Trojan:SymbOS/Skulls.D
Summary
Trojan:SymbOS/Skulls.D replaces system ROM binaries related to application uninstall and Bluetooth control.
Removal
Skulls.D can be disinfected by using F-Secure Mobile Security
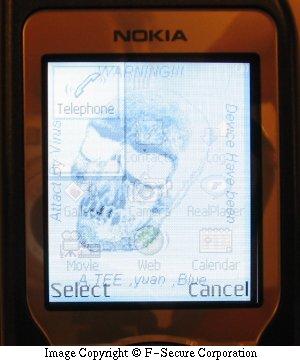
Kill the Skulls animation process, so that you can use the phone normally:
1. Press menu button on the phone for 5 seconds to get Symbian process menu
2. Look for any suspicious process, such as Caribe or Yewsprite
3. Select suspicious process and kill it with 'C' button
4. Repeat for all other processes
Then user Mobile Anti-Virus to scan the device:
1. Start F-Secure mobile Anti-Virus
2. Scan your device and remove infected files
3. Go to application manager
4. Uninstall the SIS file in which Skulls was installed (Flash_1[1].1_Full_DotSiS.sis)
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
Trojan:SymbOS/Skulls.D is a malicious SIS file trojan, that pretends to be Macromedia Flash player for Symbian Series 60 devices.

Instead, the trojan replaces system ROM binaries related to application uninstall and Bluetooth control. It also drops Cabir.M and other applications, disables third party file managers and tries to disable F-Secure Mobile Anti-Virus.
Fortunately, the Cabir.M worm in Skulls.D's payload is already detected with generic detection as Cabir.Gen; this results in Skulls.D being detected and stopped without needing an updated Anti-Virus database. Note that for this to occur, F-Secure Mobile Anti-Virus must be in realtime scan mode, as it is by default.
If you have installed Skulls.D, the most important thing is not to reboot the phone and follow the disinfection instruction in this description.
Skulls.D has been found both as independent SIS file, and as an embedded SIS in which the host SIS file pretends to contain cracked game or application.
Payload
Unlike earlier Skulls versions the Skulls.D disables only few phone system applications. The only system applications that are disabled are the ones that are needed in disinfecting it.
Skulls.D also tries to disable third party applications the user would need to disinfect the phone of a Skulls infection. For some reason however, Skulls.D copies the replacement files to the device memory card, thus disabling the tools only if user has not installed them on the C: drive.
Skulls.D is designed to disable F-Secure Mobile Anti-Virus by replacing its files with non-functional versions. As the Anti-Virus detects the infected SIS file and prevents it from being installed, this does not occur.
The Cabir.M dropped by Skulls.C does not activate automatically, but will activate on reboot. The Skulls.D does also drops other applications that will activate on device reboot. This application displays animation of flashing Skull picture on background, no matter what application user is trying to use: