Ganda
Summary
This email worm was found on 17th of March 2003. It uses it's own SMTP engine to send emails to addresses collected from Windows Address Book.
Removal
Based on the settings of your F-Secure security product, it will either move the file to the quarantine where it cannot spread or cause harm, or remove it.
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
The emails include a attachment which is a SCR (screen saver) file around 45kb in size (62kB mime-encoded). The filename is always short, such as RG.SCR or PW.SCR.
Some of the messages sent by the worm have a fake sender address, replacing the "From" field with addresses belonging to Swedish journalists or school officials. These people have nothing to do with the worm and they are not spreading it either - the worm just tries to make it look like that.
These fake addresses include skolverket@skolverket.se, red@fna.se, debatt@svt.se and several personal addresses from tidningen.to and aftonbladet.se (Swedish magazines). The worm will send massive amounts of rant emails to these addresses as well.
The messages sent by the worm are in Swedish or in English, depending on the language settings of the infected computer.
In addition to the email spreading, Ganda also parasitically appends a small piece of code to PE executable files. The purpose of this code is to patch the locations of API calls so the worm code will be executed.
The worm's file is a PE executable about 45 kilobytes long. It is not packed, however, some areas in the worm's body are encrypted with a simple crypto algorithm.
When the worm's file is activated it first decrypts its internal areas and then gets API addresses for several functions from KERNEL32.DLL, ADVAPI32.DLL, SHELL32.DLL, WININET.DLL, WSOCK32.DLL libraries. Then the worm creates a mutex named 'SWEDENSUX'. This mutex is used to identify the presence of another worm's copy in a system. The worm allocates a few blocks of memory for its internal use. After that the worm registers itself as a service process and remains resident in Windows memory.
The worm copies itself as SCANDISK.EXE into Windows directory and also it copies itself there with a randomly-generated name (for example AYDJSSKJ.EXE). Then the worm creates a startup key for the SCANDISK.EXE file:
[HKLM\Software\Microsoft\Windows\CurrentVersion\Run] "ScanDisk" = "%WinDir%\SCANDISK.EXE"
Then the worm attempts to kill processes of anti-virus and security software that have the following strings:
virus firewall f-secure symantec mcafee pc-cillin trend micro kaspersky sophos norton
After that the worm waits for Internet connection. When Internet connection is available, the worm starts to look for email addresses on an infected system. It looks for addresses inside files located in cache folders and elsewhere on a hard disk. The worm collects email addresses from Windows Address Book (it uses the WAB32.DLL library to access the Address Book) and from the following files:
*.eml *.*htm* *.dbx
The worm has its own SMTP engine. It connects to the SMTP server that is mentioned in the Registry or to 'm1.611.telia.com' SMTP server. The worm sends itself to all found email addresses. Sometimes the worm fakes the sender's email address. The fake address can be selected from the list of found addresses or from one of the following variants:
qruvabzabr@hotmail.com red@fna.se debatt@svt.se susanne.sjostedt@tidningen.to skolverket@skolverket.se mary.martensson@aftonbladet.se katarina.sternudd@aftonbladet.se cecilia.gustavsson@aftonbladet.se jessica.ritzen@aftonbladet.se margareta.cronquist@tidningen.to annika.sohlander@aftonbladet.se kerstin.danielson@aftonbladet.se insandare@tidningen.to insandare@aftonbladet.se
Additionally the worm sends a 12 kilobyte message in Swedish to the above listed email addresses using the 'skrattahaha@hotmail.com' as the sender's address. If the worm gets widespread, it will SPAM those addresses with thousands of messages overloading the mail servers.
The infected message's subject and body are randomly selected by the worm from its internal list. The messages sent by Ganda worm look like that:
or
These are examples of English subjects and bodies that the worm uses to compose messages:
Subject:
Screensaver advice.
Body:
Do you think this screensaver could be considered illegal? Would appreciate if you or any one of your friends could check it out and answer as soon as humanly possible. Thanx !
