Trojan-Downloader:W32/MyDrill.A
Summary
MyDrill.A is detection for files used as part of a Malaysian Cyber Security Drill that took place during 2007. MyDrill.A are harmless test files. Detection was added for the purpose of the drill.
Removal
Based on the settings of your F-Secure security product, it will either move the file to the quarantine where it cannot spread or cause harm, or remove it.
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
On execution this trojan will download a second trojan file from:
- http://202.190[REMOVED]/gaga/2malware.html
It is saved as C:\malware.html and then later renamed and executed as C:\malware2.exe. The second trojan is also detected as Trojan-Downloader:W32/MyDrill.A.It will then create a copy of itself in the Window's System directory, usually C:\Windows\System32.It will then Show the following Message Box:
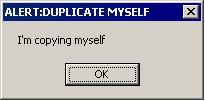
It then creates an autostart registry entry for the downloaded Trojan in:
- HKLM\Software\Microsoft\Windows\Currentversion\Run myDrill07_hi_analyst = %System%\malware2.exe
It also monitors the following active analyst tools and applications and shows a message box as an alert:
- Command Prompt
- Ethereal / WireShark
- Olly Debug
- Process Explorer
- Registry Editor
- RegShot
- Windows Task Manager
- WordPad
- ZoneAlarm
Example:
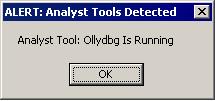
It then exits whenever one of the said tools are detected as running.With an additional anti-debugging check compared to the first trojan, the downloaded file when executed then downloads a third trojan from:
- http://202.190[REMOVED]/gaga/3-malware.html
The download is saved as C:\malware.html and then later renamed and executed as C:\malware3.exe. The third trojan is also detected as Trojan-Downloader:W32/MyDrill.A.It then copies itself to the Window's System directory as malware3.exe showing the same message box for notification. An autostart entry in the registry is then created for itself as:
- HKLM\Software\Microsoft\Windows\Currentversion\Run myDrill07_hi_analyst = %System%\malware3.exe
As the first trojan , this file then monitors active analysis tools and exits if it detects any, also showing similar message box as notification.The third trojan then downloads a none malicious file done.html from:
- http://202.190[REMOVED]/gaga/done.html
Similar to the first two trojans with the exception of the additional anti-debugging routines, this file then creates a autostart registry entry:
- HKLM\Software\Microsoft\Windows\Currentversion\Run myDrill07_hi_analyst = %System%\malware3.exe
It then actively monitors running analysis tools.It then displays the message box:
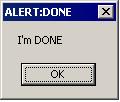
)
Protect your devices from malware with F‑Secure Total
Protecting your devices from malicious software is essential for maintaining online security. F‑Secure Total makes this easy, helping you to secure your devices in a brilliantly simple way.
- Award-winning antivirus and malware protection
- Online browsing, banking, and shopping protection
- 24/7 online identity and data breach monitoring
- Unlimited VPN service to safeguard your privacy
- Password manager with private data protection
More Support
Community
Ask questions in our Community .
User Guides
Check the user guide for instructions.
Submit a Sample
Submit a file or URL for analysis.