Email-Worm:W32/Sober.K
Summary
Sober.K worm was seeded in emails on 21st of February 2005. It is quite similar to the previous variants. Sober.K sends itself as an attachment in email messages with English or German texts.
Removal
Based on the settings of your F-Secure security product, it will either move the file to the quarantine where it cannot spread or cause harm, or remove it.
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
The worm is written in Visual Basic. The worm's file is a UPX packed PE executable about 52 kilobytes long. The unpacked worm's file size is over 179 kilobytes. The worm adds random garbage to the end of its file every time it installs itself on a computer.
Installation to system
When the worm's file is started it opens Write text editor with the following text as a decoy:
When the worm's file is run, it copies itself with 3 different names to %WinDir%\msagent\win32\ folder:
csrss.exe smss.exe winlogon.exe
These files are identical to the worm's copy except for byte at offset 0xA0. This byte is different in every dropped copy. The worm always keeps 2 of its processes in memory.
Sober.K worm adds startup keys for one of these files in System Registry:
[HKCU\Software\Microsoft\Windows\CurrentVersion\Run] "_winsystem.sys" = "%WinDir%\msagent\win32\smss.exe" [HKLM\Software\Microsoft\Windows\CurrentVersion\Run] "winsystem.sys" = "%WinDir%\msagent\win32\smss.exe"
If these keys are deleted, the worm re-creates them after a few seconds.
Also the worm drops a few empty files to Windows System and to the main installation folder. These files are used to deactivate previous variants of the worm:
runnowso.ber nonrunso.ber stopruns.zhz
The worm creates a few data files in the main installation folder:
datamx1.dat datamx2.dat datamx3.dat goto1.dat goto2.dat goto3.dat zippedso1.ber zippedso2.ber zippedso3.ber
The 'datamx' and 'goto' files are used to store email addresses collected from an infected computer's hard drive. The other 3 files are used to store the ZIPped worm's copy (it will be used for spreading).
Also the worm drops the 'read.me' file to Windows folder. This file contains the following text:
Ist eine weitere Test-Version. Lauft nur ein paar Tage! In diesem Sinne: Odin alias Anon
Spreading in emails
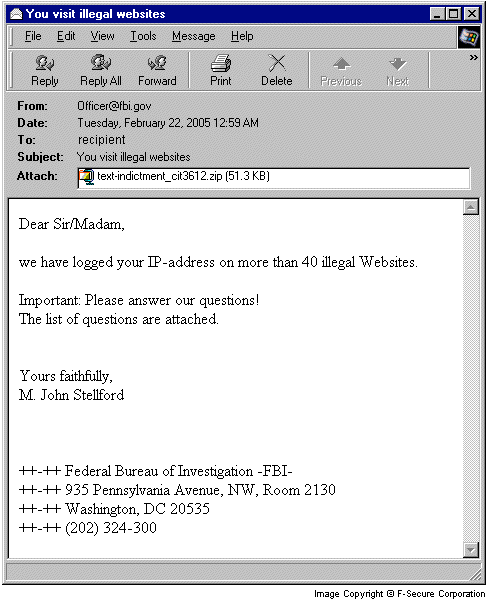
The worm sends different types of email messages with English and German texts and its file attached. The attachment is a ZIP archive containing the worm's executable. Here's a screenshot of an infected message sent by the worm:
Before spreading the worm scans files with certain extensions on all hard disks to harvest email addresses. Files with the following extensions are scanned:
pmr phtm stm slk inbox imb csv bak imh xhtml imm imh cms nws vcf ctl dhtm cgi pp ppt msg jsp oft vbs uin ldb abc pst cfg mdw mbx mdx mda adp nab fdb vap dsp ade sln dsw mde frm bas adr cls ini ldif log mdb xml wsh tbb abx abd adb pl rtf mmf doc ods nch xls nsf txt wab eml hlp mht nfo php asp shtml dbx
The found email addresses are saved into 6 files that the worm creates in its main installation folder:
datamx1.dat datamx2.dat datamx3.dat goto1.dat goto2.dat goto3.dat
When the worm is active in memory it blocks access to these files as well as to its MIME-encoded files and all 3 executable files.
The worm ignores email addresses that contain any of the following substrings:
ntp- ntp@ ntp. info@ test@ @www @from. support smtp- @smtp. gold-certs ftp. .dial. .ppp. anyone subscribe announce @gmetref sql. someone nothing you@ user@ reciver@ somebody secure whatever@ whoever@ anywhere yourname mustermann@ .kundenserver. mailer-daemon variabel noreply -dav law2 .sul.t- .qmail@ t-ipconnect t-dialin ipt.aol time freeav @ca. abuse winrar domain. host. viren bitdefender spybot detection ewido. emsisoft linux google @foo. winzip @example. bellcore. @arin mozilla iana@ iana- @iana @avp icrosoft. @sophos @panda @kaspers free-av antivir virus verizon. @ikarus. @nai. @messagelab nlpmail01. clock
The worm composes emails with both English and German texts. If the worm sends infected messages to domains with suffixes '.de', '.ch', '.at' and also to 'gmx.' domain, it composes messages in German, otherwise English messages are composed.
