Email-Worm:W32/Bagle.HR
Summary
This type of worm is embedded in an email attachment, and spreads using the infected computer's emailing networks.
Removal
Based on the settings of your F-Secure security product, it will either move the file to the quarantine where it cannot spread or cause harm, or remove it.
Manual disinfection of Bagle consists of the following steps:
- Delete the registry value [HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\d3dupdate.exe] and restart the computer
OR
- Terminate the running 'bbeagle.exe' process with Task Manager
- Then delete the worm's executable file from the Windows System Directory (%SysDir%\bbeagle.exe).
Remote Removal
F-Secure can confirm that the remote removal method found by Joe Stewart of Lurhq does indeed work (please note that the usage of this method against someone else's computers may be legally questionable).
Sending a specific byte sequence to port 6777 on the infected computers causes the worm to delete itself from the System Directory and terminate its process. The registry values are not removed but since the file does not exist Windows will ignore those.
The byte sequence to be sent:
- 0x43 0xff 0xff 0xff 0x00 0x00 0x00 0x00 0x04 0x31 0x32 0x00
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
Email-Worm:W32/Bagle.HR differs from previous Bagle variants in that it is itself capable of functioning as a trojan-downloader, rather than depending on a separate trojan-downloader program.
In addition, the worm uses rootkit technology to disguise its presence on the computer.
Execution
Upon executing for the first time, Bagle.HR it shows the following dialog box as a decoy:
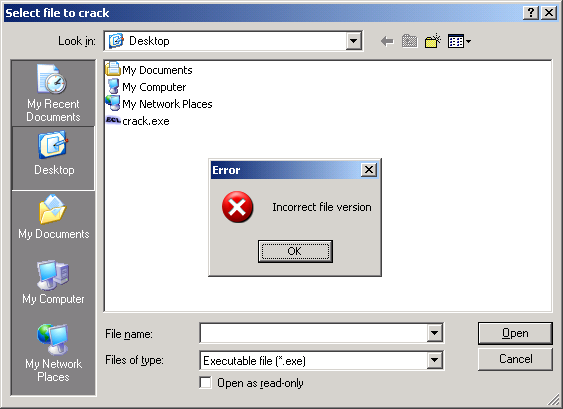
It will display the same message regardless of the file chosen.
In order to check itself for first execution, Bagle.HR checks the following registry entry:
- HKEY_CURRENT_USER\Software\FirstRRRun FirstRR23232Run = dword:00000001
If the said registry entry is available it will no longer show the dialog box.
Bagle.HR drops copies of itself in the following path and filename:
- %Local AppData folder%\hidires\flec003.exe
- %Local AppData folder%\hidires\hidr.exe
It also drops the following rootkit driver to hide its malicious activities:
- %Local AppData folder%\hidires\m_hook.sys
To enable automatic execution upon boot, it adds the following auto start entry but waits for 300000 ms before adding it:
- HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run drvsyskit = %Local AppData folder%\hidires\hidr.exe
It also adds its rootkit driver component as a service by adding the following changes to the registry:
