Worm:W32/Mydoom
Summary
Mydoom is a worm that spreads over email and the Kazaa Peer-to-Peer (P2P) network.
Removal
Based on the settings of your F-Secure security product, it will either move the file to the quarantine where it cannot spread or cause harm, or remove it.
CAUTION Manual disinfection is a risky process; it is recommended only for advanced users.
-
Delete the following registry values and restart the
computer:
- HKLM\Software\Microsoft\Windows\CurrentVersion\Run\TaskMon]
- [HKLM\Software\Microsoft\Windows\CurrentVersion\Run\TaskMon]
- [HKCR\CLSID\{E6FB5E20-DE35-11CF-9C87-00AA005127ED}\InprocServer32]
-
Delete the worm from the Windows System Directory:
- %SysDir%\taskmon.exe
-
and its backdoor component from:
- %SysDir%\shimgapi.dll
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
When executed, the worm opens up Windows' Notepad with garbage data in it. When spreading, the infectious email used to distribute the worm copies use variable subjects, bodies and attachment names.
The worm encrypts most of the strings in it's UPX-packed body with ROT13 method, i.e. the characters are rotated 13 locations to the right in the abecedary, starting from the beginning if the position is beyond the last letter.
Mydoom also performs a Distributed Denial-of-Service attack on www.sco.com. This attack starts on 1st of February.
The worm opens up a backdoor to infected computers. This is done by planting a new SHIMGAPI.DLL file to system32 directory and launching it as a child process of EXPLORER.EXE.
Mydoom is programmed to stop spreading on February 12th.
For information on the B variant of Mydoom, see: http://www.f-secure.com/v-descs/mydoom_b.shtml
Activity
The worm will launch a Notepad window with garbage contents.
Registry
When run the worm will create a mutex with the name "SwebSipcSmtxSO" to ensure only one instance of itself is running at the same time.
The worm will copy itself to the Windows System folder as 'taskmon.exe' and adds a entry in the registry:
- [HKLM\Software\Microsoft\Windows\CurrentVersion\Run] "TaskMon" = %sysdir%\taskmon.exe
or, if it fails:
- [HKCU\Software\Microsoft\Windows\CurrentVersion\Run] "TaskMon" = %sysdir%\taskmon.exe
So it's run every time Windows starts up.
It drops another file, contained encoded in its body and packed with UPX as:
- %sysdir%\shimgapi.dll
This file will sequentially open TCP ports from 3127 to 3198, listening on them for incoming connections. One of the possibilities this backdoor offers is to receive an additional executable and run it on the already infected machine.
Expiration
When the worm is executed in a date after the Sunday 12th of February 2004 it will exit immediately, without performing any further actions. It will not, however, uninstall itself.
Propagation (Peer-to-Peer)
The worm will look up form the Windows' Registry the value containing the users Kazaa shared folder, and it will copy itself to that location with a filename composed from the following list:
- winamp5
- icq2004-final
- activation_crack
- strip-girl-2.0bdcom_patches
- rootkitXP
- office_crack
- nuke2004
And extensions chosen from:
- .bat
- .exe
- .scr
- .pif
Propagation (email)
The worm collects addresses where to send itself from Windows' Address Book and from files with extension:
- pl
- adb
- tbb
- dbx
- asp
- php
- sht
- htm
- txt
It try to bypass simple anti-spam protections i.e., like substituting the '@' symbol for ' at ' and several other combinations.
email messages sent by the worm have the following characteristics:
Subjects can be any of the following:
- test
- hi
- hello
- Mail Delivery System
- Mail Transaction Failed
- Server Report
- Status
- Error
Body is one of the following:
- test
- The message cannot be represented in 7-bit ASCII encoding and has been sent as a binary attachment.
- The message contains Unicode characters and has been sent as a binary attachment.
- Mail transaction failed. Partial message is available.
Attachments are composed combining the following names:
- document
- readme
- doc
- text
- file
- data
- test
- message
- body
with the following extensions:
- pif
- scr
- exe
- cmd
- bat
- zip
The ZIP file itself is not harmful when doubleclicked. Inside the zip you have a copy of the worm, sharing the same file name as the .zip. For example, message.zip contains message.exe.
The sizes of the ZIP files vary, but it's typically around 22kB. The infected file inside the zip can have double extensions, like "body.htm .pif".
The final message might look like presented in the following picture:
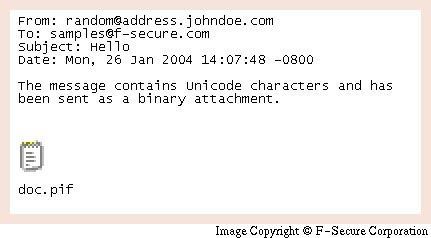
Payload
When the machine is booted after the Sunday 1st of February at 16:09:18 (UTC) (always according to the infected system's clock). A DDoS attack will be launched against SCO website.
The worm will launch 64 threads, each of them requesting the main page of the website www.sco.com. This process of requesting simultaneously 64 times the page will be repeated roughly every second (1024 milliseconds) from each of the infected machines throughout the globe. The request is a simple "GET / HTTP/1.1", aimed to overload their webserver.
Backdoor
The backdoor component of Mydoom.A is dropped to the System Directory with the filename 'shimgapi.dll'. The file is added to the registy as:
- [HKCR\CLSID\{E6FB5E20-DE35-11CF-9C87-00AA005127ED}\InprocServer32]
This registry value makes Explorer to load the DLL as an extension so it is not visible as a separate process in Task Manager.
The backdoor listens on the first available TCP port between 3127 and 3198. Connecting to that port a remote attacker can
- use the infected computer as a TCP proxy
- upload and execute arbitrary executables to the infected computer