Email-Worm:W32/Vote
Summary
This type of worm is embedded in an email attachment, and spreads using the infected computer's emailing networks.
Removal
Manual removal for Vote variants
If the worm has been activated once the system must not be restarted before it is properly cleaned; otherwise, the payload will be triggered.To clean the system, the following actions should be taken:
- All the dropped files and added registry keys must be removed.
- If Vote.A is present, the affected applications (i.e., the ones Vote.A attempts to remove) must be reinstalled.
- All the destroyed HTML and HTM file must be restored from backup files.
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
Email-Worm:W32/Vote is a family of email worms that use the September 11 terrorist attacks as a ploy to get people to execute it. The worms are written in Visual Basic.On execution, Vote will attempt to download a trojan onto the machine in addition to propagating itself. The worm also includes a number of dangerous routines.The details below describe the Vote.A variant. For more details of the other variants, please see:
Vote.A was first reported on the 24th of September, 2001 - 13 days after the WTC tragedy. It appears to be written by a teenager.
Propagation
The worm uses standard Windows Mail API to access the user's address book. This affects users of MAPI compatible email clients, mainly Microsoft Outlook. The emails sent by the worm look like this:
From: name-of-the-infected-user To: random-name-from-address-book Subject: Fwd:Peace BeTween AmeriCa and IsLaM ! Hi iS iT waR Against AmeriCa Or IsLaM !? Let's Vote To Live in Peace! Attachment: WTC.exe
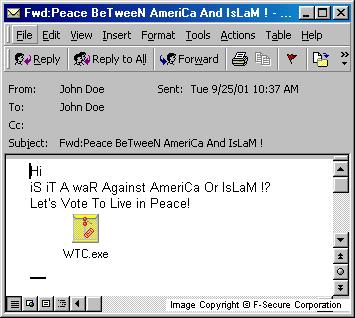
Installation
If the email file attachment is run, the worm is executed and drops the following files on the system:
- [windows_dir]\WTC.exe' - worm binary
- [windows_dir]\MixDaLaL.vbs' - HTML destroyer script
- [system_dir]\ZaCker.vbs' - payload (disk eraser)
The main worm executable (WTC.exe) then deletes a variety of files from the system in order to try and disable several antivirus programs.
Activity
The other two files dropped by the worm are scripts. '[windows_dir]\MixDaLaL.vbs' is a Visual Basic Script that searches through all the available fixed and network drives for .HTM and .HTML files. The content of all these files is replaced with this text:
- 'AmeRiCa ...Few Days WiLL Show You What We Can Do !!! It's Our Turn > > > ZaCkEr is So Sorry For You .'
ZaCker.vbs first deletes all files from the Windows folder. It then displays a message:
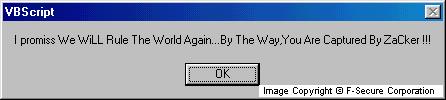
After displaying the message, the script modifies the autoexec.bat file in order to format the C: drive after the next reboot. This part of the script is broken, resulting in the autoexec.bat being empty. The script's attempt to reboot the system fails as the program called for reboot is deleted. While active, the worm opens two windows in the Microsoft Internet Explorer web browser. The first is a faked voting booth. The second page is set to download a trojan called Barrio 5.0. The browser's start page is also set to this second page.If successfully downloaded, the Barrio trojan collects passwords (dialup, ICQ, UIN, etc) and fowards them to a pre-defined email address.
Registry
The 'ZaCker.vbs script adds the following registry key to ensure it is started on the next system reboot:
- [HKLM]\Software\Microsoft\Windows\CurrentVersion\run\Norton.Thar'
Activity
Once installed, the worm changes the startup page of Internet Explorer to point to the worm's file at "c:\Windows\WTC32.scr". After performing its mass-mailing routine, the worm displays one or more message boxes with different messages, for example:
- WORLD TRADE CENTER
- WE WILL ALWAYS REMEMBER THOSE LOST SOULS...
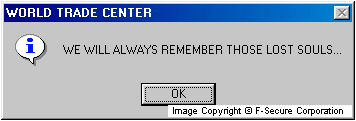
Some of these messages are very insulting and contain bad language.The worm's payload also includes dangerous routines. These are:
- Deleting all DLL files in C:\Windows\System32\ folder.
- Locating files with the following extensions - wav .mp3 .jpg .bmp .zip .rar .doc - and writing itself with the name of those files and an additional .exe extension. The original files are deleted.
- Overwriting all .exe and .scr files with its body.
File System Changes
Removes these files:
- C:\Program Files\AntiViral Toolkit Pro\*.*'
- C:\eSafe\Protect\*.*'
- C:\Program Files\Command Software\F-PROT95\*.*'
- C:\PC-Cillin 95\*.*'
- C:\PC-Cillin 97\*.*'
- C:\Program Files\Quick Heal\*.*'
- C:\Program Files\FWIN32\*.*'
- C:\Program Files\FindVirus\*.*'
- C:\Toolkit\FindVirus\*.*'
- C:\f-macro\*.*'
- C:\Program Files\McAfee\VirusScan95\*.*'
- C:\Program Files\Norton AntiVirus\*.*'
- C:\TBAVW95\*.*'
- C:\VS95\*.*'