- HKLM\SYSTEM\CurrentControlSet\Services\m_hook Type = dword:00000001 Start = dword:00000004 DisplayName = "Empty" ImagePath = %Local Application Data Folder%\hidires\m_hook.sys
Bagle.HR deletes the following key in order to prevent the user from booting into safe mode:
- HKLM\SYSTEM\CurrentControlSet\Control\SafeBoot
Activity
Bagle.HR downloads other malware from the following links:
- https://5050clothing.com/mu[REMOVED].php
- https://axelero.hu/mu[REMOVED].php
- https://calamarco.com/mu[REMOVED].php
- https://charlesspaans.com/mu[REMOVED].php
- https://chatsk.wz.cz/mu[REMOVED].php
- https://checkalertusa.com/mu[REMOVED].php
- https://cibernegocios.com.ar/mu[REMOVED].php
- https://cof666.shockonline.net/mu[REMOVED].php
- https://comaxtechnologies.net/mu[REMOVED].php
- https://concellodesandias.com/mu[REMOVED].php
- https://dev.jintek.com/mu[REMOVED].php
- https://dogoodesign.ch/mu[REMOVED].php
- https://donchef.com/mu[REMOVED].php
- https://erich-kaestner-schule-donaueschingen.de/mu[REMOVED].php
- https://foxvcoin.com/mu[REMOVED].php
- https://grupdogus.de/mu[REMOVED].php
- https://hotchillishop.de/mu[REMOVED].php
- https://ilikesimple.com/mu[REMOVED].php
- https://innovation.ojom.net/mu[REMOVED].php
- https://kisalfold.com/mu[REMOVED].php
- https://knickimbit.de/mu[REMOVED].php
- https://kremz.ru/mu[REMOVED].php
- https://massgroup.de/mu[REMOVED].php
- https://poliklinika-vajnorska.sk/mu[REMOVED].php
- https://svatba.viskot.cz/mu[REMOVED].php
- https://systemforex.de/mu[REMOVED].php
- https://uwua132.org/mu[REMOVED].php
- https://v-v-kopretiny.ic.cz/mu[REMOVED].php
- https://vanvakfi.com/mu[REMOVED].php
- https://vega-sps.com/mu[REMOVED].php
- https://vidus.ru/mu[REMOVED].php
- https://viralstrategies.com/mu[REMOVED].php
- https://Vivamodelhobby.com/mu[REMOVED].php
- https://vkinfotech.com/mu[REMOVED].php
- https://vproinc.com/mu[REMOVED].php
- https://vytukas.com/mu[REMOVED].php
- https://waisenhaus-kenya.ch/mu[REMOVED].php
- https://watsrisuphan.org/mu[REMOVED].php
- https://wbecanada.com/mu[REMOVED].php
- https://web-comp.hu/mu[REMOVED].php
- https://webfull.com/mu[REMOVED].php
- https://welvo.com/mu[REMOVED].php
- https://wvpilots.org/mu[REMOVED].php
- https://www.ag.ohio-state.edu/mu[REMOVED].php
- https://www.ag.ohio-state.edu/mu[REMOVED].php
- https://www.chapisteriadaniel.com/mu[REMOVED].php
- https://www.chittychat.com/mu[REMOVED].php
- https://www.cort.ru/mu[REMOVED].php
- https://www.crfj.com/mu[REMOVED].php
- https://www.kersten.de/mu[REMOVED].php
- https://www.kljbwadersloh.de/mu[REMOVED].php
- https://www.voov.de/mu[REMOVED].php
- https://www.walsch.de/mu[REMOVED].php
- https://www.wchat.cz/mu[REMOVED].php
