibily in the background and are performed without notifying the user or seeking consent.
Downloads
While the trojanized application is running, to the user it appears to be a list of links leading to pretty images:


Some images from the trojanized application
After a few seconds, a popup message will appear that asks the user's confirmation to apply an update. If the user confirms, a new application update downloaded from the internet will be applied.
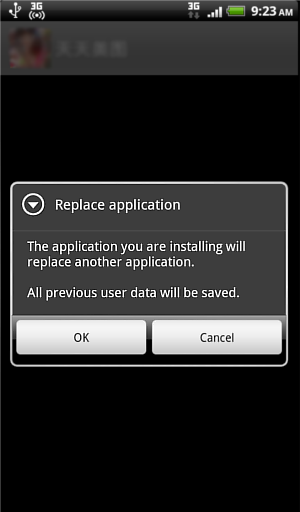
Popup dialogue.
The user can choose not to confirm the update and just press the phone's back button. The trojan however still proceeds to silently download the application package and save it in the device's SD card, all without the user's consent.
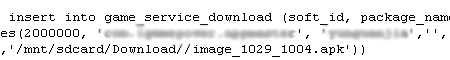
https://www.f-secure.com/v-pics/autodownload_update_2.png
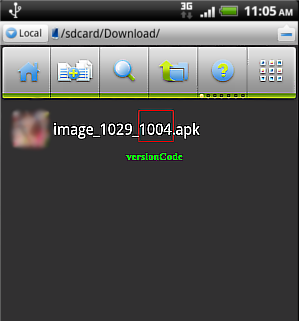
https://www.f-secure.com/v-pics/ginmaster_automatically_downloaded_update.png
Trojan:Android/GinMaster.A automatically downloads the 'update' regardless of user action (click for larger view).
Data harvesting
If any of the trigger conditions for the malicious service is met, it immediately downloads application configuration and harvests the following confidential information from the device:
- Current system time
- International Mobile Equipment Identity (IMEI)
- User Identifier (UID - same as IMEI)
- International Mobile Subscriber Identity (IMSI)
- SIM number
- Telephone number
- Network type
- Current version of app (versionCode)
- Serial number
The stolen information is sent to a remote site.
The trojan also collects package information of packages installed in the system (except those with "Android" or "Google" in the package name) and stores them in its local database.
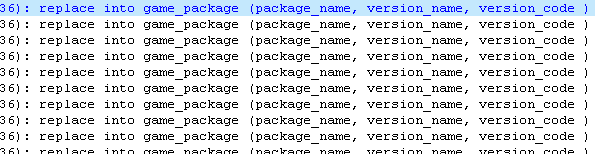
https://www.f-secure.com/v-pics/ginmaster_collected_package_info_db.png
Package information of installed programs harvested and saved (click for larger view).
The trojan also collects package information for apps newly installed on or removed from the device. For this sample, a test install of Skype was used.
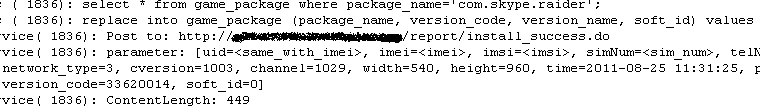
https://www.f-secure.com/v-pics/triggered_package_added_events.png
Package information of newly-installed program saved (click for larger view).
The collected package information is also sent to the remote site together with the abovementioned confidential information.
Exploits
The malicious service then proceeds to the rooting process by first preparing the files it needs, then executing them.
The original files are suffixed with png extensions (presumably in order to mislead the user) but in fact they are ELF32 for ARM binaries and shell utility scripts.
Other variants
- Trojan:Android/Ginmaster.B
- Trojan:Android/Ginmaster.C
)
Protect your devices from malware with F‑Secure Total
Protecting your devices from malicious software is essential for maintaining online security. F‑Secure Total makes this easy, helping you to secure your devices in a brilliantly simple way.
- Award-winning antivirus and malware protection
- Online browsing, banking, and shopping protection
- 24/7 online identity and data breach monitoring
- Unlimited VPN service to safeguard your privacy
- Password manager with private data protection
More Support
Community
Ask questions in our Community .
User Guides
Check the user guide for instructions.
Submit a Sample
Submit a file or URL for analysis.