Agent.AUM
Summary
Agent.AUM is a trojan that drops and executes several other malware files onto the computer system.
In general, trojan droppers are usually standalone programs that drop different types of standalone malware (trojans, worms, backdoors) to a system. A typical trojan dropper is a file that contains a few other files compressed inside its body. When a trojan dropper is run, it extracts all files it contains to a folder (usually temporary folder) and runs all of them simultaneously.
Aside from being a dropper, this trojan also has the ability to steal usernames, passwords, and other system information from the victim's computer.
Removal
Based on the settings of your F-Secure security product, it will either move the file to the quarantine where it cannot spread or cause harm, or remove it.
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
Agent.AUM is a Themida packed trojan that arrives on the system with the filename of Windows Genuine Advantage Patch.exe.
Upon execution, it drops the following files in the Windows System directory:
- ldapi32.exe (17 KB) - Detected as Backdoor.Win32.Cakl.a
- ntcvx32.dll (22 KB) - Detected as Trojan-Spy.Win32.Delf.qb
- ntswrl32.dll (9 KB) - Detected as Backdoor.Win32.Cakl.a
- vssms32.exe (1,696 KB) - A copy of itself
It checks the existence of the following mutex to ensure that there's only one instance of itself running in memory:
- TURKO3
In creates the following autostart registry entry:
- [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]vssms32 = "{systemdir}\vssms32.exe"
It also creates the following registry entry to allow itself to bypass the Windows Firewall:
- [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile\AuthorizedApplications\List] {systemdir}\vssms32.exe = "{systemdir}\vssms32.exe:*:Enabled:Dnode"
It modifies the following registry keys:
- [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal]
- [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\Network]
- and changes them it to:
- [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\minimal.xxx]
- [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\network.xxx]
This is done in order to prevent the user from successfully booting into Safe Mode.
This trojan tries to steal user account names and passwords of the following known applications:
- Firefox
- ICQ
- Internet Explorer
- MSN Messenger
- Outlook
- RAS
It also tries to get system information such as:
- CapsLock State
- Computer Name
- CPU Name
- CPU Speed
- Free Disk Space
- Local Host Name
- NumLock State
- Operating System
- Resolution
- Screen Captures of the System
- ScrollLock State
- Temporary and System Folders Location
- User Name
- Windows Language
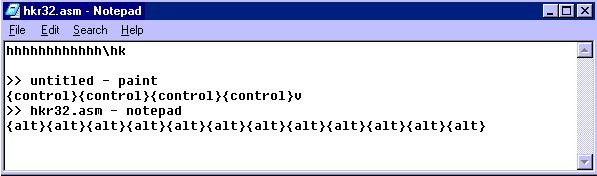
Agent.AUM also attempts to log keystroke events and saves them to the following file located at the Windows folder:
- HKR32.ASM
Below is an example of the HKR32.ASM file. It shows the user's logged keystrokes:
)
Protect your devices from malware with F‑Secure Total
Protecting your devices from malicious software is essential for maintaining online security. F‑Secure Total makes this easy, helping you to secure your devices in a brilliantly simple way.
- Award-winning antivirus and malware protection
- Online browsing, banking, and shopping protection
- 24/7 online identity and data breach monitoring
- Unlimited VPN service to safeguard your privacy
- Password manager with private data protection
More Support
Community
Ask questions in our Community .
User Guides
Check the user guide for instructions.
Submit a Sample
Submit a file or URL for analysis.