Worm:Linux/Slapper
Summary
Slapper is a network worm that spreads on Linux machines by using a flaw discovered in August 2002 in OpenSSL libraries. The worm was found in Eastern Europe late on Friday September 13th 2002.
Removal
The worm is visible in the infected system as a process ".bugtraq". An infected system can be disinfected by terminating the worm's process, and by removing the files created into temporary directory:
- /tmp/.uubugtraq
- /tmp/.buqtraq.c
- /tmp/.bugtraq
The Apache web server must be shut down as well and the OpenSSL libary must be upgraded to a fixed version (0.9.6e or above) in order to avoid reinfection.
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
The worm works on Intel-based machines running Linux distributions from Red Hat, SuSE, Mandrake, Slackware or Debian. Apache and OpenSSL must be enabled and OpenSSL version must be 0.96d or older.Apache installations cover more than 60% of public web sites on the internet. It can be estimated that less than 10% of these installations have enabled SSL services. SSL is most often used for online commerce, banking and privacy applications.
Slapper is very similar to the Scalper Apache worm, which was found in June 2002. The basic theory of operation is similar to the first widespread web worm, Code Red. Code Red infected more than 350000 websites running Microsoft IIS in July 2001.
Infection
The worm infects the system by creating a unencoded copy of itself to /tmp/.uubugtraq. It decodes the file to /tmp/.bugtraq.c and uses gcc compiler to produce an executable copy of itself as /tmp/.bugtraq, which is then executed.
Activity
At this point, the worm starts to scan a predefined set of Class A networks for vulnerable machines by connecting to the httpd server (port 80). If the worm can connect, it will check the content of the "Server:" header from the response. If the header contains the string "Apache", the worm will attempt to connect to the SSL server (port 443), and attempt to infect the target by using the OpenSSL vulnerability. Further details about the vulnerability are available below.
The worm also contains a backdoor that listens to UDP port 2002, and can be controlled remotely. The backdoor contains the ability to upload and execute arbitrary programs in the infected host. It also contains the functionality to perform various denial of service attacks. This backdoor is very similar to the one within the Scalper worm.
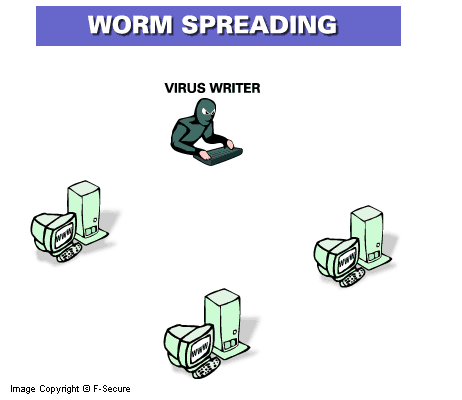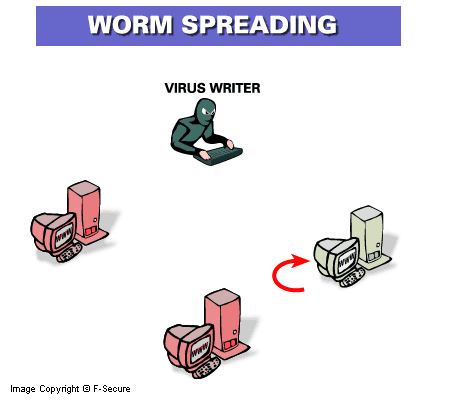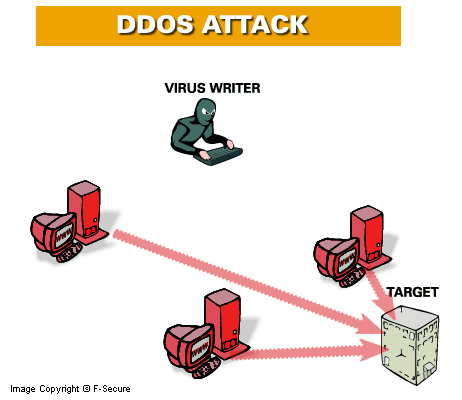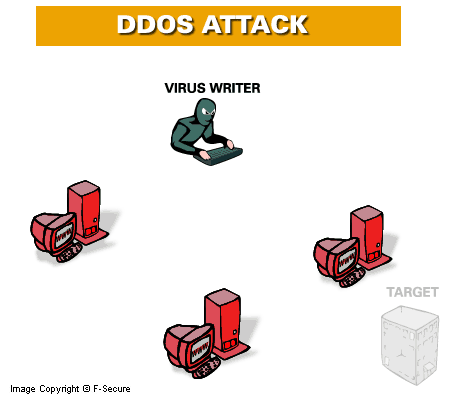
Once a machine gets infected, the worm starts to spread to new systems. In addition, the worm contains code to create a peer-to-peer attack network, where infected machines can remotely be instructed to launch a wide variety of Distributed Denial of Service (DDoS) attacks.
