Trojan:W32/Dllpatcher.A
Summary
Trojan:W32/Dllpatcher modifies the dnsapi.dll file Windows module to point to a new hosts file it creates, which contains additional hostnames and IP addresses.
Removal
Based on the settings of your F-Secure security product, it will either move the file to the quarantine where it cannot spread or cause harm, or remove it.
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
Trojan:W32/Dllpatcher attempts to 'patch' or modify the dnsapi.dll file, a module that assists the DNS client service in the Windows operating system, essentially by caching the Domain Name System (DNS) names requested during a web browsing session. Due to its behavior, the trojan is also referred to as a 'DLL patcher'.
When active, this trojan will create a new hosts file that contains both the original hosts file values as well as additional prepended hostnames and IP addresses. The malware will then patch the dnsapi.dll file to point it to the newly created hosts file. Subsequently, the dnsapi.dll will refer to the new hosts file when attempting to map hostnames to IP addresses.
This trojan has been most commonly reported in France, though it is also noted in the United States, the Netherlands and a few other countries.
Distribution & installation
The DLL patcher is included in an installer file, which is most commonly downloaded and saved to the temp folder using the filename, extensionupdate.exe (SHA1: CA1EC9706C15C457F2515ED1921F85A348BFC5AD).
When the downloaded file is executed, it will drop and execute the DLL patcher. In the sample analyzed, the dropped file (SHA1:59BD1154FF4735B81DB038ECE54C230337533497) was named orion.exe. The orion.exe file also has the following component files:
- libnspr4.dll
- libplc4.dll
- libplds4.dll
- nss3.dll
- nssutil3.dll
- smime3.dll
File creation & execution
The orion.exe file creates the new hosts file in the %windir%/system32/ location, with a random directory and file name, for example:
- C:\WINDOWS\system32\neb\okhb\ vobg.dat
The path length of the new hosts file however must match the path length of the old hosts file. The new file uses a '.dat' extension and will contain the following prepended entries:
- 107.178.255.88 www.google-analytics.com
- 107.178.255.88 ssl.google-analytics.com
- 107.178.255.88 partner.googleadservices.com
- 107.178.255.88 google-analytics.com
- 107.178.248.130 static.doubleclick.net
- 107.178.247.130 connect.facebook.net
Next, the DLL patcher locates the dnsapi.dll file (either in %windir%\system32\ or %windir%\SysWOW64\) and modifies it to use the path of the new hosts file it created:
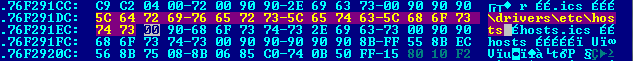
Original path for hosts file
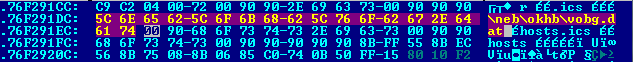
Patched path pointing to newly-created hosts file
To facilitate using the new hosts file, on the next system bootup the DLL patcher will use the following registry key to flush the DNS cache:
- HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce\cmdrun cmd.exe /C ipconfig /flushdns
This ensures that the information in the new hosts file does not conflict with older data in the DNS cache.
It will also create the following mutexes:
- Global\Matil da
- Global\Nople Mento
Security evasion
The DLL patcher attempts to evade monitoring by security products by checking for VMWare- and VBox-related registry keys:
- HKLM \ DESCRIPTION \ System \ BIOS vbox - HKLM \ DESCRIPTION \ System \ BIOS vmware
It also checks for the existence of SbieDll.dll (a component related to the Sandboxie virtual environment program) and for various VMware-related devices. If any of these are found on the infected machine, the malware exits and does nothing further.
Once the trojan has completed its tasks, its components are quietly deleted.