Trojan:W32/Renos.H
Summary
Trojan:W32/Renos.H attempts to lure the computer user into downloading "rogueware" by presenting pop-up windows that warn of a supposed threat. In addition, Renos.H modifies the computer's hosts-file in such a way that accessing websites of many antivirus vendors is blocked.
Removal
Based on the settings of your F-Secure security product, it will either move the file to the quarantine where it cannot spread or cause harm, or remove it.
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
When Trojan:W32/Renos.H is run it copies itself to four locations on the hard drive.
- %userprofile%\Start Menu\Programs\Startup\autorun.exe
- %userprofile%\Start Menu\Programs\Startup\system.exe
- %windir%\system32\printer.exe
- %windir%\system32\WinAvXX.exe
It adds the following registry keys so that WinAvXX.exe and printer.exe are automatically run during the system startup.
- HKCU\Software\Microsoft\Windows\CurrentVersion\Run WinAVX = C:\WINDOWS\system32\WinAvXX.exe
- HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon Shell = Explorer.exe C:\WINDOWS\system32\printer.exe
Programs and shortcuts in the %userprofile%\Start Menu\Programs\Startup\ folder are automatically executed on startup. Therefore the other two copies of the trojan are also run every time the infected computer is started; however only one copy will remain running at any time. This makes manual disinfection of the computer more difficult as all four copies of the file must be deleted, if even one remains it will copy itself back into all four locations.To further hinder it's removal, Renos makes the following changes to Windows Registry:
- HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\System DisableTaskMgr = 00000001
- HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\System DisableRegistryTools = 00000001
- HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer NoControlPanel = 00000001
- HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer NoWindowsUpdate = 00000001
The above keys disable access to the task manager, registry tools (regedit.exe and regedit32.exe), control panel, and Windows updates.Winav.exe is added to the list of authorized applications for the Windows XP firewall. Winav.exe is not a part of the trojan, so it is likely part of the software that it wants the computer user to download.Trojan:W32/Renos.H modifies the system to prevent the infected computer from accessing many websites, most of them antivirus related. This is accomplished by adding the following lines into the hosts file located by default in %windir%\system32\drivers\etc under Windows NT/2000/XP/Vista:
- 192.168.200.3 ad.doubleclick.net
- 192.168.200.3 ad.fastclick.net
- 192.168.200.3 ads.fastclick.net
- 192.168.200.3 ar.atwola.com
- 192.168.200.3 atdmt.com
- 192.168.200.3 avp.ch
- 192.168.200.3 avp.com
- 192.168.200.3 avp.ru
- 192.168.200.3 awaps.net
- 192.168.200.3 banner.fastclick.net
- 192.168.200.3 banners.fastclick.net
- 192.168.200.3 ca.com
- 192.168.200.3 click.atdmt.com
- 192.168.200.3 clicks.atdmt.com
- 192.168.200.3 customer.symantec.com
- 192.168.200.3 dispatch.mcafee.com
- 192.168.200.3 download.mcafee.com
- 192.168.200.3 download.microsoft.com
- 192.168.200.3 downloads.microsoft.com
- 192.168.200.3 downloads1.kaspersky-labs.com
- 192.168.200.3 downloads2.kaspersky-labs.com
- 192.168.200.3 downloads3.kaspersky-labs.com
- 192.168.200.3 downloads4.kaspersky-labs.com
- 192.168.200.3 downloads-us1.kaspersky-labs.com
- 192.168.200.3 downloads-us2.kaspersky-labs.com
- 192.168.200.3 downloads-us3.kaspersky-labs.com
- 192.168.200.3 engine.awaps.net
- 192.168.200.3 fastclick.net
- 192.168.200.3 f-secure.com
- 192.168.200.3 ftp.avp.ch
- 192.168.200.3 ftp.downloads1.kaspersky-labs.com
- 192.168.200.3 ftp.downloads2.kaspersky-labs.com
