Worm:W32/NetSky.B
Summary
Worm:W32/ NetSky.B (also known as Moodown.B) worm was found on 18th of February 2004. It is a minor variant of NetSky.A worm that appeared 2 days earlier.
Removal
Based on the settings of your F-Secure security product, it will either move the file to the quarantine where it cannot spread or cause harm, or remove it.
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
The worm spreads itself in emails inside a ZIP archive or as an executable attachment. It also copies itself to shared folders of all available drives. This allows the worm to spread in P2P (peer-to-peer) and local networks.
Installation
When the worm's file is run, it first shows a fake error messagebox:
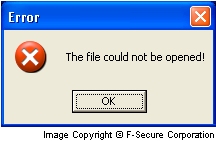
Then the worm copies itself to Windows directory with SERVICES.EXE name and creates a startup key for this file in System Registry:
- [HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] "service" = "%windir%\services.exe -serv"
where %windir% represents Windows directory. At the same time the worm also attempts to delete the following key values:
- [HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] "Taskmon" "Explorer" "system." "KasperskyAv"
- [HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] "Taskmon" "Explorer"
- [HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\RunServices] "system."
- [HKCR\CLSID\{E6FB5E20-DE35-11CF-9C87-00AA005127ED}\InProcServer32]
After that the worm starts looking for email addresses. It scans files with the following extensions on all available drives (c:-z:) except CD-ROM drives:
- .msg
- .oft
- .sht
- .dbx
- .tbb
- .adb
- .doc
- .wab
- .asp
- .uin
- .rtf
- .vbs
- .html
- .htm
- .pl
- .php
- .txt
- .eml
If the worm finds a folder with the 'sharing' or 'share' name, it copies itself to that folder with the following names:
- winxp_crack.exe
- dolly_buster.jpg.pif
- strippoker.exe
- photoshop 9 crack.exe
- matrix.scr
- porno.scr
- angels.pif
- hardcore porn.jpg.exe
- office_crack.exe
- serial.txt.exe
- cool screensaver.scr
- eminem - lick my pussy.mp3.pif
- nero.7.exe
- virii.scr
- e-book.archive.doc.exe
- max payne 2.crack.exe
- how to hack.doc.exe
- programming basics.doc.exe
- e.book.doc.exe
- win longhorn.doc.exe
- dictionary.doc.exe
- rfc compilation.doc.exe
- sex sex sex sex.doc.exe
- doom2.doc.pif
Propagation (email)
When Internet connection is available, the worm starts to spread itself. It creates ZIP archives with its file in Windows directory. The names of these ZIP archives are the same as the names of worm's files inside. The worm can use the following names for its attachments:
- document
- msg
- doc
- talk
- message
- creditcard
- details
- attachment
- me
- stuff
- posting
- textfile
- concert
- information
- note
- bill
- swimmingpool
- product
- topseller
- ps
- shower
- aboutyou
- nomoney
- found
- story
- mails
- website
- friend
- jokes
- location
- final
- release
- dinner
- ranking
- object
- mail2
- part2
- disco
- party
- misc
The worm can use one or two extensions for its attachments. For the first extension the worm uses the following:
- .txt
- .rtf
- .doc
- .htm
For the second extension the worm uses the following:
- .exe
- .scr
- .com
- .pif
The worm spreads itself in emails as a ZIP attachment or as an attachment with one of the above shown names. The subject of an infected email can be one of the following:
- hi
- hello
- read it immediately
- something for you
- warning
- information
- stolen
- fake
- unknown
The body text of an infected email can be one of the following:
- anything ok?
- what does it mean?
- ok
- i'm waiting
- read the details.
- here is the document.
- read it immediately!
- my hero
- here
- is that true?
- is that your name?
- is that your account?
- i wait for a reply!
- is that from you?
- you are a bad writer
- I have your password!
- something about you!
- kill the writer of this document!
- i hope it is not true!
- your name is wrong
- i found this document about you
- yes, really?
- that is bad
- here it is
- see you
- greetings
- stuff about you?
- something is going wrong!
- information about you
- about me
- from the chatter
- here, the serials
- here, the introduction
- here, the cheats
- that's funny
- do you?
- reply
- take it easy
- why?
- thats wrong
- misc
- you earn money
- you feel the same
- you try to steal
- you are bad
- something is going wrong
- something is fool
The worm's file is attached to the infected email inside a ZIP archive or as an normal binary file. A recipient has to unpack the worm's attachment from a ZIP archive and to run it or to run an executable attachment to get infected.