- https://www.wg-aufbau-bautzen.de/mu[REMOVED].php
- https://www.wzhuate.com/mu[REMOVED].php
- https://xotravel.ru/mu[REMOVED].php
- https://yeniguntugla.com/mu[REMOVED].php
- https://zebrachina.net/mu[REMOVED].php
- https://zsnabreznaknm.sk/mu[REMOVED].php
The rootkit driver terminates and deletes the following files that are related to antivirus software:
- _AVP32.EXE
- _AVPCC.EXE
- _AVPM.EXE
- a2guard.exe
- aavshield.exe
- AckWin32.exe
- ADVCHK.EXE
- AhnSD.exe
- airdefense.exe
- ALERTSVC.EXE
- ALMon.exe
- ALOGSERV.EXE
- ALsvc.exe
- amon.exe
- Anti-Trojan.exe
- AntiVirScheduler
- AntiVirService
- ANTS.EXE
- APVXDWIN.EXE
- Armor2net.exe
- ashAvast.exe
- ashDisp.exe
- ashEnhcd.exe
- ashMaiSv.exe
- ashPopWz.exe
- ashServ.exe
- ashSimpl.exe
- ashSkPck.exe
- ashWebSv.exe
- aswUpdSv.exe
- ATCON.EXE
- ATUPDATER.EXE
- ATWATCH.EXE
- AUPDATE.EXE
- AUTODOWN.EXE
- AUTOTRACE.EXE
- AUTOUPDATE.EXE
- avciman.exe
- Avconsol.exe
- AVENGINE.EXE
- avgamsvr.exe
- avgcc.exe
- AVGCC32.EXE
- AVGCTRL.EXE
- avgemc.exe
- avgfwsrv.exe
- AVGNT.EXE
- avgntdd
- avgntmgr
- AVGSERV.EXE
- AVGUARD.EXE
- avgupsvc.exe
- avinitnt.exe
- AvkServ.exe
- AVKService.exe
- AVKWCtl.exe
- AVP.EXE
- AVP32.EXE
- avpcc.exe
- avpm.exe
- AVPUPD.EXE
- AVSCHED32.EXE
- avsynmgr.exe
- AVWUPD32.EXE
- AVWUPSRV.EXE
- AVXMONITOR9X.EXE
- AVXMONITORNT.EXE
- AVXQUAR.EXE
- BackWeb-4476822.exe
- bdmcon.exe
- bdnews.exe
- bdoesrv.exe
- bdss.exe
- bdsubmit.exe
- bdswitch.exe
- blackd.exe
- blackice.exe
- cafix.exe
- ccApp.exe
- ccEvtMgr.exe
- ccProxy.exe
- ccSetMgr.exe
- CFIAUDIT.EXE
- ClamTray.exe
- ClamWin.exe
- Claw95.exe
- Claw95cf.exe
- cleaner.exe
- cleaner3.exe
- CliSvc.exe
- CMGrdian.exe
- cpd.exe
- DefWatch.exe
- DOORS.EXE
- DrVirus.exe
- drwadins.exe
- drweb32w.exe
- drwebscd.exe
- DRWEBUPW.EXE
- ESCANH95.EXE
- ESCANHNT.EXE
- ewidoctrl.exe
- EzAntivirusRegistrationCheck.exe
- F-AGNT95.EXE
- F-PROT95.EXE
- F-Sched.exe
- F-StopW.EXE
- FAMEH32.EXE
- FAST.EXE
- FCH32.EXE
- FireSvc.exe
- FireTray.exe
- FIREWALL.EXE
- fpavupdm.exe
- freshclam.exe
- FRW.EXE
- fsav32.exe
- fsavgui.exe
- fsbwsys.exe
- fsdfwd.exe
- FSGK32.EXE
- fsgk32st.exe
- fsguiexe.exe
- FSM32.EXE
- FSMA32.EXE
- FSMB32.EXE
- fspex.exe
- fssm32.exe
- gcasDtServ.exe
- gcasServ.exe
- GIANTAntiSpywareMain.exe
- GIANTAntiSpywareUpdater.exe
- GUARD.EXE
- GUARDGUI.EXE
- GuardNT.exe
- HRegMon.exe
- Hrres.exe
- HSockPE.exe
- HUpdate.EXE
- iamapp.exe
- iamserv.exe
- ICLOAD95.EXE
- ICLOADNT.EXE
- ICMON.EXE
- ICSSUPPNT.EXE
- ICSUPP95.EXE
- ICSUPPNT.EXE
- IFACE.EXE
- INETUPD.EXE
- InocIT.exe
- InoRpc.exe
- InoRT.exe
- InoTask.exe
- InoUpTNG.exe
- IOMON98.EXE
- isafe.exe
- ISATRAY.EXE
- ISRV95.EXE
- ISSVC.exe