The worm composes the following English messages:
Subjects:
Your new Password Mail_delivery_failed Paris Hilton, pure! Alert! New Sober Worm! You visit illegal websites
Senders:
service webmaster register hostmaster postmaster police Officer Admin Web FBI Michele@yahoo.com Melanie@yahoo.com security@microsoft.com
Body texts:
Thanks for your registration! We have received your payment. For more detailed information, read the attached text.
---- or ----
This is an automatically generated Delivery Status Notification. ESMTP Error [] I'm afraid I wasn't able to deliver your message. This is a permanent error; I've given up. Sorry it didn't work out. The full mail-text and header is attached
---- or ----
More than 50 HOT Hilton Videos More than 3000 Hilton picks FREE Download until April, 2005 Make your own Download Account, it's free! Further details are attached Thanks & have fun ;)
---- or ----
ATTENTION! Antivirus vendors are warning of a new variant of the Sober virus discovered today that can delete the hard disk. Protection: Download and read the zipped patch. It's very easy to install! Thanks for your cooperation! --- (c)2005 Microsoft Corporation. All rights reserved --- Microsoft Corporation --- One Microsoft Way --- Redmond, Washington 98052-6399
---- or ----
Dear Sir/Madam, we have logged your IP-address on more than 40 illegal Websites. Important: Please answer our questions! The list of questions are attached. Yours faithfully, M. John Stellford ++-++ Federal Bureau of Investigation -FBI- ++-++ 935 Pennsylvania Avenue, NW, Room 2130 ++-++ Washington, DC 20535 ++-++ (202) 324-3000
Attachments:
text.zip register_.zip header_ .zip register.zip text_ .zip help-text.zip patch_ .zip indictment_cit.zip text- .zip
where <random> is a randomly generated number. The attachment name can be a combination of the above given file names as well.
The worm can add a fake anti-virus scanning report to its infected messages:
text.zip register_.zip header_.zip register.zip text_.zip help-text.zip patch_.zip indictment_cit.zip text-.zip
---- or ----
text.zip register_.zip header_.zip register.zip text_.zip help-text.zip patch_.zip indictment_cit.zip text-.zip
---- or ----
text.zip register_.zip header_.zip register.zip text_.zip help-text.zip patch_.zip indictment_cit.zip text-.zip
Followed by:
*-*Anti-Virus Service *-* http://www.
where <domain> is the domain name of a recipient.
The worm composes the following German messages:
Subjects:
text.zip register_.zip header_.zip register.zip text_.zip help-text.zip patch_.zip indictment_cit.zip text-.zip
Senders:
text.zip register_.zip header_.zip register.zip text_.zip help-text.zip patch_.zip indictment_cit.zip text-.zip
Body texts:
## Diese email wurde automatisch generiert ## Aus Gruenden der Sicherheit, bekommen Sie diese email ## wenn Ihr aktuelles Benutzer- Passwort veraendert wurde --------------- Ihr neues Passwort und weiter Informationen befinden sich im beigefuegten Dokument. **** Ein Service von **** http://www.**** Mail: Help-Line
---- or ----
text.zip register_.zip header_.zip register.zip text_.zip help-text.zip patch_.zip indictment_cit.zip text-.zip
---- or ----
text.zip register_.zip header_.zip register.zip text_.zip help-text.zip patch_.zip indictment_cit.zip text-.zip
---- or ----
text.zip register_.zip header_.zip register.zip text_.zip help-text.zip patch_.zip indictment_cit.zip text-.zip
---- or ----
text.zip register_.zip header_.zip register.zip text_.zip help-text.zip patch_.zip indictment_cit.zip text-.zip
---- or ----
text.zip register_.zip header_.zip register.zip text_.zip help-text.zip patch_.zip indictment_cit.zip text-.zip
Attachments:
PSW-Text.zip zipped-text.zip zipped-mail.zip Register-Info.zip Formular.zip Tool.zip Patch-.zip
where <random> is a randomly generated number.
The worm can add a fake anti-virus scanning report to its infected messages:
text.zip register_.zip header_.zip register.zip text_.zip help-text.zip patch_.zip indictment_cit.zip text-.zip
---- or ----
text.zip register_.zip header_.zip register.zip text_.zip help-text.zip patch_.zip indictment_cit.zip text-.zip
---- or ----
text.zip register_.zip header_.zip register.zip text_.zip help-text.zip patch_.zip indictment_cit.zip text-.zip
Followed by:
*-*Anti-Virus Service *-* http://www.
where <domain> is the domain name of a recipient.
The worm does not use any exploits to start its file automatically on a recipient's system.
Deactivation
The worm does not infect a computer if the file with the 'xcvfpokd.tqa' name is present on a hard drive.