History
UPDATE (2002-10-02 15:30 GMT)A modification of the Cinik variant (Slapper.C) known as Slapper.C2 has been found. The only differences are some fixes of bugs introduced by the author in the original Slapper.C and it uses a different port, 1812.At the time this description was being written this worm was almost as active as the first version of Slapper which reached the peak of around 2000 active infected hosts simultaneously on its P2P network.
UPDATE (2002-09-30 16:00 GMT):Another new worm, using the same exploit against Apache and SSL was found on Monday the 30th of September 2002. This worm is currently known as Linux.Devnull. Some security vendors are calling it inux.Slapper.D, although the only thing it has common with Slapper is that it uses the same vulnerability.For more information, see http://www.f-secure.com/v-descs/devnull.htm
UPDATE (2002-09-23)A new variant of Slapper known as "Cinik" was found on Monday the 23rd of September 2002.This is slightly modified variant of Slapper.A. It uses port 1978 instead of port 2002 and the filename of the worm has been changed to "cinik.c". The worm also has backup functionality: if the worm is removed from the host, then it tries and download a copy of the worm from a page on a Românian web site (under home.ro).
We've been in touch with the administrators of this site and the virus page has now been deleted. This doesn't stop the worm from spreading though.Another variant "Unlock" was found on Sunday the 22nd of September 2002.
This variant uses port 4156 instead of port 2002 and the filename of the worm has been changed to "unlock.c". As both Cinik and Unlock versions use the same vulnerability as the original Slapper worm, most of the potential targets for them have been updated and patched already to prevent infection.
UPDATE (2002-09-16 09:50 GMT) so far, we've received direct reports of infected machines from almost 100 different countries.
UPDATE (2002-09-14 20:30 GMT) so far, F-Secure has received either direct or second-hand reports of infected machines from the following countries:
- Norway
- Lithuania
- România
- Portugal
- Japan
- The Netherlands
- China
- Turkey
- India
- USA
- Taiwan
- UK
More
The OpenSSL security advisory is available at:
- https://www.openssl.org/news/secadv_20020730.txt
CERT(r) advisory is available at:
- https://www.cert.org/advisories/CA-2002-23.html
Security advisories released by Linux vendors:
- Debian: http://www.debian.org/security/2002/dsa-136
Also:
- Mandrake: http://www.mandrakelinux.com/en/security/2002/MDKSA-2002-046.php
- RedHat: http://rhn.redhat.com/errata/RHSA-2002-155.html
- SuSE: http://www.suse.com/de/security/2002_027_openssl.html
Variants
Variant:Slapper.B
This is modified variant of Slapper.A.When the host is infected, this variant uploads itself to /tmp/.cinik.uu, decodes the source code to /tmp/.cinik.c and compiles itself to /tmp/.cinik.This variant also creates a bash script into temporary directory, /tmp/.cinik.go. The bash script is used to collect the system configuration information that is sent propably to the virus writer via email.
The script also copies the compiled .cinik file to every directory where the user used to run Apache server have write privilege.This variant uses port 1978 instead of port 2002.It also has a backup: if the worm source code is removed from the host, it will download a copy of its source code from a Românian web site, if the infected system has wget utility installed. F-Secure is working on removing of the worm from the web page.The worm also adds itself to the crontab file causing that the worm will be restarted hourly in case it has been terminated.
This variant can be removed from an infected host by removing the crontab entry from the user that is used to run the Apache web server, terminating the worm's process (.cinik) and removing the infected files from the host.
The Apache should also be shut down and appropriate updates should be applied before it is restated.F-Secure Anti-Virus detects this variant with the updates released at September 14th, 2002:
Variant:Slapper.C
This is a slightly modified variant of Slapper.A. This variant uses a different port - port 4156 instead of 2002 - and different file names. It uploads itself as /tmp/.unlock.uu, decodes the file to /tmp/.unlock and uses tar to decompress its content. Then the worm compiles the extracted source code /tmp/.unlock.c to /tmp/httpd, starts it and removes all files except /tmp/.unlock.This variant also sends IP addresses of infected hosts via email probably to the virus writer.
This variant can be removed from the host by shutting down Apache, killing the worm's process (httpd) and deleting the file /tmp/.unlock. The appropriate updates should be applied before the Apache is restarted.