Maldal
Summary
This is a political worm, found on the 19th of December, 2001.
Maldal worms spreads as an email attachment named CHRISTMAS.EXE, which looks like a typical multimedia Christmas Greeting Card.
Removal
Based on the settings of your F-Secure security product, it will either move the file to the quarantine where it cannot spread or cause harm, or remove it.
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
Maldal is written in Visual Basic for Applictions. It collects email addresses from Outlook database and from MSN Messenger contact list. It sends messages with constant message text and attachment name.
Messages sent by Maldal look like this:
Name: name-of-the-infected-user To: random-name-from-address-book Subject: Happy New Year Hii , I can't describe my feelings But all I can say is Happy new year :-) bye Attachment: christmas.exe
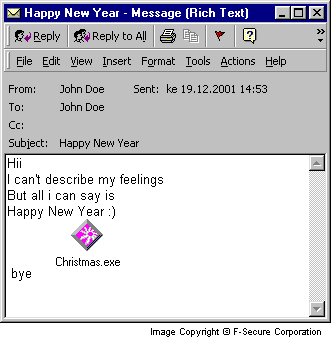
When the attachment is opened it displays a Christmas greeting window to disguise the malicious activity.

The worm copies itself to the Windows directory as 'Christmas.exe'. This copy of the worm is added to the registry run keys as
'[HKLM]\Software\Microsoft\Window\CurrentVersion\Run\Zacker'
so it will be started whenever Windows starts up.
Payload:
After activation the worm disables the keyboard and attempts to delete everything from the Windows System directory.
The computer name is set to 'ZaCker' and modifies the Internet Explorer start page to an infected homepage.
Sharoon = a war crimenal Bush supports him So... Bush = a war crimenalAmerican people must protect their country otherwise, their government will lead them to the hell ! Best Regards America Lovers ZA-UNION
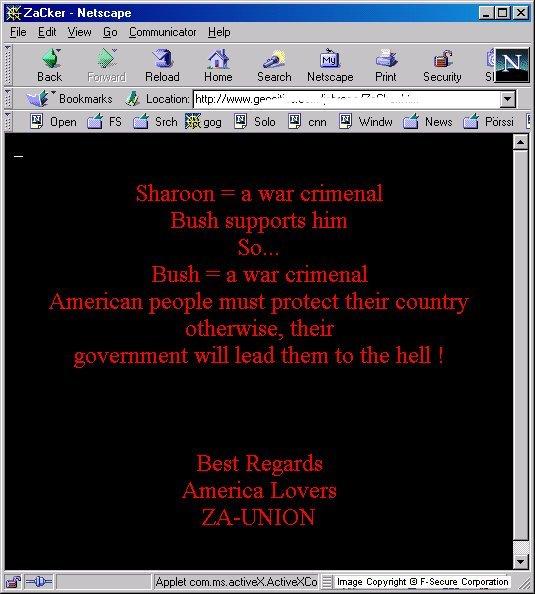
When the infected page is browsed using Internet Explorer, the JavaScript code in the page will execute, using a vulnerability known as Microsoft VM ActiveX control vulnerability (MS00-075). The JavaScript code will create an file "rol.vbs" in the root of the Windows installation drive and execute it.
At this point, the worm will attempt to remove contens of the following directories on the same drive:
Program Files\Zone Labs Program Files\AntiViral Toolkit Pro Program Files\Command Software\F-PROT95 eSafe\Protect PC-Cillin 95 PC-Cillin 97 Program Files\Quick Heal Program Files\FWIN32 Program Files\FindVirus Toolkit\FindVirus f-macro Program Files\McAfeeVirusScan95 Program Files\Norton AntiVirus TBAVW95 VS95 rescue
The worm will also drop file "DaLaL.htm" into Windows System directory, which contains a link to the second part of the worm. This file is copied, along with the copy of the worm as "server.vbs" to root of each mapped network drive.
Next the worm goes trough all all fixed and network drives, and appends the content of "DaLaL.htm" to each file with ".htm", ".html" or ".asp" extension.
The worm will also delete files with the following extensions: ".lnk", ".zip", ".jpg", ".jpeg", ".mpg", ".mpeg", ".doc", ".xls", ".mdb", ".txt", ".ppt", ".pps", ".ram", ".rm", ".mp3" and ".swf". After deleting a file, it will create a copy of itself with the same name and extension as the original file but adds ".vbs" extension into the name.
Maldal also searchs for mIRC application's configuration file, "mirc.ini", and replaces it. After that an infected user will show a message when another user joins the IRC channel where the user is. This message contains also a link to the infected web page.
Finally, if the script is executed after 30 minutes of the initial infection, and the number of seconds equals five, it attempts to delete all files from the system, shows a message box and shuts down Windows.
The second part of the worm behaves in the same way as the first part, except it drops another file to the Windows system directory - "outlook.vbs" - and executes it. This file then sends a message with a link to itself to all recipients listed in the Outlook Contacts folder.
The message has the following content:
Subject Very important !!! Body: See this page http://geocities.com/Xxxxxxx/xxx.htm
Variant:Various
There is a wide variety of closely related Maldal-variants, named with variable variant letters, depending on the anti-virus vendor. Latest (at the time of this writing) is known as Maldal.D, Maldal.E, Maldal.F, Maldal.G or Maldal.H, depending on the vendor. This variant (known to us as Maldal.D) and all variants up to it are detected by F-Secure Anti-Virus with the update released on January 3rd, 2002.