BO2K
Summary
Back Orifice 2000 is a new version of the famous Back Orifice backdoor trojan (hacker's remote access tool). It was created by the Cult of Dead Cow hackers group in July 1999. Originally the BO2K was released as a source code and utilities package on a CD-ROM. There are reports that some files on that CD-ROM were infected with CIH virus, so the people who got that CD might get infected and spread not only the compiled backdoor, but also the CIH virus.
Removal
Based on the settings of your F-Secure security product, it will either move the file to the quarantine where it cannot spread or cause harm, or remove it.
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
The first binary version of BO2K was compiled and spread in the US. A few days later there appeared an international version of this backdoor. With the time there may appear lots of versions of BO2K with different compilers and having different features.
As its previous versions, the Back Orifice 2000 backdoor has 2 major parts: client and server. The server part needs to be installed on a computer system to gain access to it with the client part. The client part connects to the server part via network and is used to perform a wide variety of actions to remote system. The client part has a dialog interface that eases the process of hacking of the remote computer.
Here's the screenshot of the client part.

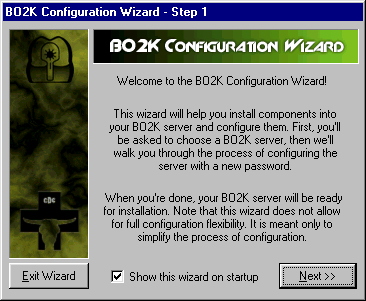
In the same package there comes also a configuration utility that is used to configure the server part of BO2K. By default the server part doesn't install itself to system being run. It should be properly configured to be used as a backdoor. The configuration utility has a wizard that helps to quickly configure the server part. It asks the user to specify networking type (TCP or UDP), port number (1-65535), connection encryption type - simple (XOR) or strong (3DES) and password for encryption that will be the password for the server access also.
Here's the screenshot of the BO2K configuration wizard.
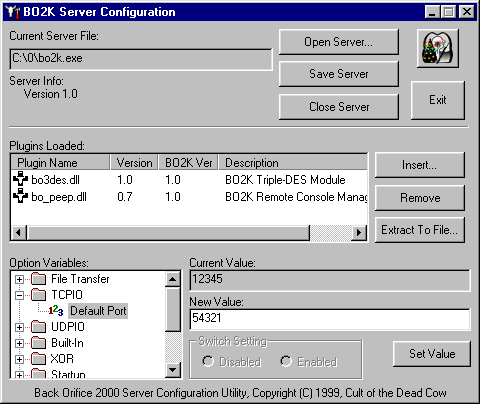
The configuration utility allows to flexibly configure the server part. It can add or remove plugins (DLLs) from the server application, configure file transfer properties, TCP and UDP settings, built-in plugins activation, encryption key, and startup properties. The startup properties setup allows to configure automatic installation to system, server file name, process name, process visibility and also NT-specific properties (NT service and host process names).
Here's the screenshot of BO2K configuration utility.
When the server part is configured to act like a trojan i.e. to install itself hideously to someone's system it writes itself to \Windows\System\ or \WinNT\System32\ folders under a name specified during configuration (default is UMGR32.EXE). Then it modifies the Registry. Under Windows 95/98 server execution string is written to:
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunServices
under Windows NT the execution string is written to:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
Then the file from which the server part started can be deleted (if it was specified during configuring). After that the BO2K will be active in memory each time Windows starts and will provide access to the infected system for hackers who have the client part and the correct password.
Being active the server part can hide its process or prevent its task to be killed from Task Manager (on NT). The backdoor uses a smart trick on NT by constantly changing its PID (process ID) and by creating the additional process of itself that will keep the backdoor alive even if one of the processes is killed. Besides, the server part adds a random (but large) number of spaces and 'e' at the end of its name, so the server part file can't be deleted from Windows (invalid or long name error occurs) though disk checking utilities don't find any problems with filename. The server part file can be only deleted from DOS or DOS session (if the file is not locked of course).
Back Orifice 2000 like its ancestors has a lot of features. But unlike the older versions the BO2K has many improvements: connection encryption (including strong 3DES), ability to work under NT, to use UDP, to allow internal plugins in DLL format, a more advanced security, more remote system control features.
Here's the list of Back Orifice 2000 capabilities:
1.
Ping and querry server part version
2.
Rebooting, locking up system, listing of passwords (yes, itworks - passwords are retrieved from memory), geting systeminfo
3.
Logging keyboard activities, operations with log file: view,delete
4.
Opening a messagebox with specified text and title
5.
Mapping TCP ports to another IP, console application, HTTPfileserver, filename, listing of mapped ports and TCP filesending
6.
Adding and removing network shares, listing of shares(including LAN), mapping of shared devices, listing of activeconnections
7.
Process control (works under NT as well): list, kill, start
8.
Full access to Registry (though the way it is done is notconvenient - all keys should be typed manually)
9.
Playing WAV files (looped playback is possible), capturingscreen, AVI and video still
10. Full disk access: listing of directories and files, finding,viewing, deleting, moving, copying of files and folders,transfer list maintenance
11. Remote compression and decompression of files (to receive bigfiles from remote system)
12. Resolving full host name and IP address
13. Flexible server control including each plugins control,command sockets manager
14. Possibility to run any plugins ('buttplugs') and to activateany functions in them with specified parameters. For exampleone plugin can initiate a video stream and 'highjack' aremote system.
The US version has some serious bugs - sometimes installation of the backdoor fails under NT. On NT shutdown an error messagebox is displayed for some time.