Bubbleboy
Summary
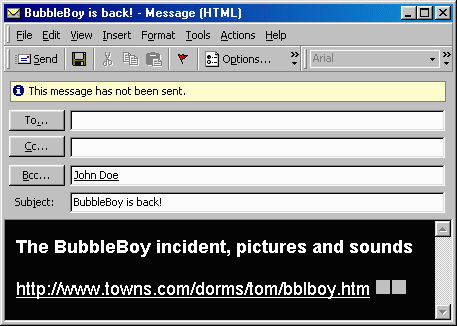
VBS/Bubbleboy is the very first worm that is able to spread via email without opening an attachment. It executes immediately after the user has opened the message in Outlook. Even viewing the message in Outlook Express "Preview Panel" causes the execution.The message looks like this:
From: (name of infected user) Subject: BubbleBoy is back! Body: The BubbleBoy incident, pictures and sounds
If you see this on your screen, contact your F-Secure distributor
The reference to Bubbleboy and the above link are references to a character in an episode in the TV show "Seinfeld". Although the link shown by the virus appears to be broken, it is most likely the same page as https://www.toptown.com/dorms/rick/bblboy.htm
Removal
Based on the settings of your F-Secure security product, it will either move the file to the quarantine where it cannot spread or cause harm, or remove it.
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
This page and it's maintainer have nothing to do with the worm.The receiver of the email gets infected and spreads the worm without clicking any attachment. The message does not even have any attachments.When user receives such an email and opens it, the worm attempts to create two files, "C:\WINDOWS\START MENU\PROGRAMS\STARTUP\UPDATE.HTA" and "C:\WINDOWS\MENU INDICIO\PROGRAMS\INICIO\UPDATE.HTA".These locations specify the Windows startup directory for both English and Spanish versions.After creating this file the worm will perform no further action until the system has been restarted.Then the worm will use ActiveX feature to access the system registry.
It modifies the Windows registered owner to "BubbleBoy" and organization to "Vandelay Industries".
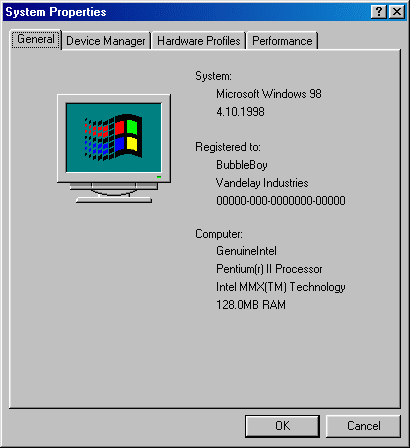
Then the worm uses ActiveX features to open Outlook and uses it to send itself to all recipients in all address books, like the Melissa virus does.It also adds a key to the registry to mark that emails has been sent:
HKEY_LOCAL_MACHINE\Software\OUTLOOK.BubbleBoy
and sets its value to:
OUTLOOK.BubbleBoy 1.0 by Zulu
The mass mailing is done only once per infected machine.Next, the worm will show a message box with the following text:
System error, delete "UPDATE.HTA" from the startup folder to solve the problem.
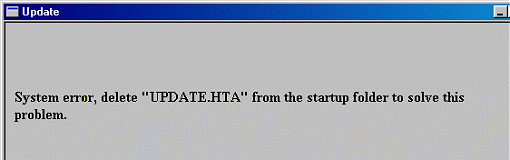
When this message appears to the user, the infected emails has been sent to all recipients already.Currently there are two known variants of this worm. The second one is encrypted.Bubbleboy is able to spread only under Microsoft Outlook 98, Outlook 2000 and Outlook Express that comes with Internet Explorer 5. It does not replicate under Windows NT - instead it just fails without error messages.Bubbleboy uses a known security hole in Microsoft Outlook to create the local HTA file.If active scripting is disabled from Outlook, the worm will not work.Microsoft has more information on this problem available at:
https://www.microsoft.com/technet/security/bulletin/fq99-032.asp
They also have a patch to fix this problem at:
https://www.microsoft.com/technet/security/bulletin/ms99-032.asp
Variant:BubbleBoy.C
This variant is similar to VBS/BubbleBoy.A.The message that this variant sends looks like this:
From: (name of infected user) Subject: From Your Friend... Body: Message From Your Friend... http://www.towns.com/dorms/tom/friends.htm
The marker in the registry is different. The marker in this variant is:
HKEY_LOCAL_MACHINE\Software\OUTLOOK.Friends
and its value is set to:
OUTLOOK.Friends 1.0 by Wh0
This variant drops a "C:\WINDOWS\FONTS.VBS" file, modifies the settings of the mIRC application and then executes mIRC to send this VBS file. This will work only if mIRC is installed to "C:\MIRC" or "C:\PROGRAM FILES\MIRC" directory.Then the worm will open a hidden MS-DOS session and will attempt to delete all files from the current directory. Usually this is the Windows directory.Finally the worm will drop a small binary file, "C:\PrettyIRC.COM". VBS/BubbleBoy.C compiles this file (using the debugger) from a previously dropped source file "C:\WINDOWS\START MENU\PROGRAMS\STARTUP\UPDATE.SCR". This program is supposed to format the hard drive, but it does not work due to a bug.