Linong
Summary
Linong is an email worm that consints of binary and script parts.
Removal
Based on the settings of your F-Secure security product, it will either move the file to the quarantine where it cannot spread or cause harm, or remove it.
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
Binary part
The binay part if the worm is about 360 kilobytes in size. It contains a VBS script that is dropped to the system during the infection.
When the exe file is run it copies itself to different places:
- '%WinDir%\PCpower.exe'
- '%SystemDir%\MyLiong.exe'
To ensure that it will be started at every system startup several registry keys are also added:
- 'SOFTWARE\Microsoft\Windows\CurrentVersion\Run\MyLinong' (MyLinong.exe) 'SOFTWARE\Microsoft\Windows\CurrentVersion\Run\PCPower' (PCPower.exe)
- 'SOFTWARE\Microsoft\Windows\CurrentVersion\Run\Linong' (MyLinong.vbs)
After setting the registry keys the VBS script is dropped to a file named 'MyLinong.vbs' in Windows sytem directory.
Using the standard Windows messaging API (MAPI) it collects email addresses from the incoming emails and sends itself to those (in one run up to 50 messages).
The email sending routine generates messages randomly from the following components:
Subjects:
- 'Info From CFusion'
- 'Patch Your CFusion'
- 'Still Remember You'
- 'Light Up The Night'
- 'Man Choice'
- 'Kiss Me'
- 'S**y Model'
- 'Popeye Cartoon'
- 'Olive & Popeye'
- 'MyGirlFriend Dogs'
- 'My Girl Friend Dogs'
- 'Sweet Lovely'
- 'Password'
- 'Need Help '
- 'Bill'
- 'Mikropos'
Message bodies:
- 'You can update your Cfusion Online For Free'
- 'Are You Ready Fix Your Cfusion,Please Update'
- 'She is MY s**y Linong'
- 'Light up The Night PARTY...'
- 'Are You Man or women. This is The sponsor from our site The man choice'
- '100 way to kiss your GirlFriend or your boyfriend'
- 'Did you ever see the s**y girls like her'
- 'The New Popeye New Cartoon NetWork'
- 'Olive And Popeye Cartoon'
- 'Nice dog...'
- 'Good Dog and Smart dogs'
- 'My Icq Friend Sweet and Lovely'
- 'Here The list of Nude Password Website. All of them Still Active, and few of them are death password'
- 'Do you need help ? to get money over the internet. You can read the help' 'Bill..'
- 'The New Mikropos Software From Mikropos Network'
The attached files can get these names:
- 'CFusion.Exe'
- 'PatchFusion.exe'
- 'MyLinong.Exe'
- 'Light up the night.exe'
- 'StarMild.exe'
- 'Kiss.Exe'
- 'S**y.Exe'
- 'Popeye.exe'
- 'Olive.exe'
- 'BullBull.exe'
- 'Moly.exe'
- 'Lovely.exe'
- '868879.exe'
- 'Help.exe'
- 'BillGate'
- 'Mikropos'
It has a visible payload also. On certain dates messages are displayed:
25th of June:
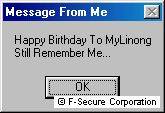
22nd of July:
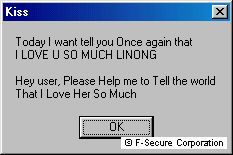
14th of November:
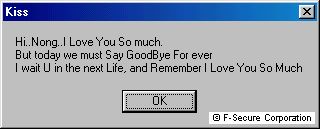
The other payload is rather annoying, it creates 500 directories to the 'C:\Linong I Love U So Much Linong For ever My Love[0-499]'
Script part
The scrip part of the worm is written in Visual Basic Script and is both, network and fast email (mass mailing) worm.
The mass mailer spreads using Outlook Application to all recipients listed in each address book. The email looks as follow:
Subject: One of this mail Body: True Story.... Attachment: mylinong.exe
where the attachment mylinong.exe is taken from the Windows System directory.
Once executed the script will copy itself as:
-
In Windows folder
- mylinong.jpg.shs
- Vbrun32DLL.vbs
-
In Windows System folder
- Kern32Lin.vbs
- mylinong.jpg.vbs
and will modify the registry to run the script on startup:
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run\Kern32lLin<Windows System>Kern32Lin.vbs
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunServices\Vbrun32DLL<Windows>vbrun32DLL.vbs
It will also change the Internet Explorer start page to the following location:
www.thewebpost.com/lovepoems/1198/dpt112098ily.shtml
Then Linong.A creates 600 directories on the infected machine.
After the worm has been active on an infected system for 14 days it will delete the above created directories and the dropped copies of itself from Windows and Windows System folders.
During the time Linong is active it attempt to show an html file previously dropped as mylinong.hta. This file shows the following text:
I L o v e Y o u L i n o n g You are the love of my love Almost One Year.., Miss U 01*29**879 01*29**868
The network part of the worm generates random IP addresses and connects to them. When the C drive of these machines is shared and there is write access to it Linong will copy itself as linong.vbs in root, Windows and startup directories but it will not copy the binary part of the worm. That is why, running the script from a remote mashine will not spread the worm.