Trojan:Android/DroidKungFu.C
Summary
Trojan:Android/DroidKungFu.C forwards confidential details to a remote server.
Removal
Once the scan is complete, the F-Secure security product will ask if you want to uninstall the file, move it to the quarantine or keep it installed on your device.
Monitoring-Tool:Android/DroidKungFu.C can be uninstalled by following the steps below:
- Go to Settings
- Go to Applications
- Go to Manage Applications
- Select the application
- Press "Clear data"
- Press "Uninstall"
- Select "OK" when asked for confirmation and wait
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
Trojan:Android/DroidKungFu.C are distributed on unauthorized Android app sites as trojanized versions of legitimate applications.
Installation
Prior to installation, this new variant of the DroidKungFu family requests the following permissions:
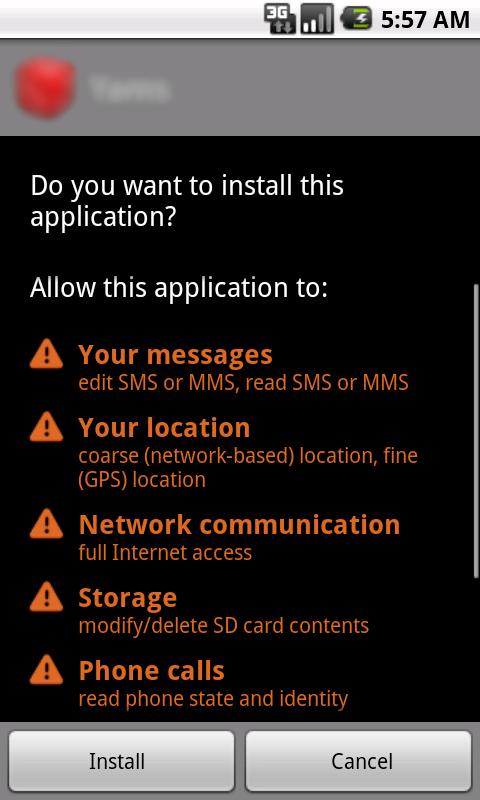
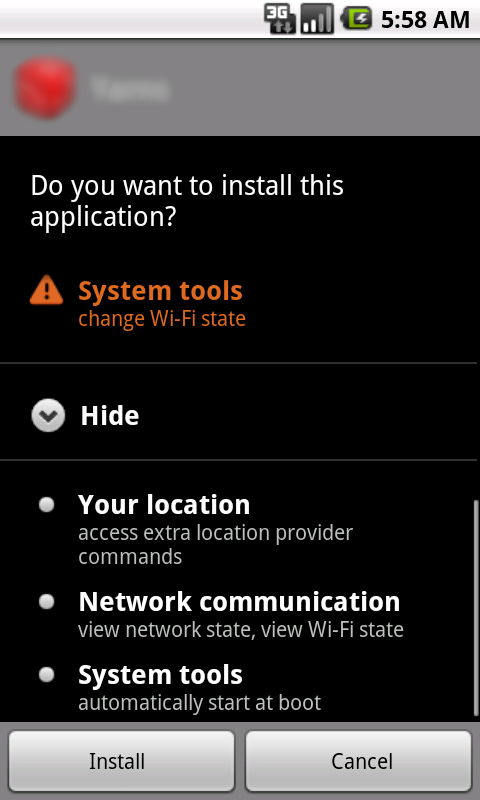
Activity
Once installed, DroidKungFu.C attempts to root the phone (gain control of the system) by using exploits, including RageAgainstTheCage. These exploits are stored in the malware package and encrypted with a key.
The trojan also attempts to collect the following information from the compromised device:
- International Mobile Equipment Identity (IMEI)
- Mobile device model
- Network operator
- Network type
- Operating system (OS) APIs
- OS type
- Information stored in the Phone memory
- Information stored in the SD card memory
The collected information is reported to remote command and control (C&C) servers at multiple locations:
- http://[...]search.gongfu-android.com:8511/[...]search/
- http://[...]search.zi18.com:8511/[...]search/
- http://[...]search.zs169.com:8511/[...]search/
More
This trojan was discovered by researchers at the North Carolina State University. For additional information, see: