Monitoring-Tool:W32/PCDM.A
Summary
A program that monitors and records all actions on a computer, including keystrokes entered.
Removal
Based on the settings of your F-Secure security product, it may block the file from running, move it to the quarantine where it cannot spread or cause harm, or ask you to select an action.
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
Monitoring-Tool:W32/PCDM.A is a riskware application designed to perform monitoring activities in a computer. The program must be manually installed on the computer system.
According to the application's product page, the program has the following features/functionalities:
System Monitoring
- Records clipboard entries and other copy-paste operations.
- Captures Windows screenshots at regular time interval (with slideshow viewing).
- Records system logins.
- Records any changes made in system date and time.
- Records keystroke entries (passwords, URLs, texts, documents) etc.
Internet Monitoring
- Records online voice chat conversations.
- Records browsed web pages.
- Records composed and send emails.
- Records internet cookies, temp files and more.
Log Report and Emailing
- Automatically prepares log report of entire PC activities.
- Displays the log report in Text or HTML file formats.
- Sends log report to defined e-mail address or uploads it to a remote server using FTP server settings.
Privacy
- Password-protection feature restricts external users from changing software settings.
- Administrator can easily hide the software from Add/remove list, Program folders, Start menu, and so on
- Hot keys and Run command settings facilitates access to software running in stealth mode.
Here is a screenshot of its user interface:
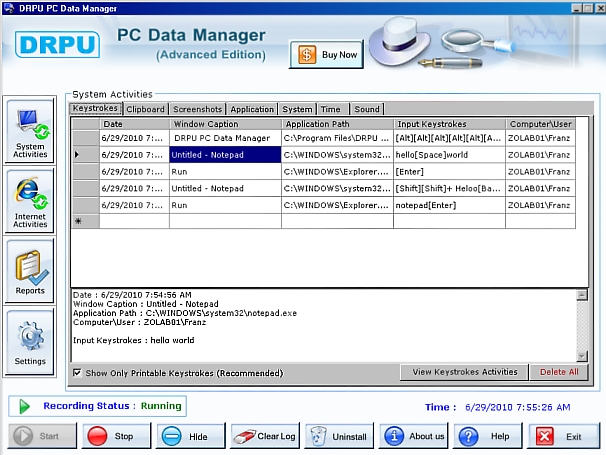
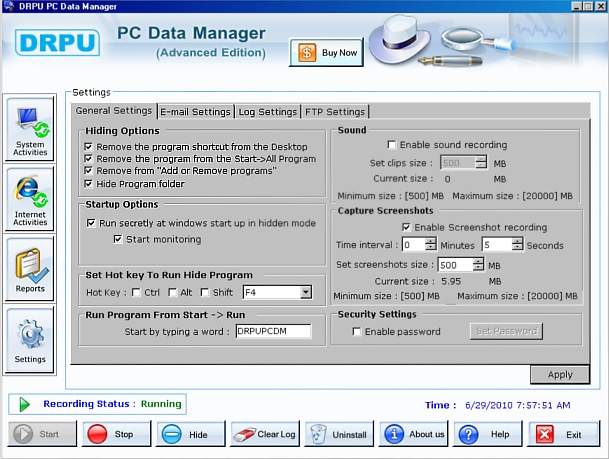
Installation
The default installation is to the following location:
- %Program Files%\DRPU PC\Data Manager
At this location are saved the program's main binary files and components:
- apcdm.exe - main binary file detected as Monitoring-Tool:W32/PCDM.A
- Help.chm
- Microsoft.Office.Interop.Excel.dll
- Pcdll.dll
- Settings.exe
- Settings.exe.manifest
- Shk.exe
- Shk.exe.manifest
- Uninstall.exe
- Uninstall.ico
- Uninstall.txt
Collected Log files for each users are stored in the following folder:
- %Documents and Settings%\All Users\Documents\PC DM Files
Note:%Program Files% is the environment variable for the Program Files Directory, which is typically the C:\Program Files folder.
%Documents and Settings% is the environment variable for the Documents and Settings Directory, which is typically the C:\Documents and Settings folder.