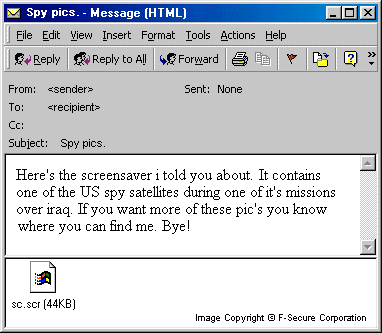
Subject:
Spy pics.
Body:
Here's the screensaver i told you about. It contains pictures taken by one of the US spy satellites during one of it's missions over iraq. If you want more of these pic's you know where you can find me. Bye!
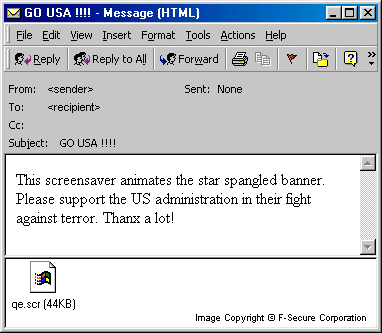
Subject:
GO USA !!!!
Body:
This screensaver animates the star spangled banner. Please support the US administration in their fight against terror. Thanx a lot!
Subject:
G.W Bush animation.
Body:
Here's the animation that the FBI wants to stop. Seems like the feds are trying to put an end to peoples right to say what they think of the US administration. Have fun!
Subject:
Is USA a UFO?
Body:
Have a look at this screensaver, and then tell me that George.W Bush is not an alien. ;-)
Subject:
Is USA always number one?
Body:
Some misguided people actually believe that an american life has a greater value than those of other nationalities. Just have a look at this pathetic screensaver and then you'll know what i'm talking about. All the best.
Subject:
LINUX.
Body:
Are you a windows user who is curious about the linux environment? This screensaver gives you a preview of the KDE and GNOME desktops. What's more, LINUX is a free system, meaning anyone can download it.
Subject:
Nazi propaganda?
Body:
This screensaver has been banned in Germany. It contains a number of animated symbols that can be related to the nazi culture. What do you think, is it a legitimate ban or not? Please answer asap. Thanx!
Subject:
Catlover.
Body:
If you like cats you'll love this screensaver. It's four animated kittens running around on the screen. Contact me for more clipart. Have fun! ;-)
Subject:
Disgusting propaganda
Body:
Hello! My 12 year old doughter received this screensaver on a CDROM that was sent to her through advertising. I find it disturbing that children are now being targets of nazi organizations. I would appreciate to hear from you on this matter, as soon as possible. Thank you.
The worm uses the following Swedish subjects:
Olaglig skarmslackar Rashets eller inte? Hakkors. Suspekta semaforer. Avskyvard reklam. Eâ€Å'verviktiga f¶rnedra ... Go ack ack ack.... Ežr USA ett UFO? Korkad president. Katt, hund, kanin. Myzli!
Some of the messages sent by the worm use the IFRAME exploit to automatically execute the infected attachment on recipients' systems. However only older and unpatched versions of certain email clients are affected.
The worm is attached to the infected message as 'xx.SCR' file where 'xx' are 2 random characters for example the attachment name can be 'SI.SCR'. To encode the attachment the worm creates a temporary file named 'tmpworm.exe' and encodes it into the infected message.
The worm includes the following text:
[WORM.SWEDENSUX] Coded by Uncle Roger in Harn¶sand, Sweden, I am being discriminated by the swedish schoolsystem. This is a response to eight long years of discrimination. I support animal-liberators worldwide.
Parasitic Appending to Executable Files
The worm affects .EXE (only PE EXE files) and .SCR files on an infected computer's hard disk. The worm appends a small code to .EXE and .SCR files that starts the worm's file (the one with a random name) every time an affected file is run. The worm also reads the contents of .LNK (link) files and tries to patch .EXE and .SCR files that those link files point to.
When affecting EXE and SCR files, the worm looks for certain API calls to KERNEL32.DLL library and replaces them with a jump to its appended code. One of the following API call instructions are patched:
LoadLibraryA GetModuleHandleA GetProcAddress ExitProcess
So when an affected file is started and execution reaches the patched address, the control is passed to the parasitically appended small piece of code, that in its turn starts the randomly-named worm's file in Windows folder.