Email-Worm:W32/Sober.B
Summary
Sober.B is an email worm that sends itself as an attachment to email messages with different subject and body texts. Messages are composed from either German or English text strings depending on a recipient's domain suffix. The worm also has the functionality to spread in P2P (peer-to-peer) networks.
Removal
Based on the settings of your F-Secure security product, it will either move the file to the quarantine where it cannot spread or cause harm, or remove it.
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
The worm is written in Visual Basic. The worm's file is packed with a modified version of UPX file compressor. It has its own SMTP engine and it is used to send out infected email messages.
Installation to system
When the worm's file is started, it shows a fake error message:
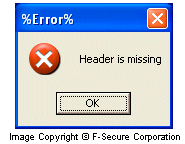
The worm copies itself to Windows System folder 3 times, once with SPOOL.EXE name, and 2 more times with semi-randomly generated names, for example RMDIAGEXAKE.EXE or MONWIUKDIR.EXE. The worm uses the following fixed text strings to generate the name of its files:
win svc task sys dll host end dir ms run ex log on reg ie 32 16 64 disk api app con mon drv crypt dat dx diag str xp hex
The worm also creates a file named MSCOLMON.OCX, where it stores email addresses harvested from an infected computer. The worm also creates a file named HUMGLY.LKUR in the same folder.
The worm creates several startup Registry keys for one of its semi-randomly named files in System Registry:
[HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
The worm also creates a startup key for its file in HKEY_USERS Registry tree:
[HKEY_USERS\[userID]\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
The subkey name that is created by the worm is semi-randomly generated. The value of a subkey is the path to one of the worm's files in Windows System folder.
The worm always has 2 of its tasks in System Memory. If one task is killed, it is immediately restarted by another one. Also the worm refreshes its startup keys in the Registry every few seconds. This makes manual disinfection of the worm more difficult. Is should be also noted that the worm blocks read access to its 2 semi-randomly named files and to MSCOLMON.OCX file as well.
Spreading in emails.
The worm scans files with certain extensions to harvest email addresses. Files with the following extensions are scanned:
htt rtf doc xls ini mdb txt htm html wab pst fdb cfg ldb eml abc ldif nab adp mdw mda mde ade sln dsw dsp vap php nsf asp shtml shtm dbx hlp mht nfo
The worm saves all found email addresses to MSCOLMON.OCX file located in Windows System folder. This is an ASCII file, not binary.
The worm sends email messages with German and English texts. When sending a message to an email address, that has domain suffix DE, CH, AT, LI, NL or BE, the worm uses German text strings, otherwise it composes a message in English. The worm sends the following English email messages:
Subject:
George W. Bush plans new wars
or
George W. Bush wants a new war
Body:
Bush plans new wars against China, Cuba and Iran. Please visit our website and vote against this very crazy war(s). More information:
Attachment:
www.gwbush-new-wars.com
----------------------
Subject:
You Got Hacked
or
Have you been hacked?
Body:
by me,, idiot! haha, very nice files on your system. i've made a website. i show your files on this website hahaha visit:
or
YA of me a great many files on your pc and very very interesting what would say the police?!,,, i don't know .-] i've files of you see:
Attachment:
www.hcket-user-pcs.com
or
yourlist.pif
or
allfiles.cmd
The worm sends the following German email messages:
Subject:
Hihi, ich war auf deinem Computer
or
Du bist Ge-Hackt worden
or
Ich habe Sie Ge-hackt
or
Der Kannibale von Rotenburg
Body:
Nette, ungewohnliche und ausgefallene Sachen hast du da auf deinem Computer! (Was soll man dazu noch sagen)
or
Ich uberlege mir schon die ganze Zeit, ob ich ein paar deiner Dateien im Internet auf einer Web-Seite stellen soll! Weil, genug Stoff habe ich ja von Dir! (Muhahahah) Du fragst dich sicherlich, was ich alles von Dir habe,,,, siehe selbst
or
Was wohl gewisse Behorden dazu sagen wurden? **hust* Ich wei? nicht so recht, soll ich dich bestechen oder die Behorden einschalten ??? Du kannst jetzt ruhig Deine Dateien loschen oder sonst was, aber nutzen wird es Dir wenig, weil ich sie auch habe! Wenn du meinst das ich Mist rede, dann sehe Dir die Datei-Liste an. Dann siehst du, was ich alles von Dir habe. Na ja,, ich melde mich nachste Woche noch einmal!
or
Entschuldigen Sie bitte diese uberaus deutliche Betreffzeile! Aber ein neuer Dialer macht mit dieser Uberschrift unzahlige User zu Opfern. Die User werden mit dem versprechen gelockt, sich das usserts abscheuliche Tat- Video anzuschauen zu durfen. Stattdessen aber, installiert sich ein sehr teurer Dialer und ein Virus auf dem PC. Da aber unzahlige User auf diese Finte hereinfallen, haben wir mit Zustimmung des Bundeskriminalamtes BKA, eine Web-Seite erstellt, wo einige dieser ausserts brisanten Fotos und Videos einzusehen sind, um den Leuten die Neugier zu nehmen. Naturlich sind diese Videos und Fotos leicht zensiert worden. Um auf diesen Web-Server zu gelangen, mussen Sie zuerst bestatigen, dass Sie das 18 Lebensjahr bereits vollendet haben. Wir bitten sie ausdrucklichst, keine Kinder diese Seite einsehen zu lassen. I.A.: Dieter Braun ----- MultiMedia AG Munchen ia. BKA (ORG. Rund-Mail V6.02) ----- Geschaftsfuhrer: Michael Leuningen (089/8941440) FAX: 089/89414434
Attachment:
Daten-Text.pif
or
DateiList.pif
or
Server.com
The worm modifies its attachment to fool CRC-based detection. It can adds random data to its file's end.
Spreading in file sharing networks
When active, the worm tries to locate shared folders of Kazaa, EMule and EDonkey2000. If such folders are located, the worm overwrites all executable files in those folders with its copy preserving the original file's size and name.
)
Protect your devices from malware with F‑Secure Total
Protecting your devices from malicious software is essential for maintaining online security. F‑Secure Total makes this easy, helping you to secure your devices in a brilliantly simple way.
- Award-winning antivirus and malware protection
- Online browsing, banking, and shopping protection
- 24/7 online identity and data breach monitoring
- Unlimited VPN service to safeguard your privacy
- Password manager with private data protection
More Support
Community
Ask questions in our Community .
User Guides
Check the user guide for instructions.
Submit a Sample
Submit a file or URL for analysis.