Stealth
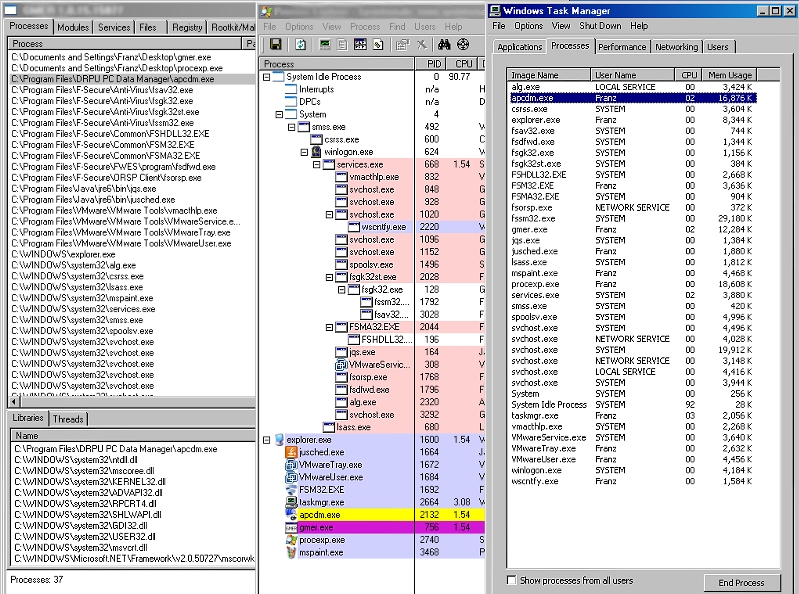
Though the program claims to be running in stealth mode, it does not implement any high level techniques to hide its process and folders, the former being easily identified using freely available tools, as seen in this screenshot of three different tools used to view the processes (click for larger view):
https://www.f-secure.com/v-pics/monitoring_tool_w32_pcdm_processes.jpg
Folders can be made visible by making certain changes to the Windows Folder Options settings, as can be seen in the image below (click for larger view):
https://www.f-secure.com/v-pics/monitoring_tool_w32_pcdm_folders.jpg
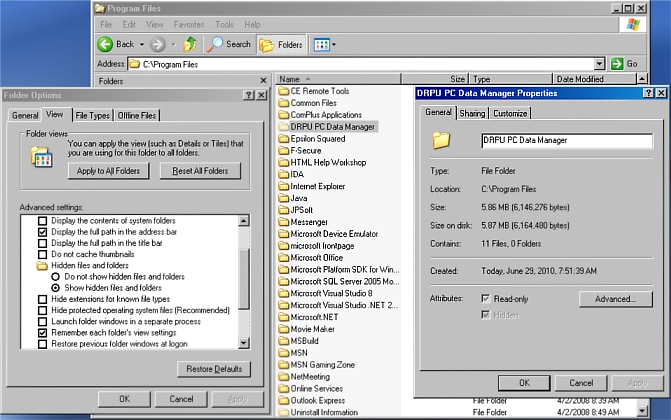
- Show hidden files and folders is selected.
- Hide Protected operating System files (recommended) is unchecked.
Registry Changes
The following are the registry entries created by the program:
- HKEY_LOCAL_MACHINE\Software\DRPUPCDM
- HKEY_CURRENT_USER\Software\DRPUPCDM
- HHEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run DRPU Pc Data manager = \apcdm.exe "hd"
Where "=" is the installation directory of the program and "hd" is its parameter indicating that the program be run as hidden.
)
Protect your devices from malware with F‑Secure Total
Protecting your devices from malicious software is essential for maintaining online security. F‑Secure Total makes this easy, helping you to secure your devices in a brilliantly simple way.
- Award-winning antivirus and malware protection
- Online browsing, banking, and shopping protection
- 24/7 online identity and data breach monitoring
- Unlimited VPN service to safeguard your privacy
- Password manager with private data protection
More Support
Community
Ask questions in our Community .
User Guides
Check the user guide for instructions.
Submit a Sample
Submit a file or URL for analysis.