Brador
Summary
Brador is the first known backdoor for the Pocket PC hand-held devices.
When run, the backdoor copies itself to startup folder, mails the IP address of the PDA to the backdoor author and starts listening commands on a TCP port. The hacker can then connect back to the PDA via TCP port and control the PDA through the backdoor.
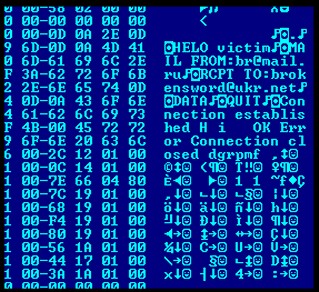
Brador has not been seen in the wild. It only runs on ARM-based Pocket PC devices that have Windows Mobile 2003 (Windows CE 4.2) or later.
Brador is a backdoor, not a virus. It will not spread on it's own.
Removal
Disinfection with Anti-Virus for Pocket PC
Run the F-Secure Anti-Virus for Pocket PC delete infected files and reboot the device.
If you need to do disinfection manually, delete svchost.exe from Windows\StartUp directory with the Pocket PC explorer and reboot the device.
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
Installation to system
When run the Brador will copy itself to Windows\StartUp directory as svchost.exe on the Pocket PC device, so that it will automatically start at each time when device boots.
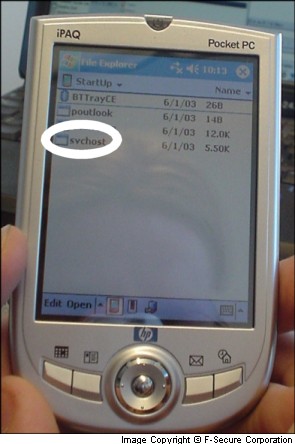
The installation routine makes slight modifications to the file copied to Windows\StartUp directory. So the file will be a bit different at each boot, although this will not affect the operation of the backdoor. It is still unclear whether this is intentional or side effect of the installation routine.
Payload
When the Brador has installed itself into the system it will read the local host IP address and email that to the author.
After emailing it's IP address the backdoor opens a TCP port and start listening commands from it.
The backdoor is capable of uploading and downloading files from PDA, executing arbitrary commands and displaying messages to the PDA user.