ExploreZip.E
Summary
Explorezip.E is functionally similar to the variant that was widely spread in 1999. The main difference seems to be that the virus code has been repacked to make it undetectable to the current scanners.
On January 8th, 2003 a new variant of ExploreZip worm was found in the wild.
Removal
If ExploreZip worm is in a network environment, the whole network should be taken down to stop the worm's infecting attempts. Then all workstations should be disinfected separately. Only after every single workstation is clean, network connections can be re-enabled. The reason for such drastic measures is the following - the worm is a very fast infector. A single infected workstation can re-infect the whole network in a few minutes.
The second step is killing worm's processes in memory. To kill worm's processes, open Task Manager and kill processes with the following names:
- zipped_files.exe
- Explore.exe
- _setup.exe
Note that the worm's task is Explore.exe, do not confuse it with the main Windows component Explorer.exe!
After that the following files need to be deleted from a hard drive:
- %windir%\_setup.exe
- %winsysdir%\Explore.exe
where %windir% is Windows directory and %winsysdir% is Windows System directory.
The final step is removing worm's execution string from WIN.INI file on Windows 9x systems and from the Registry on Windows NT-based systems. This is done to get rid of annoying Windows messages about missing files.
Windows 9x systems
Open WIN.INI file located in Windows directory in any text editor and remove the worm's execution string after RUN= variable. It is advised to make a backup copy of your WIN.INI file before editing. Windows NT-based systems: open Registry Editor, locate the following key:
- [HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows]
Then delete 'run' variable in the above mentioned key. Please note that editing System Registry is not a simple task and this operation is not advised for inexperienced users.
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
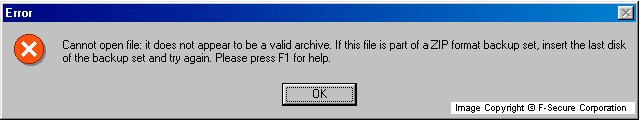
The worm is written in Delphi and is compressed with UPX file compressor. The packed file size is 91048 bytes, the unpacked file size is over 230 kilobytes. When the worm is run for the first time, it displays a fake error message:
Error Cannot open file: it does not appear to be a valid archive. If this file is part of a ZIP format backup set, insert the last disk of the backup set and try again. Please press F1 for help.
Then the worm copies itself as 'zipped_files.zip' file to the root folder of C: drive, opens this file with a default ZIP file viewer and then deletes the file. When a WinZip is installed on an infected system, it is started but because the worm deletes its file just after it tries to open it, WinZip shows that the 'zipped_files.zip' archive contents are empty. Then the worm installs itself to system. It copies itself as 'Explore.exe' to Windows System directory. It modifies WIN.INI file by putting its execution string after RUN= variable. This is done to make the worm's file during every Windows session. On NT-based system the worm adds its execution string to the Registry. On NT-based systems the worm can also install itself as '_setup.exe' in Windows directory, but this copy it not activated. To spread itself in email, the worm connects to an infected user's email client using MAPI interface, reads unanswered email messages and 'answers' them by sending itself to the original senders. The infected message looks like that:
Subject: RE:[the original subject of the message] Body: Hi ! I received your email and I shall send you a reply ASAP. Till then, take a look at the attached zipped docs. bye. Attachment: zipped_files.exe
The worm can alter the message body by adding a recipient's name after 'Hi' string. It can also add 'Sincerely' string followed by a sender's name in the end of message body. In this case the worm does not add 'bye.' to the end of the message body. The worm does not use Iframe trick to make its attachment run automatically on a target system, so it's spreading is limited. However, the social engineering used by the worm can trick many people to run the attached worm's file.
The worm can infect computers over a local network. The worm looks for computers that share resources with an infected system and if it finds such a computer, it looks for Windows folder there. If it is found, the worm copies itself as '_setup.exe' file to a remote computer and modifies WIN.INI file there. As a result, a remote computer will be infected with the worm when it is restarted. But only Windows 9x systems are vulnerable as WIN.INI file is not used to start programs on Windows NT-based systems. The worm has a dangerous payload. It is constantly looking for the files with the below listed extensions on all available drives:
- .DOC - Microsoft Word documents
- .XLS - Microsoft Excel spreadsheets
- .PPT - Microsoft PowerPoint presentations
- .ASM - Assembler source files
- .CPP - C++ source files
- .C - C source files
- .H - C header files
When the worm finds a file with one of those extensions, it overwrites it and then zeroes its length, so recovery becomes impossible.
)
Protect your devices from malware with F‑Secure Total
Protecting your devices from malicious software is essential for maintaining online security. F‑Secure Total makes this easy, helping you to secure your devices in a brilliantly simple way.
- Award-winning antivirus and malware protection
- Online browsing, banking, and shopping protection
- 24/7 online identity and data breach monitoring
- Unlimited VPN service to safeguard your privacy
- Password manager with private data protection
More Support
Community
Ask questions in our Community .
User Guides
Check the user guide for instructions.
Submit a Sample
Submit a file or URL for analysis.