Trojan:Android/Zsone.A
Summary
Trojan:Android/Zsone.A sends SMS messages to premium-rate numbers related to subscription for SMS-based services.
Removal
Once the scan is complete, the F-Secure security product will ask if you want to uninstall the file, move it to the quarantine or keep it installed on your device.
Trojan:Android/Zsone.A can be uninstalled by following the steps below:
- Go to Settings
- Go to Applications
- Go to Manage Applications
- Select the application
- Press "Clear data"
- Press "Uninstall"
- Select "OK" when asked for confirmation and wait
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
The detection Trojan:Android/Zsone.A identifies a number of trojanized applications that were found on the Google Android Market in May 2011.
At the time of writing, these applications were already removed from the official Android Market, but could still be found in various forums and unofficial Android application distribution sites, most commonly catering to users in mainland China.
Installation
On installation, the affected applications display the following permissions requests:
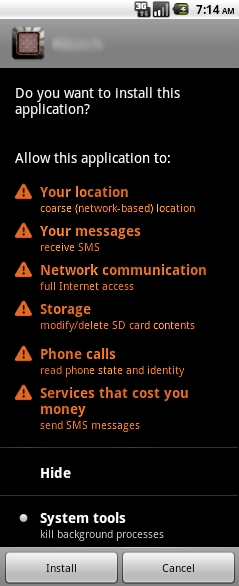
Payload
Trojan:Android/Zsone.A's malicious routine starts when the application itself is launched. On the fifth click/action performed in the app, Zsone.A's SMS-sending payload is triggered.
The trojan will silently send SMS messages to the following hard-coded premium-rate phone numbers:
- 10626213
- 10621900
- 106691819
- 1066185829
- 10665123085
The SMS messages observed so far contain the following text strings:
- aAHD
- 921X1
- 921X2
- 28AHD
- 95pAHD
- M6307AHD
These strings are used within Chinese mobile networks for subscribing to various paid SMS services. The trojan's behavior may result in registering the user's device to a service, thereby incurring unsolicited charges.
The trojan hides its SMS-sending activity from the user by aborting SMS messages received from the following numbers:
- 10086
- 10000
- 10010
- 1066133
- 10655133
- 10621900
- 10626213
- 106691819
- 1066185829
- 10665123085
- 10665123085
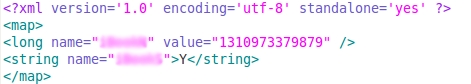
Zsone.A maintains a record of its SMS-sending status in an XML file in the shared preferences folder. When an SMS message is sent, the trojan saves a 'Y' ('Yes') in the XML file.
Other variant
- Trojan:Android/Zsone.C
)
Protect your devices from malware with F‑Secure Total
Protecting your devices from malicious software is essential for maintaining online security. F‑Secure Total makes this easy, helping you to secure your devices in a brilliantly simple way.
- Award-winning antivirus and malware protection
- Online browsing, banking, and shopping protection
- 24/7 online identity and data breach monitoring
- Unlimited VPN service to safeguard your privacy
- Password manager with private data protection
More Support
Community
Ask questions in our Community .
User Guides
Check the user guide for instructions.
Submit a Sample
Submit a file or URL for analysis.