Worm:W32/Sobig
Summary
The Sobig worm was found in the wild on January 9th 2003. The worm spreads via email and network shared drives. It also tries to download other files from web pages located on a Geocities site.
Removal
Based on the settings of your F-Secure security product, it will either move the file to the quarantine where it cannot spread or cause harm, or remove it.
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
Update 2003-04-23 09:00 GMTIt has been reported that the webpage that controls the trojan downloader component of the worm had been updated for a period of time. The page pointed to a location containing a trojan (detected by F-Secure Anti-Virus as Backdoor.Delf.da). At the time of this update, the control page is no longer available.
Infection
When the worm is run on a system for the first time it copies itself to the Windows System Directory using the name winmgm32.exe. After this a new value, pointing to this file is added to the registry as
- HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\WindowsMGM
This way the worm will be started every time Windows starts.
Activity
Sobig contains a routine that downloads a text file from a website. The content of the file is used as a URL to download some program and run it on the infected machine. At the time of writing this description this feature is inactive, as the file points to a non-exisiting location.
The worm might affect network printers. In such cases printers might start to print garbage.
Propagation (email)
Email addresses are collected from files with various extensions:
- .WAB
- .DBX
- .HML
- .HTML
- .EML
- .TXT
The sender address is fixed, it is always big@boss.com.
Subjects are randomly chosen from the following list:
- Re: Here is that sample
- Re: Document
- Re: Sample
- Re: Movies
The message body says:
- Attached file:
The message contains an executable attachment. The attachment name can be one of the following:
- Sample.pif
- Untitled1.pif
- Document003.pif
- Movie_0074.mpeg.pif
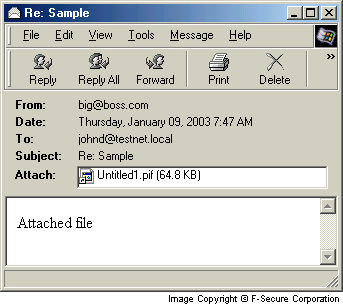
The infected emails are sent using the worms own STMP engine that is independent from the users email settings.
Propagation (Local Area Network)
Sobig lists all the network shares available to the infected computer and tries to copy itself to either of these directories:
- Windows\All Users\Start Menu\Programs\StartUp
or
- Documents and Settings\All Users\Start Menu\Programs\Startup
These are the default startup folders for Windows 9x and NT/XP based systems. If the worm is copied there Windows will run it next time the user logs in. This way the system gets infected.