NewLove
Summary
VBS/NewLove is a destructive and polymorpic VBScript worm similar to VBS/LoveLetter. Further information about VBS/LoveLetter is available at https://www.F-Secure.com/v-descs/love.shtml
Removal
Based on the settings of your F-Secure security product, it will either move the file to the quarantine where it cannot spread or cause harm, or remove it.
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
Variant:NewLove.A
VBS/NewLove.A uses Microsoft Outlook to spread in email messages. The message that it sends looks like this:
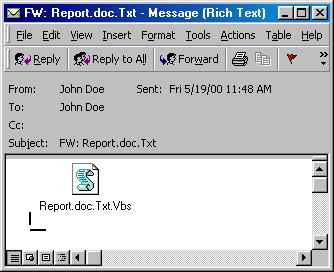
From: name-of-the-infected-user To: random-name-from-address-book Subject: FW: (random_file_name.ext) Body: Attachment: (random_file_name.ext).vbs
The worm replicates in an attachment with a random file name that has ".vbs" added to it. For example, "REPORT.DOC.vbs" or "Information on Jacks Birthday.txt.vbs". VBS/NewLove takes the random name from the recently opened files directory. If there is no files in that directory, it generates the name.
If the attachment is opened with the Notepad, the code of the worm can be seen:
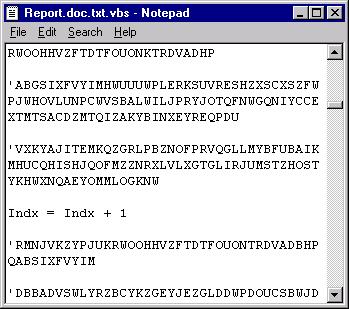
Then the worm sends itself to each recipient in each Outlook address book - just like VBS/LoveLetter.
VBS/NewLove.A copies itself - with a random name - to the Windows System directory and to the Windows directory. It adds itself to the registry with a random key to the following registry hives:
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run\ HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunServices\
Then the worm will go through all drives and subdirectories. For each file, the worm creates a new file using the same name with an additional extension ".vbs" and deletes the original file.
After this the machine can not boot any longer.
VBS/NewLove.A was reported to be somewhat in-the-wild on 19th of May, 2000. Detection of this worm was added to F-Secure Anti-Virus on 11:00 GMT 19th of May, 2000.