Redirected hosts file
Summary
This detection is triggered when an entry in your hostsfile redirects a particular IP address to a different host. A redirected hostsfile entry is a common action performed by various malware.
Removal
Once detected, the F-Secure security product will automatically handle a harmful program or file by either blocking or asking the user for a desired action.
Exclude an intentionally modified hosts file
Based on the settings of your hosts file that has been intentionally modified by the user will still trigger this detection. In such cases, you can exclude the hosts file from further scanning. To do so:
-
Select the radio button
I want to decide:
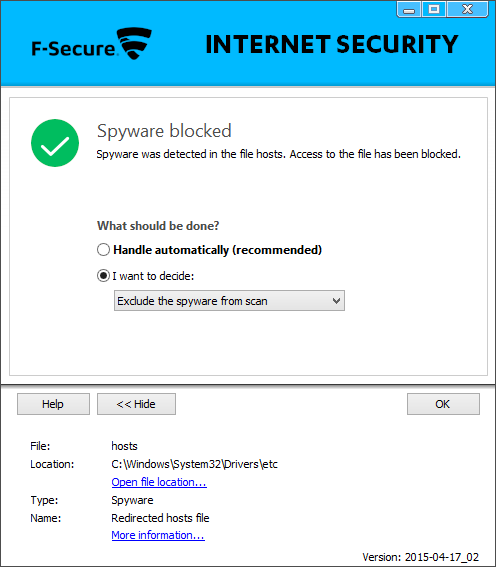
-
Then select the option
Exclude the spyware from scan from the
drop-down menu
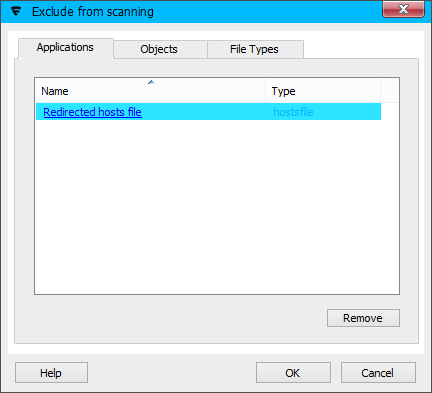
The hosts file will be excluded from subsequent scanning and appear in the product's Excluded Applications list.
The exclusion can be reversed by removing the file from the Excluded Applications list in the future, at your own discretion.
You may also refer to F-Secure Community: How to allow a quarantined hosts file and exclude the file from scanning for additional information on excluding files from scanning.
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
A hosts file is a 'directory' of hostnames and their IP addresses that is used by the operating system to easily find resources, such as other computers or websites.
Maliciously modified hosts file
Modifying and redirecting hosts file entries is a common tactic used by malware to silently send users to an unwanted website. Often, this is used to expose the user's machine to web-based attacks, as well as exposing the user to unsolicited and/or malicious content.
In other cases, the modification is made to prevent the user from accessing certain sites, such as operating system or security software vendors.
Intentionally modified hosts file
Under certain circumstances, hosts files may be manually modified by system administrators or developers in the course of their work.
Such intentional modifications will still trigger the 'redirected hosts file' detection. In such cases, to preserve the modification, the user should exclude the hosts file from scanning once the product detects the change (see section Removal: Exclude an intentionally modified hosts file).