Vierika
Summary
VBS/Vierika is a mass mailer (worm) written in Visual Basic Script.
This worm consists of two different script parts, one that arrives in an Outlook message as an attachment and another that is available on a web site.
Removal
Based on the settings of your F-Secure security product, it will either move the file to the quarantine where it cannot spread or cause harm, or remove it.
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
Variant:Vierika.A
On March 5th, 2001, F-Secure received several report about this worm. Due to efforts made by F-Secure Corporation and its Italian partner Symbolic S.p.A, the web page that contains the main part of the worm has been disabled in a few hours. On that way spreading of the worm has been stopped.
This worm arrives in a message that has the following content:
Subject: Vierika is here Body: Vierika.jpg Attachment: Vierika.jpg.vbs
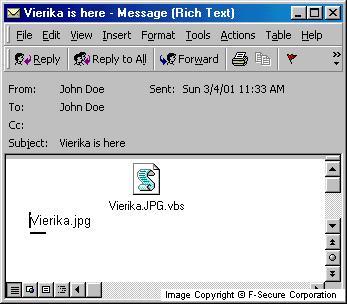
The attachment contains a small script, that lowers Internet Explorer security zone settings and also changes the start page to an Italian site. This page contains a script code, which is the main part of the worm.
Next time when Internet Explorer is started, the browser will connect to the infected page. Since security zone settings are lowered by the first part of the worm ("Vierika.JPG.vbs"), the second part ("Vindex.html") is able to execute directly from the web site.
This part will first drop a file "c:\Vierika.JPG.vbs" that is the first part of the worm, and spread it using Microsoft Outlook to to each recipient in every address book.
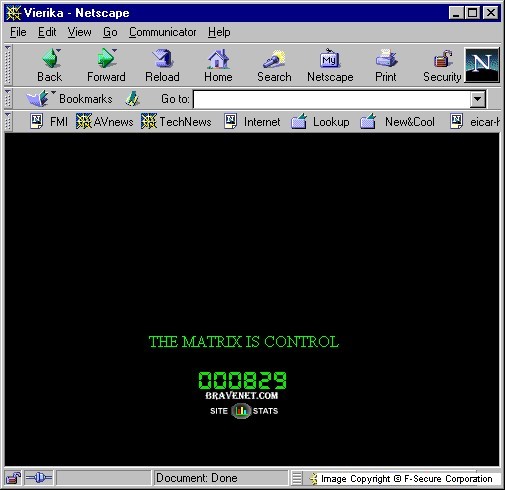
The page that contains the second (mass mailing) part of the worm looks as follows:
THE MATRIX IS CONTROL
To restore the Internet Explorer start page setting, change or remove the following registry key:
HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main\Start Page
Also the Internet security zone setting should be restored from "Tools/Internet Options/Security" dialog at least to "Medium" level.
Variant:Vierika.B
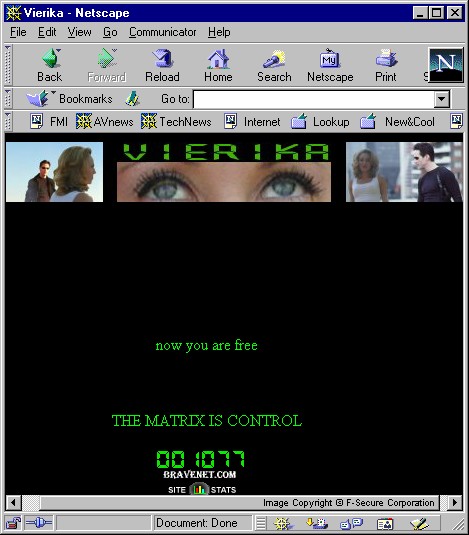
This variant arrives in a message that have the same content with VBS/Vierika.A@mm. However, the worm is modified slightly and it uses a web page located at Geocities server. The web page is modified as well:
now you are free MATRIX IS CONTROL
After mass mailing, VBS/Vierika.B replaces "C:\Vierika.JPG.vbs" with a file that contains only the following word:
free
F-Secure Anti-Virus has a heuristic that detects this worm. This detection is included in updates released before March 5th, 2001.