Valentine
Summary
VBS/Valentine is a mass mailing worm written in Visual Basic Script.
On February 19th 2001, this worm has been posted to several Usenet newsgroups. F-Secure Anti-Virus detects this worm with updates released February 13rd, 2001 or later.
Removal
Based on the settings of your F-Secure security product, it will either move the file to the quarantine where it cannot spread or cause harm, or remove it.
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
Variant:Valentine.A@mm
The worm arrives in an infected message sent with Microsoft Outlook. When it is openend, it first drops "loveday14-b.hta" to the Windows Startup directory in both Spanish and English versions of Windows.
When the system is restarted, "loveday14-b.hta" will be executed and the following message box is shown.
The worm creates an infected "main.html" file to the Windows System directory and sets the Internet Explorer start page to point to a web page that contains another worm, VBS/San.A@m. Further information about VBS/San.A@m is available at: https://www.Europe.F-Secure.com/v-descs/san.shtml
VBS/Valentine.A sends itself to every recipient in each address book. The infected message has the following content:
Subject: Body: Que cosa mas tonta
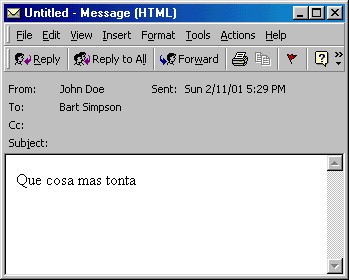
Message does not have an attachment. The worm code is embedded into the HTML message itself on a similar way as VBS/BubbleBoy.
Like VBS/Timofon.A, this worm attempts to send messages to cellular phones using a SMS gateway at Movistar.net. These messages contain the following text:
Feliz san valentin.
These messages are visible in Outlook Sent Items folder. They look as follows:
Subject: Feliz san valentin Body: Feliz san valentin. Por favor visita (link to a web page)
where (link to a web page) is a link to the worm itself.
Next VBS/Valentine.A searcs all network and local drives for a mIRC installation, and if such is found, it replaces the "script.ini" file with its own causing that the "mail.html" from the Windows System directory will be sent when an user joins the same channel where an infected user is.
At 8th, 14th, 23rd and 29th of any month the worm activates its payload deleting all files from all drives, replacing deleted files with text files that has the same name but an additional ".txt" extension. These text files have the following content:
Hola, me llamo Onel2 y voy a utilizar tus archivos para declararle mi amor a Davinia, la chica mas guapa del mundo. Feliz san Valentin Davinia. Eres la mas bonita y la mas simpatica. Todos los dias a todas horas pienso en ti y cada segundo que no te veo es un infierno. Quieres salir conmigo? En cuanto a ti usuario, debo decirte @ue tus ficheros no han sido contaminados por un virus, sino sacralizados por el amor que siento por Davinia.
This worm has been available on a public web page in the Internet and it has been posted to several Usenet newsgroups. Even after the infected web page has been removed from the Internet, the worm is able to spread via Outlook Express.
This worm uses the same security vulnerability as JS/Kak.A@m. A fix and futher information about this vulnerability is available from Microsoft: https://www.microsoft.com/technet/security/bulletin/ms99-032.asp
Further information about JS/Kak.A@m is available at: https://www.F-Secure.com/v-descs/kak.shtml