- JEDI.EXE
- KAV.exe
- kavmm.exe
- KAVPF.exe
- KavPFW.exe
- KAVStart.exe
- KAVSvc.exe
- KAVSvcUI.EXE
- KMailMon.EXE
- KPfwSvc.EXE
- KWatch.EXE
- livesrv.exe
- LOCKDOWN2000.EXE
- LogWatNT.exe
- lpfw.exe
- LUALL.EXE
- LUCOMSERVER.EXE
- Luupdate.exe
- MCAGENT.EXE
- mcmnhdlr.exe
- mcregwiz.exe
- Mcshield.exe
- MCUPDATE.EXE
- mcvsshld.exe
- MINILOG.EXE
- MONITOR.EXE
- MonSysNT.exe
- MOOLIVE.EXE
- MpEng.exe
- mpssvc.exe
- MSMPSVC.exe
- myAgtSvc.exe
- myagttry.exe
- navapsvc.exe
- NAVAPW32.EXE
- NavLu32.exe
- NAVW32.EXE
- NDD32.EXE
- NeoWatchLog.exe
- NeoWatchTray.exe
- NISSERV
- NISUM.EXE
- NMAIN.EXE
- nod32.exe
- nod32krn.exe
- nod32kui.exe
- NORMIST.EXE
- notstart.exe
- npavtray.exe
- NPFMNTOR.EXE
- npfmsg.exe
- NPROTECT.EXE
- NSCHED32.EXE
- NSMdtr.exe
- NssServ.exe
- NssTray.exe
- ntrtscan.exe
- NTXconfig.exe
- NUPGRADE.EXE
- NVC95.EXE
- Nvcod.exe
- Nvcte.exe
- Nvcut.exe
- NWService.exe
- OfcPfwSvc.exe
- OUTPOST.EXE
- PAV.EXE
- PavFires.exe
- PavFnSvr.exe
- Pavkre.exe
- PavProt.exe
- pavProxy.exe
- pavprsrv.exe
- pavsrv51.exe
- PAVSS.EXE
- pccguide.exe
- PCCIOMON.EXE
- pccntmon.exe
- PCCPFW.exe
- PcCtlCom.exe
- PCTAV.exe
- PERSFW.EXE
- pertsk.exe
- PERVAC.EXE
- PNMSRV.EXE
- POP3TRAP.EXE
- POPROXY.EXE
- prevsrv.exe
- PsImSvc.exe
- QHM32.EXE
- QHONLINE.EXE
- QHONSVC.EXE
- QHPF.EXE
- qhwscsvc.exe
- RavMon.exe
- RavTimer.exe
- Realmon.exe
- REALMON95.EXE
- Rescue.exe
- rfwmain.exe
- Rtvscan.exe
- RTVSCN95.EXE
- RuLaunch.exe
- SAVAdminService.exe
- SAVMain.exe
- savprogress.exe
- SAVScan.exe
- SCAN32.EXE
- ScanningProcess.exe
- sched.exe
- sdhelp.exe
- SERVIC~1.EXE
- SHSTAT.EXE
- SiteCli.exe
- smc.exe
- SNDSrvc.exe
- SPBBCSvc.exe
- SPHINX.EXE
- spiderml.exe
- spidernt.exe
- Spiderui.exe
- SpybotSD.exe
- SPYXX.EXE
- SS3EDIT.EXE
- stopsignav.exe
- swAgent.exe
- swdoctor.exe
- SWNETSUP.EXE
- symlcsvc.exe
- SymProxySvc.exe
- SymSPort.exe
- SymWSC.exe
- SYNMGR.EXE
- TAUMON.EXE
- TBMon.exe
- TC.EXE
- tca.exe
- TCM.EXE
- TDS-3.EXE
- TeaTimer.exe
- TFAK.EXE
- THAV.EXE
- THSM.EXE
- Tmas.exe
- tmlisten.exe
- Tmntsrv.exe
- TmPfw.exe
- tmproxy.exe
- TNBUtil.exe
- TRJSCAN.EXE
- Up2Date.exe
- UPDATE.EXE
- UpdaterUI.exe
- upgrepl.exe
- Vba32ECM.exe
- Vba32ifs.exe
- vba32ldr.exe
- Vba32PP3.exe
- VBSNTW.exe
- vchk.exe
- vcrmon.exe
- VetTray.exe
- VirusKeeper.exe
- VPTRAY.EXE
- vrfwsvc.exe
- VRMONNT.EXE
- vrmonsvc.exe
- vrrw32.exe
- VSECOMR.EXE
- Vshwin32.exe
- vsmon.exe
- vsserv.exe
- VsStat.exe
- WATCHDOG.EXE
- WebProxy.exe
- Webscanx.exe
- WEBTRAP.EXE
- WGFE95.EXE
- Winaw32.exe
- winroute.exe
- winss.exe
- winssnotify.exe
- WRADMIN.EXE
- WRCTRL.EXE
- xcommsvr.exe
- zatutor.exe
- ZAUINST.EXE
- zlclient.exe
- zonealarm.exe