NetBus
Summary
NetAV is the worm that spreads in email messages. email addresses are collected from the users' Address Book and HTML files located in the 'Temporary Internet Files' folder. Every Tuesday the worm searches for *.DOC files in the 'My Documents' folder and, if there are several files there, picks one randomly and sends it out. The worm does not spread on Tuesday, it only sends *.DOC files out.
Removal
Based on the settings of your F-Secure security product, it will either move the file to the quarantine where it cannot spread or cause harm, or remove it.
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
Like most backdoors, NetBus has client and server components, and to function properly needs the server component to be installed on the remote system to be accessed. Once installed, Netbus allows a hacker to remotely access data and gain control over some Windows functions on the computer system.
Version 1.60 of NetBus server is a Windows PE file named PATCH.EXE. On execution, the server part installs itself to Windows directory and it will be executed automatically during the next Windows startup. The execution command for the server part is written to the registry:
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
The client part allows to control the remote computer system where the server part is installed and activated. The client part has a dialog interface which allows to perform tricks (some of them are really nasty) on remote system and to receive/send data, text and other information.
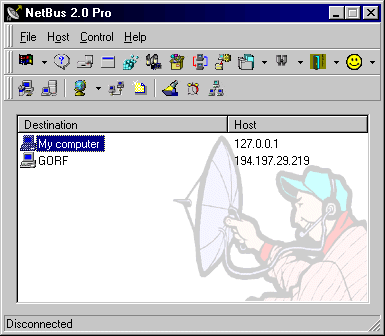
The client and server parts use TCP/IP protocol to communicate with each other. The client part has an option to scan a range of IP addresses to search for active server part and connect to it.
Below is a list of NetBus features:
1. Open/close the CD-ROM tray once or in intervals (specified in seconds); 2. Show optional BMP or JPG image (full path allowed); 3. Swap mouse buttons - the right button gets the left button's functions and vice versa; 4. Start optional application (full path allowed); 5. Play optional WAV sound-file (full path allowed); 6. Point the mouse to optional coordinates; 7. Show a message dialog on the screen and allow the user on remote system to answer it; 8. Shutdown Windows, reboot, logoff or power off; 9. Go to an optional URL within the default web-browser; 10. Send keystrokes to the active application on the target computer; 11. Listen for keystrokes on remote system and save them to file; 12. Get a screenshot from remote computer; 13. Return information about the target computer; 14. Upload any file to the target computer or update the server part of NetBus; 15. Increase and decrease the sound-volume; 16. Record sounds that the microphone catch - to listen what happens in the room where remote computer is; 17. Make click sounds every time a key is pressed; 18. Download and deletion of any file from the target system; 19. Blocking certain keys on the remote system keyboard; 20. Password-protection management of the remote server; 21. Show, kill and focus windows on remote system.
The server part takes steps to protect itself from being removed from the system - it hides its process name in Windows task manager and denies access to file on attempt to delete or rename it. When the server part is called with '/noadd' command line it will be not started every time Windows starts. When '/remove' command is passed to server part, it removes itself from the system.