- 192.168.200.3 ftp.downloads3.kaspersky-labs.com
- 192.168.200.3 ftp.f-secure.com
- 192.168.200.3 ftp.kasperskylab.ru
- 192.168.200.3 ftp.sophos.com
- 192.168.200.3 go.microsoft.com
- 192.168.200.3 ids.kaspersky-labs.com
- 192.168.200.3 kaspersky.com
- 192.168.200.3 kaspersky-labs.com
- 192.168.200.3 liveupdate.symantec.com
- 192.168.200.3 liveupdate.symantecliveupdate.com
- 192.168.200.3 mast.mcafee.com
- 192.168.200.3 mcafee.com
- 192.168.200.3 media.fastclick.net
- 192.168.200.3 microsoft.com
- 192.168.200.3 msdn.microsoft.com
- 192.168.200.3 my-etrust.com
- 192.168.200.3 nai.com
- 192.168.200.3 networkassociates.com
- 192.168.200.3 norton.com
- 192.168.200.3 office.microsoft.com
- 192.168.200.3 pandasoftware.com
- 192.168.200.3 phx.corporate-ir.net
- 192.168.200.3 rads.mcafee.com
- 192.168.200.3 secure.nai.com
- 192.168.200.3 securityresponse.symantec.com
- 192.168.200.3 service1.symantec.com
- 192.168.200.3 sophos.com
- 192.168.200.3 spd.atdmt.com
- 192.168.200.3 support.microsoft.com
- 192.168.200.3 symantec.com
- 192.168.200.3 trendmicro.com
- 192.168.200.3 update.symantec.com
- 192.168.200.3 updates.symantec.com
- 192.168.200.3 updates1.kaspersky-labs.com
- 192.168.200.3 updates2.kaspersky-labs.com
- 192.168.200.3 updates3.kaspersky-labs.com
- 192.168.200.3 updates4.kaspersky-labs.com
- 192.168.200.3 updates5.kaspersky-labs.com
- 192.168.200.3 us.mcafee.com
- 192.168.200.3 vil.nai.com
- 192.168.200.3 viruslist.com
- 192.168.200.3 viruslist.ru
- 192.168.200.3 virusscan.jotti.org
- 192.168.200.3 virustotal.com
- 192.168.200.3 windowsupdate.microsoft.com
- 192.168.200.3 www.avp.ch
- 192.168.200.3 www.avp.com
- 192.168.200.3 www.avp.ru
- 192.168.200.3 www.awaps.net
- 192.168.200.3 www.ca.com
- 192.168.200.3 www.fastclick.net
- 192.168.200.3 www.f-secure.com
- 192.168.200.3 www.grisoft.com
- 192.168.200.3 www.kaspersky.com
- 192.168.200.3 www.kaspersky.ru
- 192.168.200.3 www.kaspersky-labs.com
- 192.168.200.3 www.mcafee.com
- 192.168.200.3 www.microsoft.com
- 192.168.200.3 www.my-etrust.com
- 192.168.200.3 www.nai.com
- 192.168.200.3 www.networkassociates.com
- 192.168.200.3 www.pandasoftware.com
- 192.168.200.3 www.sophos.com
- 192.168.200.3 www.symantec.com
- 192.168.200.3 www.symantec.com
- 192.168.200.3 www.trendmicro.com
- 192.168.200.3 www.viruslist.com
- 192.168.200.3 www.viruslist.ru
- 192.168.200.3 www.virustotal.com
- 192.168.200.3 www3.ca.com
Renos.H also changes Internet Explorer's Home page, default search engine, and enables browser extensions and balloon tips. The trojan also changes the Internet security zone settings to enable ActiveX controls.When the trojan is running it presents the following dialog window every five minutes. The security issue it warns of does not actually exist and is just a hoax to get the user to download rogueware.
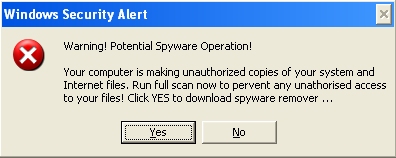
See the Rogue Antispyware description for additional details.Earlier versions of "Renos" were not intrinsically malicious towards the computer's OS, but were fraudulent. Current generations alter the Windows Hosts file and disable Windows Update, classifying them as Malware. See the Renos description for information on earlier versions.
)
Protect your devices from malware with F‑Secure Total
Protecting your devices from malicious software is essential for maintaining online security. F‑Secure Total makes this easy, helping you to secure your devices in a brilliantly simple way.
- Award-winning antivirus and malware protection
- Online browsing, banking, and shopping protection
- 24/7 online identity and data breach monitoring
- Unlimited VPN service to safeguard your privacy
- Password manager with private data protection
More Support
Community
Ask questions in our Community .
User Guides
Check the user guide for instructions.
Submit a Sample
Submit a file or URL for analysis.