Trojan:W32/Feedel
Summary
The Feedel trojan is downloaded onto a system by a separate downloader program, which will then proceed to execute Feedel. We detected the downloader as Trojan-Downloader:W32/Agent.
Removal
In most reported cases, the payload stored in the final encrypted section of the Feedel trojan's code is a LinkOptimizer.A tool for removing the LinkOptimizer is available from:
- LinkOptimizerRemovalTool.zip (Not signed by F-Secure)
To protect themselves from deletion, LinkOptimizer variants modify their file security permissions and registry key. Additional steps are required to successfully remove them from the system.
- Finding the Sample
- Launch the Registry Editor
- Navigate to the following:[HKLM\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\explorer.exe]
- Check to whic file the "Debugger" value points
Example Registry key:
- [HKLM\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\explorer.exe] Debugger="c:\windows\system32\jardrlmn.log"
Manual disinfection instructions:
- Start cmd.exe
- Kill the explorer.exe process from Task Manager
- Kill all processes that do not have SYSTEM or NETWORK SERVICE in the User Name column, EXCEPT the cmd.exe process
- Using cmd.exe, go to the folder where the malware sample is located, for example: cd windows\system32
- Add the necessary permission to the malware sample(Example: "cacls [filename] /G Everyone:F")
- Remove the read-only and other attributes of the malware sample(Example: "attrib -r -s -h")
- Delete the malware sample using cmd.exe(Example: "del [filename]")
- Launch the Registry Editor
- Navigate to[HKLM\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\explorer.exe]
- Add necessary permissions to the key by right-clicking on it, then selecting Permissions and selecting the Full Control checkbox
- Delete the key from the Registry
- Start explorer.exe
- Restart the system and check the Registry again. If the registry key is not present, the infection has been successfully removed
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
HZB.Feedel's actual payload depends on the type of malware which is stored in the final, encrypted section of its code, and is usually a LinkOptimizer or Trojan-Password stealer. DownloadThe actual download is performed by a small (usually 6000 to 7000 bytes) downloader with the mutex name "Global\__RST__". The downloader itself is usually packed with UPX.The downloader retrieves an encrypted data file (usually named aacaa.gif, aacab.gif or similar) from a malicious link. The name of the link varies, but usually appears as:
- https://[...]/pix/[filename].gif
The IP address of the malicious link is password-protected; in the sample we received, the password was "countermode.ws".Once downloaded onto the system, the downloader completely decrypts the data file. EncryptionAll the possible strings, API names and other details of the downloaded file are completely encrypted using the encryption algorithm RC4 block cipher. Before decryption, the data file appears as:
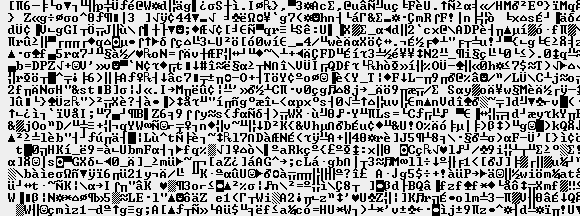
The data file is also protected by a password. The password appears as:
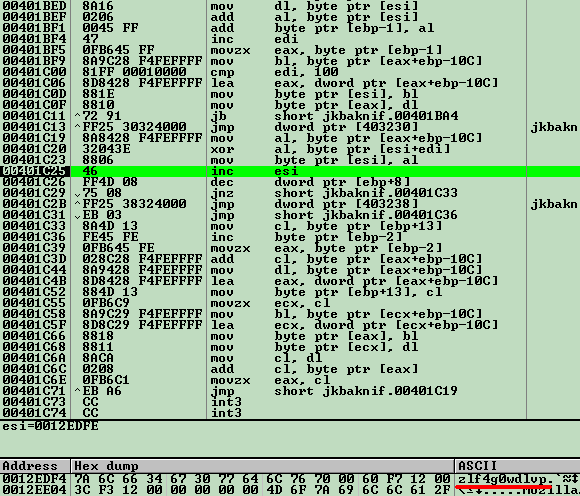
In the example shown, the password is "zlf4g0wdlv".The size of the password used for the encrypted data is usually around 10 characters. The strength of this password means that using a brute-force attack to crack it would take a long time. Simply guessing it would be almost impossible.After decryption, the same data file appears as:

The decrypted content is detected as a Trojan:W32/Feedel variant.
Execution
On execution, the downloader will decrypt the actual malware, which is contained in the last encrypted segment of content in the downloaded file, and is protected by a separate 9-byte long password. Once decrypted, the malware will lock itself to the hardware. The type of malware stored into this final segment may vary, but have usually been Linkoptimizers or Trojan-PSW malware.
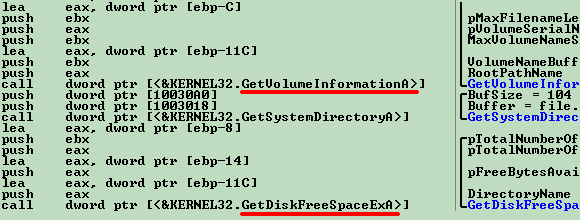
In the sample we analyzed, the trojan collects system information from the infected machine, specifically the serial number of the Windows drive and the size of the partition. Using this information, it then adds an additional layer of encryption and drops the malware in the temporary folder, using a value obtained from GetTickCount API for the filename.Feedel uses this information as an encryption/decryption RC4 key, to ensure that the malware cannot and will not be executed on any other machine. Incidentally, this also makes analysis very difficult to perform.Feedel uses the system temporary folder, %temp%. An example path is as follows:
- C:\%temp%\10874359.exeC:\Windows\Temp\10874359.exe
The temporary fileis then executed, after which boththe downloader andthe file that createdthe above mentionedfile will be deleted.
)
Protect your devices from malware with F‑Secure Total
Protecting your devices from malicious software is essential for maintaining online security. F‑Secure Total makes this easy, helping you to secure your devices in a brilliantly simple way.
- Award-winning antivirus and malware protection
- Online browsing, banking, and shopping protection
- 24/7 online identity and data breach monitoring
- Unlimited VPN service to safeguard your privacy
- Password manager with private data protection
More Support
Community
Ask questions in our Community .
User Guides
Check the user guide for instructions.
Submit a Sample
Submit a file or URL for analysis.