Babylonia
Summary
Babylonia is a memory resident Windows-based virus with worm and automatic update capabilities. The virus infects PE EXE (Windows Portable Executables) and HLP (Windows Help files). It also patches Windows socket library WSOCK32.DLL to send its copies to Internet and drops additional component that is able to download and install 'virus plugins' from Internet.
Removal
Based on the settings of your F-Secure security product, it will either move the file to the quarantine where it cannot spread or cause harm, or remove it.
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
The virus uses VxD calls that are allowed on Win9x computers only, so it is not able to infect WinNT stations and servers. The virus uses several features that are already found in other computer viruses and worms: global network spreading (I-Worm.Happy/SKA worm), Windows Help file infection (WinHLP.Demo), installation into Windows memory (Win95/CIH), e.t.c.
When an infected EXE file is run, the virus installs its resident copy into Windows memory, drops and runs an additional file (update component) and returns control to the host program.
To install itself into memory the virus scans Windows kernel, gets necessary Windows functions addresses and installs itself as a system driver (VxD). It allocates a block of Windows VxD memory, copies itself to there and hooks IFS API (disk file access functions). To switch its code from application level to system drivers (from Ring3 to Ring0) the virus uses a standard trick with system interrupt description tables that was first introduced by CIH virus.
The virus then creates an additional PE EXE file 4 kb long in root directory of drive C: - C:\BABYLONIA.EXE. This is a standalone virus component that provides additional virus functions. The virus stores the image of this file in a compressed form, so it occupies less than 2 kb in virus body. The virus uses 'aPLib' compression method for this file as well as for its other components (plugins).
The virus IFS API hooker intercepts three types of file access functions: reading/modifying file attributes, file opening and renaming. When an PE EXE file is accessed the virus checks its internal format and writes itself to the end of last file section while increasing its size. In some cases when the file has large enough Fixup section the virus disables this section and writes itself into it. In this case the size of infected file is not increased.
To get control when infected files are run the virus does not modify program's start address, but patches the file entry routine. The virus uses 'Entry Point Obscuring' technology: it scans file startup code and overwrites it at some position with a call to virus body.
While infecting Windows HLP file the virus creates a script routine there which is activated each time this help file is accessed by Windows help system: the virus modifies internal HLP file structure, adds its script to the 'SYSTEM' area, converts its code to polymorphic start-up routine and includes it into the script.
While infecting the WSOCK32.DLL library the virus looks for 'Send' function and patches it with a short routine that instructs the memory resident virus copy to spread itself. When patched WSOCK32.DLL is loaded the virus filters data that is being sent, and when messages are sent out, the virus attaches its copy to them. When infected message are received the virus attachment looks like that:
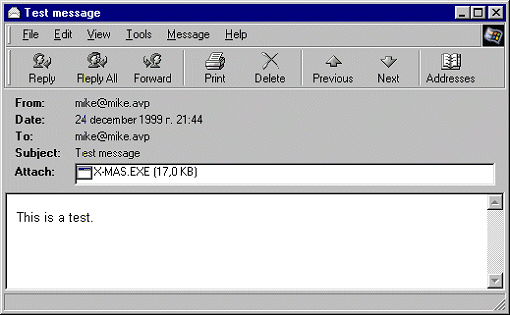
If a message already has an attachment, the virus appends it anyway and the message as a result might has two or more attached files including the virus.
The virus body attached to an infected message is a Win32 PE executable X-MAS.EXE. The virus routine performs selection from six possible name variants depending on the current month, but fails due to a bug and as a result the file name is always X-MAS.EXE. The copmlete list of names looks like that:
I-WATCH-U BABILONIA X-MAS SURPRISE! JESUS BUHH CHOCOLATE
This file itself is about 17 Kb long (6Kb of host file and 11Kb of virus code, the virus does not infect files that are smaller than 8Kb, but it makes an exception exactly for X-MAS.EXE file that is spread as an attachment). When this file is run, the virus installs itself into system and returns control to the host program. The X-MAS.EXE file then opens all files in current directory, Windows, and Window system directories. The virus resident copy is already installed, and as a result PE EXE files in these directories become infected. The X-MAS.EXE file has the following icon (here it is enlarged for your convenience):
Before its termination the host file then displays 2 fake error messageboxes:
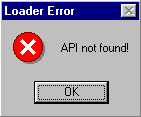
and
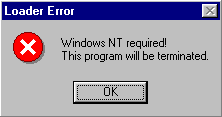
Under Windows 95/98 the virus displays the above messagebox, but under Windows NT, the 'NT' is changed to '95' to show 'incompatibility' with user's operating system.
As mentioned above the virus drops C:\BABYLONIA.EXE file that acts as an update component to the virus. This is standalone program that is not linked to the virus directly. The virus does not infect this file as it is about 4 kb long (and the virus does not infect files smaller than 8 kb).
When the BABYLONIA.EXE file is run, it registers itself as a 'service process' that is not visible in the task list. Then it copies itself to Windows system directory as KERNEL32.EXE (do not confuse with a standard Windows library - KERNEL32.DLL) and registers this file in the auto-run section of the system registry to be run during all further Windows startups:
HKLM\Software\Microsoft\Windows\CurrentVersion\Run
Then the update component connects to hacker's website based in Japan and gets the 'vecna/virus.txt' file from there. This file contains the list of additional virus components (plugins). The update component then downloads these files one by one and processes them. In case there is no connection to Internet, or the website or plugin files are not accessible, the update component stays resident in Windows memory and each minute tries to connect to that site and get the files. When all files are downloaded and processed, the update component exits.
The files on the hacker's website have a special format - header ID stamp 'VMOD', then version stamp, and address of 'main' routine in the file. These 'main' routines in files are Win32 programs, the virus locates them and passes control to their code. As a result data files from hacker's website are downloaded and run as 'virus plugins' and by using these plugins the virus author is able to operate with infected computers - to upgrade the virus, to installs trojans and backdoors, to corrupt data, e.t.c.
At the moment of this description creation there were four plugins known. The first one with DROPPER.DAT name creates the C:\INSTALAR.EXE file, writes program code there, runs it and then deletes the file. This EXE file is the same one that is sent in attached files. So, if the system is disinfected from the virus, but the update component is installed on the computer, it will download and reinstall the virus to a cleaned system.
The second file (GREETZ.DAT) checks date and time and starting from 15th of January, from 5:00 till 20:00 local time writes to the C:\AUTOEXEC.BAT file the set of commands that will display the following message:
W95/Babylonia by Vecna (c) 1999 Greetz to RoadKil and VirusBuster Big thankz to sok4ever webmaster Abracos pra galera brazuca!!! --- Eu boto fogo na Babilonia!
The third plugin (IRCWORM.DAT) installs a mIRC worm to the system that tries to spread itself via IRC channels as '2kBug-MircFix.EXE' and '2kbugfix.ini' files. But the worm seems to have a bug and can't spread because of that.
The fourth plugin (POLL.DAT) informs virus author about infected computer: it sends a message to 'babylonia_counter@hotmail.com' address. The message text looks like this:
Quando o mestre chegara?
These messages are not intercepted by the virus resident copy, and they do not become infected with the virus. To prevent duplicate postings the virus creates the '05_12_99' file in the Windows system directory and if this file already exists the plugin exits with no Email messages are sent.