Worm:W32/Mydoom.M
Summary
This type of worm is embedded in an email attachment, and spreads using the infected computer's emailing networks.
Removal
Based on the settings of your F-Secure security product, it will either move the file to the quarantine where it cannot spread or cause harm, or remove it.
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
Mydoom.M is a mass-mailing worm that sends emails with messages that looks like mail system errors and automated spam warnings.
To collect more addresses, Mydoom.M also uses web search engines like Google and Yahoo.The worm carries a backdoor that listens on port 1034/TCP. This backdoor and the Zindos worm carried out a Distributed Denial-of-Service (DDOS) attack against www.microsoft.com.
Infection
Mydoom.M arrives in email as a packed executable. The worm is packed with the UPX packer and adds random trailing junk to itself to evade easy detection.
When the worm's file is run, it copies itself as java.exe to Windows System folder and creates a startup key for this file in the Registry:
- [HKLM\Software\Microsoft\Windows\CurrentVersion\Run] "JavaVM" = "%WindowsDir%\ java.exe"
The backdoor component is dropped to the Windows folder as services.exe and added to the registry:
- [HKLM\Software\Microsoft\Windows\CurrentVersion\Run] "services" = "%WindowsDir%\services.exe"
%WindowsDir% represents the Windows folder name, for example C:\Windows on Windows XP systems.
Propagation (Email)
Mydoom.M collects email addresses from Windows Address Book (WAB), Temporary Internet Files and by scanning the hard drive. To collect even more addresses Mydoom.M uses Google, Yahoo, Lycos and Altavista search engines. Utilizing these engines the worm performs a query for the domains of addresses it already found in other places (eg.Address Book).
The infected emails Mydoom.M sends most often look like mail system error and other warning messages.
Mydoom.M uses the following text strings as subjects for infected emails that it sends:
- Returned mail: Data format error
- Returned mail: see transcript for details
- Delivery reports about your email
- Mail System Error - Returned Mail
- Message could not be delivered
- delivery failed
- report
- test
- status
- error
- hi
- hello
The text body of emails are created from templates with randomly changing parts. For example:
Dear user yyy@XXX, Your account was used to send a large amount of junk email during the last week.Most likely your computer had been infected by a recent virus and now contains a hidden proxy server. Please follow instructions in order to keep your computer safe. Best wishes, XXX user support team.
Other messages may look like this:
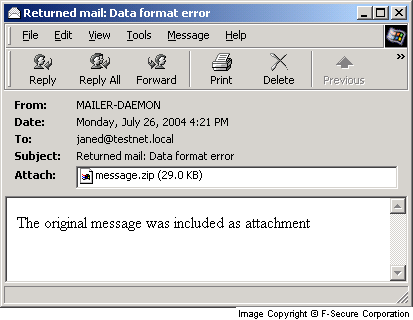
Attachments will get one of the following names with CMD, BAT, COM, EXE, PIF or SCR extension:
- message
- document
- attachment
- text
- file
- letter
- transcript
- instruction
- readme
In some cases, when the worm targets specific domains, it sends a ZIP attachment that contains an executable file with the following name structure:
- .{doc|txt|htm|html}.{com|exe|scr|pif}
The worm ignores email addresses that contains any of the following domains and accounts:
- avp
- syma
- sarc.
- microsoft
- msdn.
- msn.
- hotmail
- panda
- spersk
- yahoo
- sophos
- example
- domain
- uslis
- update
- trend
- foo.com
- bar.
- secur
- seclist
- gmail
- gnu.
- arin.
- ripe.
- sourceforge
- sf.net
- rarsoft
- winzip
- winrar
- root
- info
- noone
- nobody
- nothing
- anyone
- someone
- your
- you
- me
- rating
- site
- soft
- no
- foo
- help
- not
- feste
- ca
- gold-certs
- the.bat
- page
- root
- info
- noone
- nobody
- nothing
- anyone
- someone
- your
- you
- me
- rating
- site
- soft
- no
- foo
- help
- not
- feste
- ca
- gold-certs
- the.bat
- page
Backdoor
As confirmed with the discovery of the Zindos worm, the backdoor component is used a first stage of the Mydoom.M + Zindos attack.
Mydoom.M drops a backdoor component that listens on port 1034/TCP. Connecting to the port, the attacker can upload and execute arbitrary files and get the list of infected computers.
The backdoor scans random IP addresses for open 1034/TCP and collects them to a list for retrieval later.