Redesi
Summary
Redesi is a mass mailer email worm. It was written in Visual Basic and the body is compressed with UPX packer. It affects Microsoft Outlook users mostly since it uses MAPI to spread.
Removal
Based on the settings of your F-Secure security product, it will either move the file to the quarantine where it cannot spread or cause harm, or remove it.
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
The worm comes as an email attachment. The emails sent by the worm look like this:
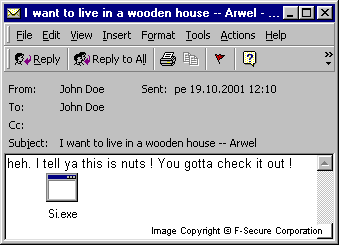
The subject lines are randomly chosen from the following list:
'Kev Gives great orgasms to ladeez!! -- Kev' 'hell is coming for u, u will be sucked into a bottomless pit!!! -- Gaz' 'Scientists have found traces of the HIV virus in cow's milk...here is the proof -- Will' 'Yay. I caught a fish -- Si' 'I don't want to write anything but Si is bullying me. -- Jim' 'Michelle still owes me 10 ... shit ! -- Si' 'Why have I only got cheese and onion crisps? I hate them !! -- Si' 'A new type of Lager / Weed variant...... sorted !' 'My dad not caring about my exam results -- by Michelle'
The attached filename can be 'Common.exe', 'rede.exe', 'Si.exe', 'UserConf.exe' or 'disk.exe'.
When the user opens the attachment the worm drops itself to c:\ with the following names: 'Common.exe', 'rede.exe', 'Si.exe', 'UserConf.exe' or 'disk.exe'. The files have hidden atribute so they are not visible in explorer by default.
After this it sends itself to the email addresses it can find in the user's Outlook address book.
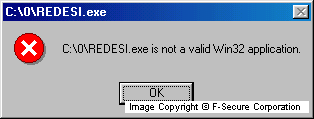
Finally it displays a fake error message to disgiuse the malicious activity.
Variant:Redesi.B (I-Worm.Redesi.b)
This variant of the Redesi worm is based on the same code. It differs from the original one in the subject lines and message body it uses. The messages look like they were forwarded messages from Microsoft Tech Support.
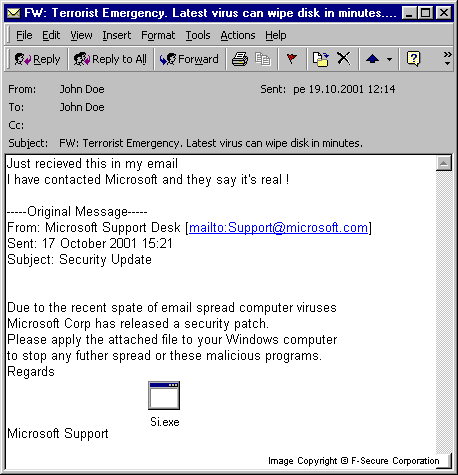
Subjects are chosen from this list:
'FW: Microsoft security update.' 'FW: Security Update by Microsoft.' 'FW: IT departments on state of HIGH ALERT.' 'FW: Terrorists release computer virus.' 'FW: Emergency response from Microsoft Corp.' 'FW: Terrorist Emergency. Latest virus can wipe disk in minutes.' 'FW: Microsoft Update. Final Release Candidate.' 'FW: New computer virus.'
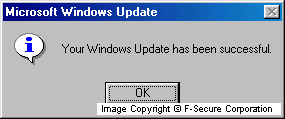
When it sent the messages it displays a fake message:
Payload
Redesi.b has a destructive payload. When it infects the machine it adds a value to the registry called
'HKLM\Software\Microsoft\Windows\CurrentVersion\Run\Rede'
and sets it to 'c:\rede.exe' so the worm will be started at each reboot.
If the date format is set to either dd/mm/yy or mm/dd/yy on 11th of November in 2001 it adds a some code to c:\autoexec.bat that will print a message:
'Bide ye the Wiccan laws ye must, In perfect love and perfect trust.'
This sentence is quoted from "The Complete Idiots Guide to Witchcraft and Wicca"
After this, the worm formats the hard drive after the next reboot.
Removal instructions
All the worm files from c:\ must be removed (see above) together with the modified registry values:
- 'HKLM\Software\Microsoft\Windows\CurrentVersion\Run\Rede'
- 'HKLM\Software\Microsoft\Windows\CurrentVersion\ErrorHandling\Rede'
F-Secure Anti-Virus with the latest updates can detect the worm.
)
Protect your devices from malware with F‑Secure Total
Protecting your devices from malicious software is essential for maintaining online security. F‑Secure Total makes this easy, helping you to secure your devices in a brilliantly simple way.
- Award-winning antivirus and malware protection
- Online browsing, banking, and shopping protection
- 24/7 online identity and data breach monitoring
- Unlimited VPN service to safeguard your privacy
- Password manager with private data protection
More Support
Community
Ask questions in our Community .
User Guides
Check the user guide for instructions.
Submit a Sample
Submit a file or URL for analysis.