|

Last year we hosted an F-Secure Reverse Engineering Challenge Compo. We've prepared a challenge for this year as well. The competition's target is to decode programs in order to find hidden information. It consists of three Windows executable files.
The author of Khallenge 2007 is the Response Lab's youngest member — Kamil. His main focus is on antispyware response.

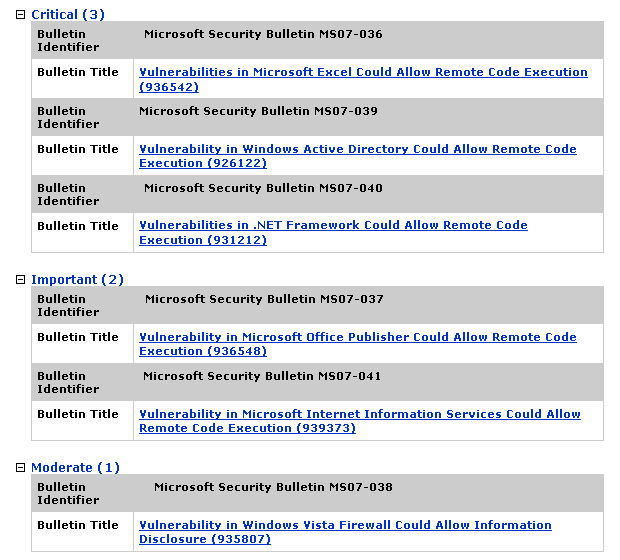
These updates cover vulnerabilities for several applications, including Office Excel, Windows Active Directory, and .NET Framework for the critical updates. Most of these vulnerabilities allow remote code execution and one allows information disclosure.
For more information as well as links for the actual patches, see July's bulletin.

Pretty much all of the messages we've seen have used a visible IP address as the address to download the greeting cards from. The fact that it's using an IP address and not a domain name is a pretty good sign that you shouldn't click on the link.
As today is the 4th of July – Independence Day in the United States, it wasn't a big surprise that there has been lots of malicious 4th of July greeting cards going around. They work exactly the same way as the other greeting cards and the ones we've seen have all been using IP addresses for the clickable link. Again, stay away from them.

What's great is that the security community is actively trying to get these sites shut down but the bad guys just keep on changing the IP address in the new mails. In addition, they keep changing the files that are being downloaded. It goes without saying that we're adding detection for them as we see new samples.
|
|