Trojan:AndroidOS/AdSMS.A
Summary
Trojan:AndroidOS/AdSMS.A is distributed via a link embedded in a fake SMS; on clicking the link, the trojan's Android Package (APK) file is downloaded and installed onto the mobile device.
Removal
Once the scan is complete, the F-Secure security product will ask if you want to uninstall the file, move it to the quarantine or keep it installed on your device.
Trojan:AndroidOS/AdSMS.A can be uninstalled with the following steps:
- Go to Settings
- Go to Applications
- Go to Manage Applications
- Select "org.me.androidapplication1"
-
Press 'uninstall' and wait
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
The SMS appears to be targeted to Android users in mainland China, as it pretends to be from a mobile service provider in China and contains Chinese-language text, a translated example of which is as follows:
Dear customer of [network provider], your mobile phone contains security system vulnerability. To increase the security level, please download the updated patch! [link]
The link provided in the SMS leads to the APK for this trojan. At the time of writing, the APK uses the filename htc.apk.
Installation
The trojan is only installed if the user clicks on the link in the malicious SMS. Shown below are the permissions requested by the trojan:
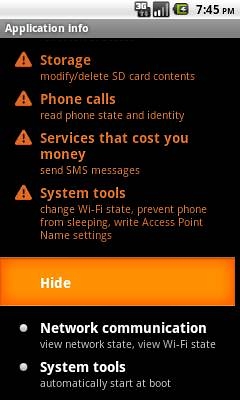
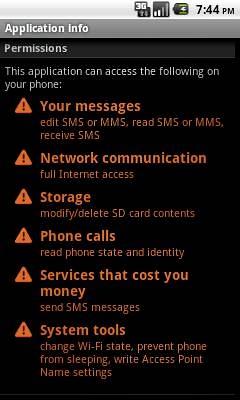
Permissions request by Trojan:AndroidOS/AdSMS.A
Once installed, no icon appears in the phone's applications menu to indicate the malware's presence on the phone, though the trojan will run in the background.
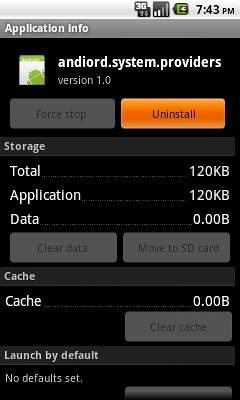
Users may detect its presence by checking the "Manage applications" menu under Settings for the application name andiord.system.providers:
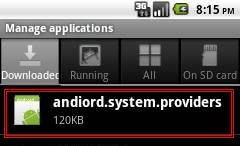
Trojan:AndroidOS/AdSMS.A's listed as 'andiord.system.providers'
Activity
While running, it will download an additional file and configuration file from various malicious sites:
- hxxp://adsms.itodo.cn/[...].aspx?
- hxxp://adsms.yywo.cn/[...].aspx?
- hxxp://adsms.1oo86.net/[...].aspx?
- hxxp://61.164.109.77/[...]/[...].apk
The trojan also obtains the following details from the phone:
- International Mobile Equipment Identity (IMEI)
- Phone number
- SDK version
- Network infromation
- Wi-Fi
And sends the details to remote servers.
The trojan is also capable of reading, writing and sending SMS messages and changing the phone's Wi-Fi state.
)
Protect your devices from malware with F‑Secure Total
Protecting your devices from malicious software is essential for maintaining online security. F‑Secure Total makes this easy, helping you to secure your devices in a brilliantly simple way.
- Award-winning antivirus and malware protection
- Online browsing, banking, and shopping protection
- 24/7 online identity and data breach monitoring
- Unlimited VPN service to safeguard your privacy
- Password manager with private data protection
More Support
Community
Ask questions in our Community .
User Guides
Check the user guide for instructions.
Submit a Sample
Submit a file or URL for analysis.