Worm:W32/NetSky.AA
Summary
NetSky.AA worm was found on April 27th, 2004. This variant is similar to previous Netsky variants, but it does not have a backdoor and a payload.
Removal
Based on the settings of your F-Secure security product, it will either move the file to the quarantine where it cannot spread or cause harm, or remove it.
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
The worm's file is a PE executable 17408 bytes long packed with a new or modified file compressor.
Installation to system
Upon execution NetSky.AA copies itself as WINLOGON.SCR file to Windows folder and adds a startup key for this file into System Registry:
[HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] "SkynetsRevenge" = "%WinDir%\winlogon.scr"
where %WinDir% represents Windows folder name.
Then the worm shows a fake error messagebox:
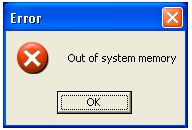
If the worm's file extension is SCR, then the messagebox is now shown.
Spreading in emails
The worm scans all hard drives from C: to Z: to harvest email addresses. The worm looks for email addresses in files with the following extensions:
.eml .txt .php .cfg .mbx .mdx .asp .wab .doc .vbs .rtf .uin .shtm .cgi .dhtm .adb .tbb .dbx .pl .htm .html .sht .oft .msg .ods .stm .xls .jsp .wsh .xml .mht .mmf .nch .ppt
Netsky.AA worm ignores email addresses that contain any of the following strings:
icrosoft antivi ymantec spam avp f-secur itdefender orman cafee aspersky f-pro orton fbi abuse messagelabs skynet andasoftwa freeav sophos antivir iruslis
The worm composes emails with different subject and body texts. Here is the list of subject texts that the worm uses:
Re: Document Re: Approved Re: Text Re: Thank you! Re: Details Re: Photos Re: Private Re: Information Re: Hi Re: Hello Re: Summary Re: Step by Step Re: Music Re: Application Re: Tel. Numbers Re: List Re: Text file Re: Paint file Re: Contacts Re: e-Books Re: Bill Re: Error Re: Missed Re: Letter Re: Product Re: Website Re: Movie Re: Presentation Re: Advice Re: Fax number Re: Cheaper Re: War Re: Demo Re: Final Re: Poster Re: Patch Re: Pricelist Re: Job
The worm uses one of the following text strings as body text for an infected message:
Your document is attached. Here is the file. Please view the attached file. See the attached file for details. Please take the attached file. Please have a look at the attached file. Please read the attached file. Your file is attached. For furher details see the attached file.
Netsky.AA attaches its executable file to emails that it sends out. The attachment name is selected from the following variants:
Your_Document.pif Your_Document.pif Your_Text.pif Your_Document_Part3.pif Your_Details.pif Your_Pics.pif Your_Private_Document.pif Your_Information.pif Your_Document.pif Your_Digicam_Pictures.pif Your_Summary.pif Your_Description.pif Your_Music.pif Your_Software.pif My_Telephone_Numbers.pif Your_List.pif Your_Text_File.pif Your_Paint_File.pif Your_Contacts.pif Your_E-Books.pif Your_Bill.pif Your_Error.pif Your_Excel_Document.pif Your_Letter.pif Your_Product.pif Your_Website.pif Your_Movie.pif Your_Presentation.pif My_Advice.pif My_Fax_Numbers.pif Your_Product_List.pif Osam_Bin_Laden_Articel_42.pif Your_Demo.pif Your_Final_Document.pif Your_Poster.pif Your_Patch.pif Your_Pricelist.pif Your_Job.pif